|
MAIN PAGE
> Back to contents
Cybernetics and programming
Reference:
Derendyaev D.A., Gatchin Y.A., Bezrukov V.A.
Algorithm for Representation of Residual Risk Mathematical Model
// Cybernetics and programming.
2016. № 4.
P. 81-85.
DOI: 10.7256/2306-4196.2016.4.19655 URL: https://en.nbpublish.com/library_read_article.php?id=19655
Algorithm for Representation of Residual Risk Mathematical Model
Derendyaev Denis Aleksandrovich
post-graduate student of the Department of Computer Systems Design and Safety at Saint Petersburg National Research University of Information Technologies, Mechanics and Optics
197101, Russia, Saint Petersburg, str. Kronverkskii Prospekt, 49

|
battelnet.net@mail.ru
|
|
 |
Other publications by this author
|
|
Gatchin Yurii Armenakovich
Doctor of Technical Science
professor of the Computing System Design and Safety at Saint Petersburg National Research University of Information Technologies, Mechanics and Optics
197101, Russia, Saint Petersburg, str. Kronverkskii Prospekt, 49

|
gatchin@mail.ifmo.ru
|
|
 |
Other publications by this author
|
|
|
Bezrukov Vyacheslav Alekseevich
PhD in Technical Science
associate professor of the Department of Computer Systems Design and Safety at Saint Petersburg National Research University of Information Technologies, Mechanics and Optics
197101, Russia, Saint Petersburg, str. Kronverkskii Prospekt, 49

|
bezrukov@mail.ifmo.ru
|
|
 |
Other publications by this author
|
|
|
DOI: 10.7256/2306-4196.2016.4.19655
Received:
05-07-2016
Published:
26-08-2016
Abstract:
The majority of modern risk evaluation and management methods imply the concept of residual risk as a figure describing the risk of a threat after all countermeasures have been implemented, however, researchers do not pay enough attention thereto. In this research the authors offer their algorithm allowing to represent the residual risk of information security threats in a form of a mathematical model which in its turn creates opportunities for a more detailed analysis of a parameter under review and the model itself. Coefficients of this model demonstrate the impact of input parameters on the final result. The algorithm of the residual risk mathematical model is based on a complete factorial experiment taking into account peculiarities of a parameter under review. This approach allows to analyze the role of residual risk not only as a figure but also mathematical model which can help to better imply residual risk when implementing risk evaluation and management methods in order to improve an information protection system at an enterprise.
Keywords:
risk evaluation methods, durability of protection mechanisms, risk of a threat, model coefficient, complete factorial experiment, algorithm, information security threats, information protection system, mathematical model, residual risk
This article written in Russian. You can find original text of the article here
.
Введение С каждым годом информационные технологии развиваются всё больше, а вопрос об обеспечении их безопасности становится всё актуальнее, что в свою очередь требует более совершенных технологий по управлению рисками угроз информационной безопасности. Разработано большое количество зарубежных и отечественных стандартов, описывающих информационную безопасность в целом и управление рисками в частности. К ним относятся ISO 15408, ISO 17799, ISO 27001, BSI, ГОСТ ИСО/МЭК 17799 и ГОСТ ИСО/МЭК 27001, британский стандарт BS 7799 и т.д.
Управление рисками строится на их оценки, которая включает в себя анализ и оценивание. Существуют различные методы направленные на поиск оптимального значения оценки рисков информационной безопасности и их анализа: метод нечёткой кластеризации и вычисления взаимной информации[1], матричный подход[2], нечёткий всесторонний метод[3], на основе предикатов и логического вывода[4] и т.д.
Результатом оценки риска после внедрения мер противодействия угрозе информационной безопасности является значение остаточного риска. Большинство современных методик используют остаточный риск как числовой показатель, который по результатам проведенных мер противодействия должен входить в заранее определенный доверительный интервал , устраивающий конкретную компанию. Остаточный риск расчитывается по формуле `R_(ost)=R*(1-m) ` , где `R` - риск угрозы, `m` - прочность механизмов защиты и представляет из себя остающийся, потенциальный риск после применения всех контрмер[5], он является важным показателем качества механизмов противодействия и как следствие играет важную роль в управлении рисками информационной безопасности, что делает вопрос математического описания остаточных рисков актуальным.
Целью данной работы является представление алгоритма получения математического описания остаточного риска. Алгоритм получения математической модели остаточного риска 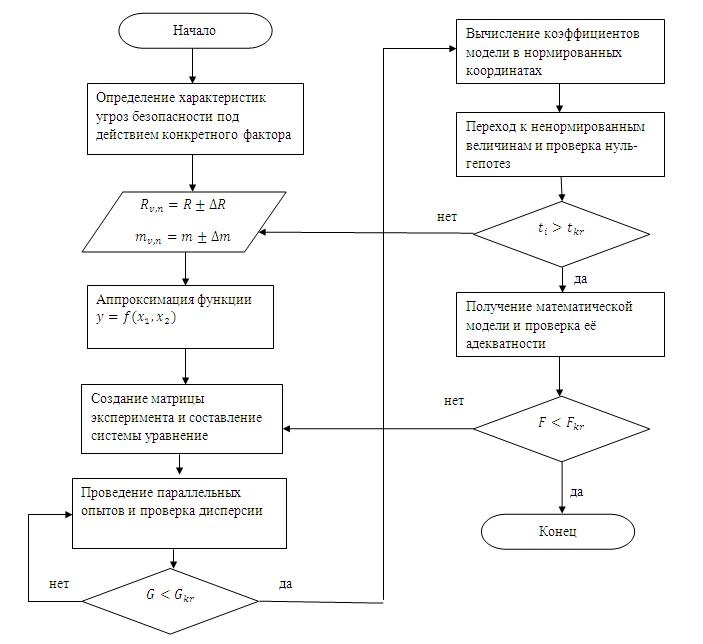
Рис.1 Алгоритм получения математической модели остаточного риска
Алгоритм строится на базе полного факторного эксперимента [6,7].
Для начала нам необходимо определить характеристики угрозы безопасности, такие как вероятность и критичность. Зная данные характеристики можно вычислить значение риска угрозы `R=P*Z` ` ` , где `P` ` ` - вероятность а `Z` ` ` - критичность угрозы. Доверительный интервал для входных параметров алгоритма: риск угрозы `deltaR` ,прочность механизмов защиты `deltam` , может варьироваться от 10% до 30% от значения входного параметра. Аппроксимация представляет собой замену нашей функции остаточного риска от двух переменных другой, при этом замена может происходить различными вариантами:`y=a_(0)+a_(1)*x_(1)+a_(2)*x_(2) `, `y=a_(0)+a_(1)*x_(1)+a_(2)*x_(2)+a_(12)*x_(1)*x_(2)`, `y=a_(0)+a_(1)*x_(1)+a_(2)*x_(2)+a_(3)*x_(1)^(2)` и тд. Нахождение всех коэффициентов является основной задачей в ходе получения математической модели, которые покажут, на сколько каждый из входных параметров влияет на результат. В матрице эксперимента количество столбцов равно числу коэффициентов функции, а количество строк определяется по формуле `N=2^(n)` , где `n` ` ` - число входных параметров. На основе матрицы эксперимента составляется система уравнений, которая используется для расчета коэффициентов. Проведение параллельных опытов используется для получения более точного результата.
В алгоритме присутствуют три условия, которые должны быть соблюдены при проведении расчетов: проверка однородности оценок дисперсии по критерию Кохрэна `G<G_(kr)` ` ` , проверка нуль гипотез для коэффициентов модели с помощью критерия Стьюдента `t>t_(kr)` ` ` и проверка адекватности самой математической модели по критерию Фишера `F<F_(kr)` ` ` . Если хоть одно условие не выполняется, то необходимо перейти к предыдущим шагам алгоритма для внесения изменений. Пример использования алгоритма Рассмотрим произвольную угрозу информационной безопасности, для которой: `P=0,38, Z=53, m=0,8, R=0,38*53=20, deltaR=2, deltam=0,1`
Проведем аппроксимацию нашей функции `y=f(x_(1),x_(2))` линейной`y=a_(0)+a_(1)*x_(1)+a_(2)*x_(2)` .
Матрицу эксперимента представим в виде таблицы. Среднее значение итогового результата образуется из за вероятности преодоления механизмов защиты, которое принимает значенияе не более 1% , в результате чего нам необходимо провести параллельные опыты и усреднить полученные значения. Столбоц `x_(0)` добавлен для возможности расчета коэффициента`a_(0)`. Дисперсия определяется по формуле:` S_(i)^(2)=(1)/(1-n)*sum_(i=1)^n (y_(i) - << y>>)^(2)`, где `n` - число параллельных опытов.
Таблица 1. Эксперимент
| № |
`x_(0)`
|
`x_(1)`
|
`x_(2)`
|
`y_(1)`
|
`y_(2)`
|
`y_(3)`
|
`<< y>>` |
`S^(2)` |
| 1 |
1 |
18 |
0,7 |
5,5 |
5,41 |
5,43 |
5,45 |
0,012 |
| 2 |
1 |
18 |
0,9 |
1,92 |
1,89 |
1,95 |
1,92 |
0,004 |
| 3 |
1 |
22 |
0,7 |
6,7 |
6,65 |
6,75 |
6,7 |
0,01 |
| 4 |
1 |
22 |
0,9 |
2,3 |
2,34 |
2,37 |
2,34 |
0,005 |
Далее нам необходимо перейти к нормированным значениям для упрощения расчета коэфициентов. При переходе верхние значения параметров приравниваются к 1, а нижние к -1.
Таблица 2. Нормированные величины
| № |
` ` `barx_(0)`
|
`barx_(1) `
|
`barx_(2) `
|
`<< y>>` |
| 1 |
1 |
-1 |
-1 |
5,45 |
| 2 |
1 |
-1 |
1 |
1,92 |
| 3 |
1 |
1 |
-1 |
6,7 |
| 4 |
1 |
1 |
1 |
2,34 |
Расчитываем коэффициенты математической модели при нормированных значениях по следующей формуле `bara_(g)=1/N*sum_(i=1)^N <<y_(i)>>*barx_(gi)` , где индекс `g` указывает номер столбца, индекс `i` - номер строки. После чего необходимо вернуться к ненормированным значениям:`a_(0)=bara_(0)-bara_(1)*(x_(v1)+x_(n1))/(x_(v1)-x_(n1))-bara_(2)*(x_(v2)+x_(n2))/(x_(v2)-x_(n2))` , `a_(1)=(2*bara_(1))/(x_(v1)-x_(n1))` , `a_(2)=(2*bara_(2))/(x_(v2)-x_(n2))` , где `x_(v)` и `x_(n)` верхнее и нижнее значение входных параметров.
В результате расчетов получилась следующая математическая модель: `y=-3,9+0,2*x_(1)+20*x_(2)`
При расчетах все условия проверки алгоритма были соблюдены, что говорит об адекватности расчитанных коэффициентов и самой математической содели. Заключение В результате использования алгоритма мы получаем линейную функцию остаточного риска`R_(ost)=-3,9+0,2*x_(1)+20*x_(2)` с рассчитанными коэффициентами, которые показывают насколько сильно каждый параметр оказывает влияние на итоговый результат. Рассмотренный в работе алгоритм позволяет представить значение осаточного риска для любой угрозы информационной безопаснсоти в виде математической модели, что можно использовать для улучшения качества системы защиты информации, с учетом рассмотрения остаточного риска не только как числового показателя, но и как математическую функцию.
References
1. Kozlova E. A. Otsenka riskov informatsionnoi bezopasnosti s pomoshch'yu metoda nechetkoi klasterizatsii i vychisleniya vzaimnoi informatsii / E.A. Kozlova // Molodoi uchenyi. — 2013. — №5. — S. 154-161.
2. Goel S. Information security risk analysis – a matrix-based approach [Elektronnyi resurs] / S. Goel, V. Chen // SUNY. – University at Albany. – 2005. URL: http://www.albany.edu/~goel/publications/goelchen2005.pdf (data obrashcheniya: 16.06.2016 )
3. Lee M.C. Information Security Risk Analysis Methods and Research Trends: AHP and Fuzzy Comprehensive Method [Elektronnyi resurs] / M.C.Lee // IJCSIT. – Vol 6. – No1. – 2014. URL: http://www.airccse.org/journal/jcsit/6114ijcsit03.pdf (data obrashcheniya: 14.06.2016 )
4. Tenetko M.I. Analiz riskov informatsionnoi bezopasnosti / M.I. Tenetko, O.Yu. Peskova //Izvestiya YuFU. Tekhnicheskie nauki. – 2011. – №12. – S.49-57.
5. Varfolomeev A.A. Upravlenie informatsionnymi riskami: ucheb. posobie / A.A. Varfolomeev. – M.: RUDN, 2008. – 158 s.
6. Matematicheskoe modelirovanie avtomatizirovannykh sistem kontrolya i upravleniya: Metod. ukazaniya / Avt.-sost. A.Yu. Senkevich. Tambov: Izd-vo Tamb. gos. tekhn. un-ta, 2004. 44 s.
7. Korobeinikov A.G., Grishentsev A.Yu., Kutuzov I.M., Pirozhnikova O.I., Sokolov K.O., Litvinov D.Yu. Razrabotka matematicheskoi i imitatsionnoi modelei dlya rascheta otsenki zashchishchennosti ob''ekta informatizatsii ot nesanktsionirovannogo fizicheskogo proniknoveniya // Kibernetika i programmirovanie. - 2014. - 5. - C. 14 - 25. DOI: 10.7256/2306-4196.2014.5.12889. URL: http://www.e-notabene.ru/kp/article_12889.html
Link to this article
You can simply select and copy link from below text field.
|
|





