MAIN PAGE
> Back to contents
Cybernetics and programming
Reference:
Polyanichko M.A.
Using technical indicators to identify insider threats
// Cybernetics and programming.
2018. № 6.
P. 40-47.
DOI: 10.25136/2644-5522.2018.6.27970 URL: https://en.nbpublish.com/library_read_article.php?id=27970
Using technical indicators to identify insider threats
Polyanichko Mark Aleksandrovich
PhD in Technical Science
Associate Professor, Department of Computer Science and Information Security, Emperor Alexander I St. Petersburg State University of Communications
190031, Russia, Sankt-Peterburg oblast', g. Saint Petersburg, ul. Moskovskii, 9

|
polyanichko@pgups.ru
|
|
 |
Other publications by this author
|
|
|
DOI: 10.25136/2644-5522.2018.6.27970
Received:
10-11-2018
Published:
15-01-2019
Abstract:
Detecting insider threats and countering them is a complex task faced by information security experts in both the commercial sector and government organizations. Modern organizations depend on information technology and their information assets, which makes the problem of confronting insiders all the more urgent. Identification of insiders can be carried out by introducing a complex of both technical and organizational measures. The article proposes the use of data from the work logs of information protection software and other monitoring tools to identify insider threats and highlights a set of indicators indicating the presence of suspicious employee actions. The set of technical indicators (indicators) proposed in the article can be used to build a system of logical rules or fuzzy inference rules that allow identifying insiders in an organization. The introduction of mechanisms for analyzing the proposed indicators will improve the efficiency of the information security administrator and will help prevent incidents related to the implementation of insider threats.
Keywords:
internal threats, information security, insider, insider detection, indicator, information security tools, monitoring, insider threats, suspicious actions, staff
This article written in Russian. You can find original text of the article here
.
Инсайдерские угрозы является одной из самых больших проблем информационной защиты, так как они выходят на передний план на фоне совершенствования криптографических методов, аппаратных и программных средств защиты информации. Данные угрозы сложно поддаются анализу в силу непредсказуемости человеческого поведения и не могут быть нивелированы полностью. Тем не менее, применение совокупности организационных, профилактических и технических мер может существенно снизить риск данных угроз. Обеспечение информационной безопасности от инсайдерских угроз требует совершенствования как программных средств защиты информации, так и решения организационных проблем и внедрения процессов управления информационной безопасностью, ориентированных на инсайдерские угрозы. Традиционные методы защиты и более совершенная защита от устойчивых продвинутых угроз (advanced persistent threat) на основе сбора данных неэффективны против инсайдеров-злоумышленников [3]. В контексте данного исследования, инсайдер – это работник организации (как действующие, так и уволенные), деловые партнеры и подрядчики, имеющие доступ к информационным активам и системам организации или располагающие знаниями об используемых в организации методах и средствах обеспечения безопасности, которому предоставлены определённые права доступа. Подразумевается, что такие пользователи могут злоупотреблять своими привилегиями и, таким образом, нарушить конфиденциальность и целостность данных. Также допускается, что «пользователем» может быть какой-то компьютерный объект – процесс, агент или система – предположительно, но совсем необязательно, действующий от имени конкретных пользователей. Инсайдеры представляют большую опасность для организации, так как могут продолжительное время действовать незаметно, совершать акты мошенничества, красть конфиденциальную информацию и интеллектуальную собственность или нарушать работу информационных систем. Статистика показывает, что число инцидентов информационной безопасности, связанных с действиями инсайдеров растет [1, 5], а внедрение корпоративных информационных систем [6], мобильных приложений, мессенджеров, социальных сетей и облачных систем хранения данных в рабочие процессы современных организаций открывают новые возможности для реализации внутренних угроз информационной безопасности.
Современные программные средства защиты информации, как правило, ориентированы на защиту информационных активов и редко на обнаружение аномалий в поведении работников [4, 10]. Тем не менее, системы управления информационной безопасностью и другие программные средства обеспечения информационной безопасности могут быть использованы для выявления инсайдерских угроз [11, 12].
Имеются различные показатели, получаемые из систем журналирования программных средств защиты информации, которые могут быть использованы для обнаружения инсайдерских действий [9]. К ним относятся данные об аутентификации, изменении данных, сетевой активности, получении доступа к ресурсам, активности вредоносного программного обеспечения и системных ошибках. Для обнаружения подозрительной активности администраторы информационной безопасности могут использовать следующие программные средства защиты информации в качестве источников информации:
- SIEM-системы: решения, которые осуществляют мониторинг информационных систем, анализируют события безопасности в реальном времени, исходящие от сетевых устройств, средств защиты информации, ИТ-сервисов, инфраструктуры систем и приложений [14]. Входной информацией для SIEM-систем может служить практически любая информация.
- Средства управления доступом и аутентификации: применяются для управления и мониторинга доступа к информационным системам и использования привилегий.
- DLP-системы: сведения о попытках инсайдерских утечек, нарушении прав доступа.
- IDS/IPS-системы: несут данные о сетевых атаках, изменениях конфигурации и доступа к устройствам.
- Антивирусные приложения: генерируют события о работоспособности ПО, базах данных, изменении конфигураций и политик, вредоносном коде.
- Журналы событий серверов и рабочих станций: применяются для контроля доступа, обеспечения непрерывности, соблюдения политик информационной безопасности.
- Межсетевые экраны: сведения об атаках, вредоносном программном обеспечении и прочих угрозах информационной безопасности.
- Сетевое активное оборудование: используется для контроля доступа, учета сетевого трафика.
- Сканеры уязвимостей: данные об инвентаризации активов, сервисов, программного обеспечения, уязвимостей, поставка инвентаризационных данных и топологической структуры.
- Системы инвентаризации и asset-management: поставляют данные для контроля активов в инфраструктуре и выявления новых.
- Системы веб-фильтрации. Предоставляют данные о посещении сотрудниками подозрительных или запрещенных веб-сайтов.
Исходя из вышесказанного, в качестве технических индикаторов (количественных и качественных), которые могут указывать на наличие инсайдерской угрозы могут быть использованы [2] индикаторы, связанные со следующими событиями:
1. Печать документов
- Увеличение количества выводимых на печать документов
- Выполнение печати в нерабочее время
- Удаленная печать
- Печать документов, запрещенных для копирования
- Печать больших документов
2. Поисковые запросы
- Увеличение количества запросов
- Осуществление поиска в нерабочее время
- Запросы из черного списка
- Прямой доступ к базе данных
- Запросы на странные темы
- Высокое количество уникальных запросов
3. Осуществление доступа
- Высокое использование одного IP адреса для доступа
- Доступ в нерабочее время
- Доступ к запрещенным ресурсам
- Попытки получения администраторского доступа
4. Скачивание информации
- Увеличение количества скачиваемой информации
- Скачивание информации в нерабочее время
- Скачивание с удаленных серверов
- Скачивание документов, запрещенных для копирования
- Скачивание больших файлов
5. Использование браузера
- Частое обращение к одному и тому же ресурсу
- Использование браузера в нерабочее время
- Просмотр запрещенных ресурсов
- Просмотр большого количества документов
Для формирования значений приведенных показателей предлагается использовать математический аппарат нечетких множеств и лингвистические переменные, так как они позволяют оперировать непрерывно изменяющимися во времени динамическими входными данными, перейти к единой качественной шкале измерений и проводить качественную оценку как входных данных, так и выходных результатов. Лингвистическая переменная – в теории нечётких множеств, это переменная, которая может принимать значения фраз из естественного или искусственного языка [7, 13].
Лингвистической переменной называется набор [8]:
|
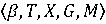 , ,
|
|
|
где
|
b – имя лингвистической переменной,
|
|
|
Т – множество значений, которые представляют собой имена нечетких переменных, областью определения каждой переменной является множество X;
|
|
|
G – синтаксическая процедура, позволяющая оперировать элементами терм-множества T и создавать новые термы (значения). Множество 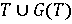 , где G(T) ‑ множество полученных термов, называется расширенным терм-множеством лингвистической переменной; , где G(T) ‑ множество полученных термов, называется расширенным терм-множеством лингвистической переменной;
|
|
|
М – математическое правило, определяющее класс функции принадлежности для значений из множества T.
|
| |
|
|
Для описания лингвистических переменных предлагается использовать функции принадлежности L-класса, p-класса, S-класса, t-класса и g-класса [8].
|
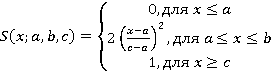 , ,
|
|
|
где
|
S(x;a,b,c) – функция принадлежности S-класса;
|
| |
|
|
Функция S-класса применяется в случае, если возрастание какого-то показателя увеличивает его функцию принадлежности к множеству.
|
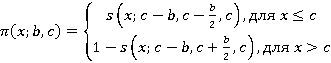 , ,
|
|
|
где
|
p(x;b,c) – функция принадлежности p-класса;
|
| |
|
|
Функция p-класса применима в том случае, если изменение значения показателя сначала увеличивает значение функции принадлежности, а затем его уменьшает.
|
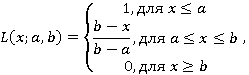
|
|
|
где
|
L(x;a,b) – функция принадлежностиL-класса;
|
| |
|
|
ФункцияL-класса применяется, если значение функции принадлежности не информативно в каком-то диапазоне значения показателя.
|
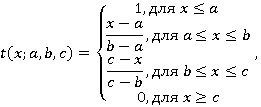
|
|
|
где
|
t(x;a,b,c) – функция принадлежности t-класса;
|
| |
|
|
В некоторых случаях, функция принадлежности класса t может быть альтернативой по отношению к функции класса p.
|
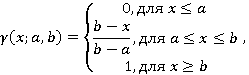
|
|
|
где
|
g(x;a,b) – функция принадлежности g-класса;
|
| |
|
|
Ниже рассмотрены примеры технических показателей выявления инсайдерских угроз. На рисунке 1 изображена лингвистическая переменная «PrintBursts», характеризующая увеличение количества документов, выводимых на печать. Технический показатель увеличения объема печати описывается тремя термами «low», «medium» и «high». Данный показатель измеряется в процентах, относительно среднего объема печати данного сотрудника за предыдущий период. В случае, если количество выводимых на печать документов увеличилось до 25%, то считается, что происходит небольшое увеличение печати, которое не имеет большой смысл относить к подозрительному поведению. Увеличение свыше 50%, то есть более чем в полтора раза считается подозрительным. Средний диапазон считается областью среднего риска и решение о необходимости дополнительного анализа поведения остается за администратором безопасности.
|
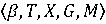 , ,
|
|
|
где
|
b = «PrintBursts»,
|
|
|
Т = {«low», «medium», «high»};
|
|
|
X = [0,100]
|
|
|
G = {Æ};
|
|
|
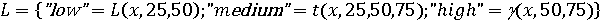 . .
|
| |
|
|
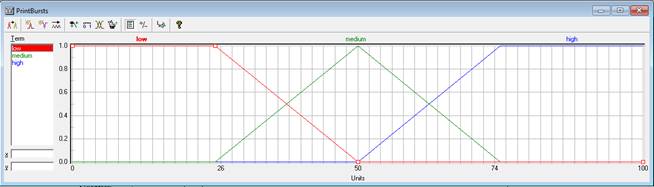
Рисунок 1 – Лингвистическая переменная «PrintBursts»
На рисунке 2 изображен график лингвистической переменной «PrintSusTiming». Технический показатель выполнения печати в нерабочее время описывается тремя термами «low», «medium» и «high». Данный показатель измеряется в часах, прошедших относительно окончания официального рабочего времени. В работе при создании переменной использовался стандартный восьмичасовой рабочий день (с 8.30 до 17.30). В случае, если сотрудник выполняет печать в течение трех часов с момента окончания рабочего дня, то такое поведение слабо относится к подозрительному, так как задержки на работе являются распространённым явлением. Самым подозрительным временем печати является ночное время, то есть спустя 12-14 часов после окончания рабочего дня. При этом по мере приближения времени к началу следующего рабочего дня значение показателя снижается, так как сотрудники часто приезжают на работу немного заранее.
|
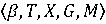 , ,
|
|
|
где
|
b = «PrintSusTiming»,
|
|
|
Т = {«low», «medium», «high»};
|
|
|
X = [0,16]
|
|
|
G = {Æ};
|
|
|
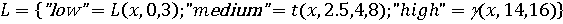 . .
|
| |
|
|
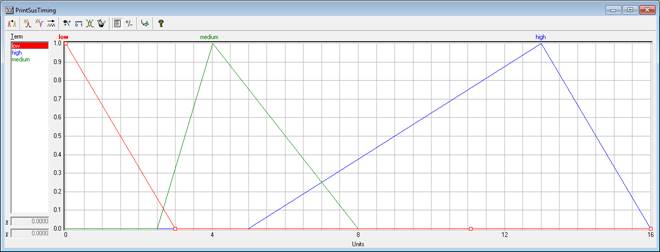
Рисунок 2 – Лингвистическая переменная «PrintSusTiming»
На рисунке 3 изображен график лингвистической переменной «QueryHighDistCnt». Технический показатель наличия поисковых запросов на странные темы описывается двумя термами «low» и «high». Данный показатель измеряется в процентах, относительно среднего объема запросов, выполняемых пользователем. В случае, если объем уникальных запросов от общего объема запросов не превышает 25%, то относить данный факт к подозрительному поведению не имеет смысла. Возрастание количества уникальных запросов до 30% и выше может свидетельствовать о том, что пользователь собирает информацию компании или компьютер пользователя заражен вредоносным программным обеспечением, которое выполняет автоматизированный поиск.
|
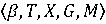 , ,
|
|
|
где
|
b = «QueryHighDistCnt»,
|
|
|
Т = {«low», «high»};
|
|
|
X = [0,100]
|
|
|
G = {Æ};
|
|
|
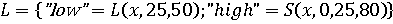 . .
|
| |
|
|
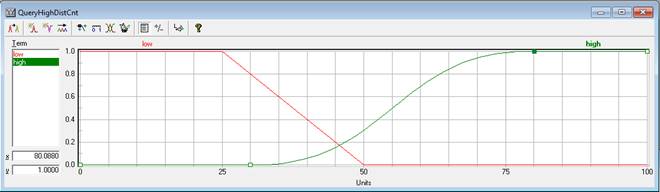
Рисунок 3 – Лингвистическая переменная «QueryHighDistCnt»
Анализ данных показателей может выявить потенциально опасные инсайдерские действия, такие как осуществление доступа в нерабочее время, печать или скачивание больших объемов информации, обращение к информации, не требуемой для выполнения должностных обязанностей и д.р.
Заключение
Предложенный набор технических индикаторов (показателей) может быть использован для построения системы логических правил или правил нечеткого вывода, позволяющих осуществлять выявление инсайдеров в организации. Внедрение механизмов анализа предложенных индикаторов позволит повысить эффективность работы администратора информационной безопасности и позволит предотвращать инциденты, связанные с реализацией инсайдерских угроз и уменьшить время, требуемое для выявления их наличия.
References
1. Insider Threat Report: 2018 - CA Technologies // CA Technologies URL: https://www.ca.com/content/dam/ca/us/files/ebook/insider-threat-report.pdf (data obrashcheniya: 18.07.2018).
2. Kauh J. [i dr.]. Indicator-based behavior ontology for detecting insider threats in network systems // KSII Transactions on Internet and Information Systems. 2017. № 10 (11). C. 5062–5079.
3. Smith J.A., Holloway R. Mitigating cyber threat from malicious insiders 2014. C. 1–8.
4. Thomas Georg, Patrick D., Meier M. Ethical issues of user behavioral analysis through machine learning // Journal of Information System Security. 2017. № 1 (13). C. 3–17.
5. Verizon 2015 Data Breach Investigations Report // Information Security. 2015. C. 1–70.
6. Anikin I.V. Upravlenie vnutrennimi riskami informatsionnoi bezopasnosti korporativnykh informatsionnykh setei // Nauchno-tekhnicheskie vedomosti SPbGPU. Informatika. Telekommunikatsii. Upravlenie. 2009. №3 (80).
7. Zade L. Ponyatie lingvisticheskoi peremennoi i ego primenenie k prinyatiyu priblizhennykh reshenii. — M.: Mir, 1976.
8. Kofman A. Vvedenie v teoriyu nechetkikh mnozhestv. — M.: Radio i svyaz', 1982. — 432 c.
9. Polyanichko M.A., Korolev A.I. Podkhod k vyyavleniyu insaiderskikh ugroz v organizatsii // Estestvennye i tekhnicheskie nauki. 2018. - №9., Vypusk (123). - 2018 - s. 152 - 154.
10. Polyanichko M.A. Sovremennoe sostoyanie metodov obnaruzheniya i protivodeistviya insaiderskim ugrozam informatsionnoi bezopasnosti // Colloquium-Journal. 2018. № 9–1 (20). C. 44–46.
11. Polyanichko M.A., Punanova K.V. Osnovnye problemy prakticheskogo primeneniya cheloveko-orientirovannogo podkhoda k obespecheniyu informatsionnoi bezopasnosti // «Fundamental'nye i prikladnye razrabotki v oblasti tekhnicheskikh i fiziko-matematicheskikh nauk» Sbornik nauchnykh statei po itogam raboty tret'ego mezhdunarodnogo kruglogo stola. - M.: Obshchestvo s ogranichennoi otvetstvennost'yu «KONVERT». 2018. C. 57–60.
12. Polyanichko M.A. Osnovnye mery protivodeistviya insaiderskim ugrozam informatsionnoi bezopasnosti // «Fundamental'nye i prikladnye razrabotki v oblasti tekhnicheskikh i fiziko-matematicheskikh nauk» Sbornik nauchnykh statei po itogam raboty tret'ego mezhdunarodnogo kruglogo stola. - M.: Obshchestvo s ogranichennoi otvetstvennost'yu «KONVERT». 2018. C. 43–46.
13. Rutkovskaya D., Pilin'skii M., Rutkovskii L. Neironnye seti, geneticheskie algoritmy i nechetkie sistemy: Per. s pol'sk. I.D. Rudinskogo, Tom 452. — Moskva: Goryachaya liniya-Telekom, 2006.
14. Chto takoe SIEM - sistemy i dlya chego oni nuzhny? // ANTI - MALWARE [Elektronnyi resurs]. URL: https://www.anti-malware.ru/analytics/Technology_Analysis/Popular-SIEM-Starter-Use- Cases (data obrashcheniya: 25.07.2018).
Link to this article
You can simply select and copy link from below text field.
|





