|
DOI: 10.7256/2306-4196.2016.4.19516
Received:
19-06-2016
Published:
26-08-2016
Abstract:
The subject of the research is the analysis of SDN network safety methods. One of such safety methods is the analysis of the current network configuration for a fast determination of changes and upkeep of the authorized status. Today SDN networks are gaining popularity therefore development of protection algorithms for such networks is a necessary step. SDN network approach to data transfer differs from that of traditional networks. Based on that fact, an important research goalo is either to define drawbacks of exisiting algorithms applicable to such networks or to develop new ones. Research goals include analysis of existing algorithms, search for solutions and adaptation of these solutions to initial tasks or development of a new solution. As a result of the research, the author describes a device that would ensure security of SDN network at the level of data transfer disregarding external factors. This would alllow to provide an independent evaluation of network security. When the network is being re-configured, all changes will be automatic or semi-automatic, thus they will not distort the authorized status of the network.
Keywords:
SDN, network, security, network topology, network analysys, network security, Unified Threat Management, network modeling, SDN security device, network configuration
This article written in Russian. You can find original text of the article here
.
Безопасность SDN сети Сегодня, использование информационных технологий является одним из ключевых моментов при создании полностью автоматизированных предприятий. При этом для сети отводится очень важная роль. Такие сети должны быть полностью защищены от непредвиденных сбоев или угроз.[2]
SDN сеть — сеть передачи данных, в которой уровень управления сетью отделён от устройств передачи данных и реализуется программно. Ключевые принципы SDN — разделение процессов передачи и управления данными, централизация управления сетью при помощи унифицированных программных средств, виртуализация физических сетевых ресурсов.
Программно-определяемые сети (SDN) благодаря автоматизации рабочих процессов с применением правил обеспечивают ускоренное развертывание и доставку приложений в организациях при значительном сокращении затрат на информационные технологии. Технология программно-определяемых сетей служит платформой для архитектур облачных сред благодаря автоматизированной доставке приложений по запросу и масштабируемой мобильности. Программно-определяемые сети усиливают преимущества виртуализации центров обработки данных, способствуя расширению выбора ресурсов, их экономичному использованию, сокращению затрат на внедрение и эксплуатацию инфраструктуры.
Целью разработки такой технологии как Software Defined Network(SDN или ПКС), является упрощение основных сетевых компонентов, а также, за счет этого, снижение их стоимости и сложности обслуживания. Одними из самых важных моментов является увеличение пропускной способности канала передачи данных и возможность централизованного управления сетью. За счет этого у нас значительно упрощается динамической изменение сети, поскольку всеми изменениями руководит оператор на едином контроллере.
Ключевая идея - это создание специального программного обеспечения, позволяющего отделить управление сетевым оборудованием от уровня передачи данных
В архитектуре SDN различают плоскости данных, управления и приложений(см рис 1). На уровне приложений, напрямую сообщается SDN контроллеру о требованиях к сети и её поведении, при помощи NBI-интефейса. Помимо этого, здесь запрашивается информация от контроллера, позволяющая ему иметь целостный взгляд на сеть в целом.
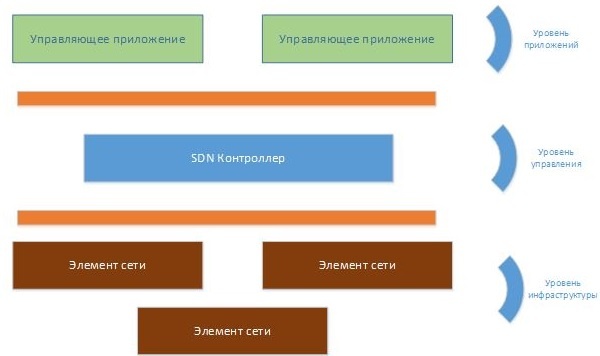
Рисунок 1
Уровень передачи данных состоит из устройств, называемых SDN datapath, которые представляют из себя сетевое устройство, обеспечивающее перенаправление трафика и нескольких функций обработки трафика.
Взаимодействие между SDN-контроллером и SDN Datapath происходит по протоколу OpenFlow [4], поэтому очень часто такие устройства также называют OpenFlow-устройствами или OpenFlow- коммутаторами. SDN-интерфейс между плоскостями управления и данными (CDPI) является интерфейсом, определенным между SDN- контроллером и SDN Datapath. Данный интерфейс должен обеспечивать как минимум следующие возможности:
- Программное управление всеми операциями перенаправления.
- Получение всевозможных статистических отчетов от OpenFlow-коммутаторов.
- Оповещения о событиях.
Предполагается, что CDPI будет реализован открытым, не зависимым от производителя и интероперабельным способом. Протоколом, который обеспечивает взаимодействие плоскости управления и плоскости данных, является протокол OpenFlow.
SDN Northbound интерфейсы (NBI) являются интерфейсами между SDN- приложениями и SDN-контроллерами. Они предоставляют абстрактный взгляд на сеть и непосредственно обеспечивают необходимое сетевое поведение. Они могут быть реализованы на любом уровне абстракции и с различным набором функциональностей.[1]
Рассмотрим проблему изменения конфигурации на примере обычных и SDN сетей. На рисунке 2 представлена возможная схема сети, где взаимодействие серверов 19 и 20, находящихся в одной стойке, будет доступно для видимости серверов 21 и 22 при наличии широковещательных пакетов и отсутствии правильной настройке средств разграничения доступа, таких, как например, vGate.
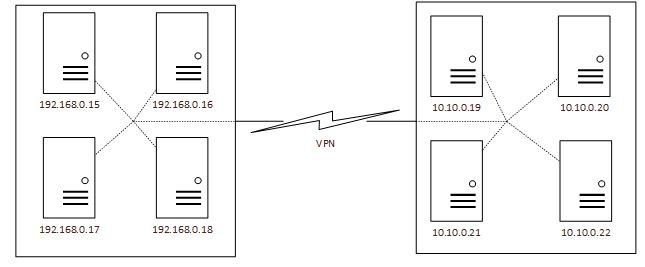
Рисунок 2
Очевидно, обеспечение безопасности не должно ограничиваться лишь установкой специализированного оборудования (брандмауэров или систем для унифицированного управления угрозами — Unified Threat Management, UTM), поскольку оно позволяет защитить только внешний периметр сети. Сеть должна быть устойчива к любым целенаправленным или случайным действиям, совершаемым пользователями внутри сети по невнимательности, из-за незнания внутренних регламентов или умышленного игнорирования сложных и часто запутанных процедур доступа.[3]
В работе практически любой сети неизбежно изменение её топологии или конфигурации. Это может быть: запланированная смена или переконфигурация оборудования, выход оборудование из строя, а также воздействия злоумышленника. При изменении конфигурации топологии сети теряется доверенное состояние, в котором сеть функционировала и мы имеем новую топологию или новую конфигурацию, при которой нам либо известно о произошедших изменения, либо нет.
Имея недоверенное состояние мы не можем гарантировать дальнейшую безопасную работу с сетью, до осуществления повторной проверки на доверенность конфигурации. Таким образом нам необходимо провести оперативную оценку произошедших изменений, для принятия решения, при котором мы сможем продолжить работу с сетью. Это может быть как изменение параметров средств безопасности, так и простое подтверждение о том, что данная топология и конфигурация сети по-прежнему безопасны, для дальнейшего функционирования сети.
Аналогичная ситуация характерна не только для традиционных сетей, но и также для сетей SDN. Рассмотрим подобное взаимодействие на рисунке 3.
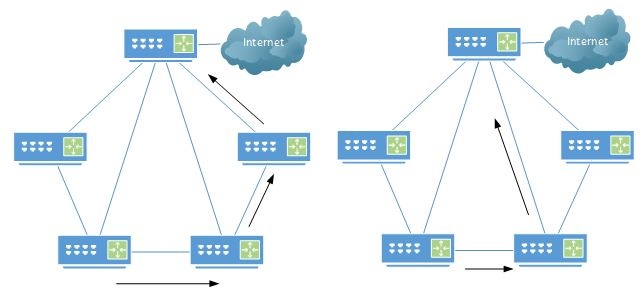
Рисунок 3
Здесь мы видим, что передача данных в SDN сети возможна по нескольким каналам. При выходе их строя одного из маршрутизаторов мы не можем гарантировать, что при переходе на другой канал передачи данных мы можем гарантировать доверенное состояние сети, при котором возможна дальнейшая безопасная работа с сетью.
При использовании средств защиты, нам никто не может гарантировать, что они не имеют своих недостатков, недорабток илибэкдоров, что заставляет администраторов сети использовать только комбинации средств защиты от разных производителей, поскольку несколько независимых источников дают более точную оценку безопасности по одной и той же сети. Имея одни и те же потоки данных, два разных средства должны получить одинаковую итоговую оценку состояния сети.
Для сохранения безопасности SDN сети мы хотим использовать специальный многофункциональный программно-аппаратный комплекс, способный выполнять роли от обычного зеркалирования трафика до ролей систем обнаружения утечек и брандмауэров, в зависимости от загруженной в него функциональности, способной динамически изменяться в небольшие промежутки времени. Данные изменения будут загружаться по специальному порту с сервера безопасности, и после чего автоматически устанавливаться в течении нескольких минут. Устройство устанавливается в разрыв между коммутаторами SDN и способно отслеживать текущую конфигурацию сети. Это устройство предназначено для поддержания доверенного состояния сети.
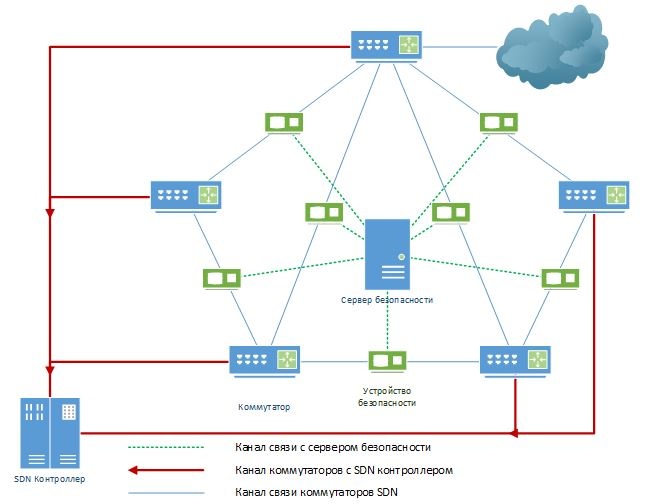
Рисунок 4
Устройства безопасности располагаются между коммутаторами таким образом, что они абсолютно не заметны для основной сети(см рисунок4). они имеют по одному выходу на каждый коммутатор и третий выход для связи с сервером безопасности, который является управляющим для наших устройств безопасности. На нем хранится вся информация о топологии сети и конфигурация каждого устройства безопасности.
В качестве концепта устройства будет использоваться компьютер Raspberry Pi, имеющий 3 ethernet выхода, помещенный в пылевлагозащитный корпус. Unix-подобная операционная система позволит ограничиться только необходимым набором функциональности ОС, и позволит сократить расходы памяти.
Программное обеспечение, устанавливаемое на операционную систему делится на два вида- это управляющие программы и прикладное программное обеспечение по обеспечению защиты сети.
Из управляющих программ выделяются средство определения изменения топологии сети и средство для изменения конфигурации устройства.
Рассмотрим подробнее схему работы средства определения изменения топологии сети представленную на рисунке 5. Средство определения изменения топологии сети Средство выполняет сравнение текущей модели и новой просканированной модели. На основе полученных результатов выдается список изменений состава и/или характеристики сети(в том числе пропускная способность и загруженность канала).
Сравнение выполняется путем сопоставления графов достижимости сети. Поочередно сравниваются состояния узлов(вершин) и линий связи(ребер) графов. В случае, когда находятся различия- новый граф отправляется в БД возможных состояний сети. Далее граф отправляется на АРМ офицера информационной безопасности для дальнейшего рассмотрения.
Если изменений не было обнаружено, работа продолжается в штатном режиме.
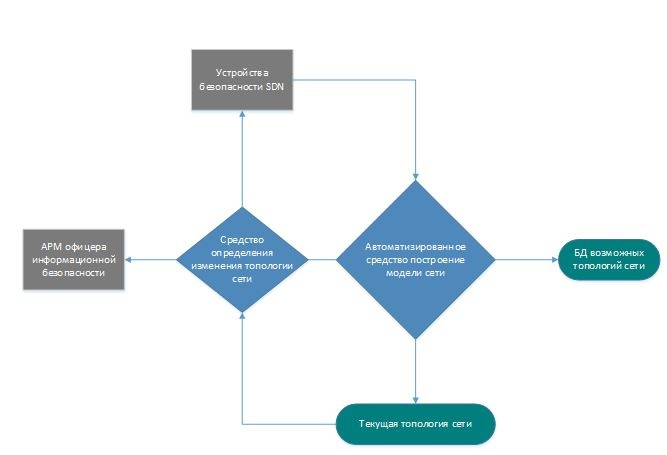
Рисунок 5. Схема работы средства определения изменения топологии сети
Автоматизированное средство построения модели сети
Задачей данного модуля является составление модели сети на основе опроса доступных для данного устройства безопасности SDN узлов.
С устройства посылаем broadcast запрос с обоих портов.
Эти две линии связи будут являться ребром нашего графа, а узлы, которые нам ответили вершинами.
В процессе построения модели выделяем следующие аспекты: достижимость узла, время отклика, пропускная способность, текущая нагрузка.
После составления модели, она передается в средство определения изменения топологии сети.
База данных возможных топологий сети
В базе хранятся все встречаемые ранее состояния топологии сети. В соответствие им идут конфигурации Устройств безопасности SDN.
АРМ офицера информационной безопасности
АРМ офицера информационной безопасности занимается разрешением вопросов о текущей конфигурации Устройств безопасности SDN
После получения нового графа состояния сети, конфигурация устройств возможна в нескольких режимах в зависимости от масштабов изменения графа.
В случае незначительных изменение производится автоматическая переконфигурация или подтверждение того, что изменение конфигурации не требуется.
Если изменения значительные и подобный граф уже встречался, администратор может только подтвердить, что это аналогичный случай и переконфигурирование сети нужно выполнить соответственно.
Если произошли значительные изменения и подобный граф не встречался, то администратор вручную устанавливает новую конфигурацию.
Средство для изменения конфигурации устройства
Задачей данного модуля является получение информации от сервера безопасности SDN, принятие данных прошивки и переконфигурации устройства. При изменении топологии сети, сервер безопасности получает необходимые данные и принимает решение о дальнейших функциональных особенностях каждого модуля. Он высылает необходимые конфигурации устройств безопасности в виде прошивок, которые в дальнейшем будут установлены данным модулем. Вывод Представленное устройство будет способно обеспечить безопасность SDN сети на уровне передачи данных вне зависимости от внешних факторов. В данном случае это позволит предоставить независимую оценку безопасности сети. При переконфигурации сети все необходимые изменения будут происходить в автоматическом или полуавтоматическом режиме, таким образом, что доверенное состояние сети не будет нарушено.
References
1. Pandey S. et al. Ip network topology discovery using snmp //Information Networking, 2009. ICOIN 2009. International Conference on. – IEEE, 2009. – S. 1-5.
2. Nazir F. et al. Constella: a complete IP network topology discovery solution //Managing Next Generation Networks and Services. – Springer Berlin Heidelberg, 2007. – S. 425-436.
3. Harrington D., Wijnen B., Presuhn R. An architecture for describing simple network management protocol (SNMP) management frameworks. – 2002.
4. Li C. S., Liao W. Software defined networks //IEEE Communications Magazine. – 2013. – T. 51. – №. 2. – S. 113-113.
5. Sezer S. et al. Are we ready for SDN? Implementation challenges for software-defined networks //Communications Magazine, IEEE. – 2013. – T. 51. – №. 7. – S. 36-43.
6. Kreutz D., Ramos F., Verissimo P. Towards secure and dependable software-defined networks //Proceedings of the second ACM SIGCOMM workshop on Hot topics in software defined networking. – ACM, 2013. – S. 55-60.
7. Shin S. et al. FRESCO: Modular Composable Security Services for Software-Defined Networks //NDSS. – 2013.
Link to this article
You can simply select and copy link from below text field.
| 




