|
MAIN PAGE
> Back to contents
Legal Studies
Reference:
Belikova K.M.
The role of cryptography in ensuring cybersecurity and protecting information about technologies of strategic and advanced development in the context of protection of sci-tech achievements in the BRICS countries
// Legal Studies.
2021. № 9.
P. 22-62.
DOI: 10.25136/2409-7136.2021.9.36508 URL: https://en.nbpublish.com/library_read_article.php?id=36508
The role of cryptography in ensuring cybersecurity and protecting information about technologies of strategic and advanced development in the context of protection of sci-tech achievements in the BRICS countries
Belikova Ksenia Michailovna
ORCID: 0000-0001-8068-1616
Doctor of Law
Professor of the Department of Entrepreneurial and Corporate Law, Kutafin Moscow State Law University, Professor
125993, Russia, Moscow, Sadovaya-Kudrinskaya str., 9

|
BelikovaKsenia@yandex.ru
|
|
 |
Other publications by this author
|
|
|
DOI: 10.25136/2409-7136.2021.9.36508
Received:
17-09-2021
Published:
24-09-2021
Abstract:
The subject of this research is the role of cryptography in ensuring cybersecurity and protecting information about technologies of strategic and advanced development in the context of protection of sci-tech achievements in the BRICS countries. The relevance of the selected topic is substantiated by the fact that modern countries, for example, the founder of computer industry – the United States along with the BRICS member-states, realize the importance and practical significance of cryptography in different spheres (military, civil) and aim to develop the means and systems of information security, establishing legal regulation for various aspect of its application. Such approach needs elaboration on the development and implementation of cryptography from the perspective of supranational and international law. It is determined that the currently used encryption methods are essentially based on the methods that use special mathematical algorithms built in computer software. Such methods are a substantial but surmountable obstacle for acquiring copyright and patent protection. The examined legal orders evolve by encouraging the development of national cryptographic and software systems, and ensuring its protection by patent law under certain conditions and based on a number of principles that are taken into account in national legislation of the BRICS countries. Correlation of the effectiveness of ensuring information security using only patented encryption or with application of additional protection based on the provisions on commercial secret, demonstrated futility of using the latter. From the perspective of international (or supranational) law, cryptographic software is controlled within the framework of international agreements on distribution of technical data, military and dual-purpose products.
Keywords:
cryptography, encryption, BRICS countries, patent protection, trade secrets, technologies of advanced development, scientific and technical achievements, intellectual property, computer programs, mathematical algorithms
This article written in Russian. You can find original text of the article here
.
“Let intellectual property work in your favour”
Von Seidels. Intellectual property attorneys. Patents, trademarks, designs, copyright [1]
В настоящее время объем создания и распространения информации в мире стабильно возрастает благодаря процессу цифровизации экономики и науки и росту популярности сети интернет. По сути, проникновение компьютеров в различные сферы жизни создало новую отрасль индустрии – информационную, которая в новом тысячелетии - эпохи информационной цивилизации - диктует благополучие и выживание людей за счет средств, предназначенных для обработки информации.
Обусловлено это реализованными за последнее время следующими множественными изменениями, связанными с возможностями современных компьютеров: (1) возросли на порядки и потеряли привязанность к личности объемы и разнообразие форм используемых и обрабатываемых данных; (2) сформирована зависимость контроля материальных (финансовых) ценностей от доступа к информации; (3) получила всеобщее признание зависимость стоимости от содержания информации; (4) исполнителями информационных взаимодействий стали выступать не только люди, но и запрограммированные на это автоматические системы.
В условиях, когда информация и ее содержание приобрели неограниченную значимость, информационная среда общества нуждается сохранении безопасности и защищенности от неправомерных действий, приводящих нанесению ущерба в результате сокрытия или искажения объективной информации.
Практика показывает, что в качестве объектов угроз информации наряду с информационными ресурсами, могут выступать сведения о составе (персонал), состоянии (материальные, финансовые ценности) и деятельности (научная, производственная) различных предприятий, институтов и государственных ведомств.
Именно различные виды нарушения полноты и объективности информации, ее конфиденциальности и доступности могут представлять угрозу не только для таких объектов, но и для общества в целом.
Такие нарушения, как правило, инициируются различными интересантами (конкурентами, соперниками, преступниками и т.д.), преследующими цель прямого материального ущерба путем хищения (ознакомления) или модификации (искажения) информации.
Обычно неправомерное получение информации осуществляется путем или несанкционированного доступа к охраняемым сведениям, или разглашением конфиденциальной информации такими источниками сведений, как люди, технические или бумажные носители информации (документы, публикации), средства осуществления производственной (трудовой) деятельности, ее продукция и отходы. Разнообразие источников охраняемой информации зависит от ее специфики и диктует применение различных средств (физических, аппаратных, программных) и методов (криптографических) для ее защиты, которые сопровождаются целым комплексом научных, технических и организационных мероприятий.
Однако, совокупность этих мероприятий распространяется не только на средства и методы охраны информации, но и на порождающие ее научно-технические и технологические достижения стратегического и опережающего значения в области повышения вычислительных способностей и производительности современных компьютеров, создания искусственного интеллекта, разработки программного обеспечения, развития математического аппарата и др.
С одной стороны, стремительное развитие коммуникаций различного назначения, включая компьютерные сети разного масштаба, нуждается в применении криптографических средств, отличающихся легким доступом и достаточной надежностью, с другой стороны, уже сформированная сетевая структура современных рынков с открытым перетоком научной информации в интернете в режиме он-лайн сотрудничества, но с ограничением доступа к информации стратегического и опережающего значения, требует качественных изменений и перехода научной криптографии на новый уровень информационной безопасности.
Таким образом, в настоящее время криптография стала широко востребованной наукой, а выбор криптографического способа (метода) зависит от требуемого уровня защиты и сферы принадлежности защищаемой информации: от государственной, дипломатической и военной до банковской, коммерческой и др. [2. С. 5-53]
Криптосистемы [3] с математическим обоснованием криптостойкости (на основе таких разделов математики, как общая алгебра, математическая статистика и теорий вероятностей, чисел, алгоритмов и связи в секретных системах) за последние пятьдесят лет эволюционировали от реализуемых с помощью цифровых электронных устройств (компьютеров) блочных шифров и криптографий с открытым ключом или асимметричных (основанных на факторизации больших простых чисел) до вероятностного шифрования, квантовой криптографии и др.
Классическая криптография, использующая математические алгоритмы шифрования (в виде протоколов, состоящих из правил преобразования информации), применяется, например, при передаче информации пользователями по электронной почте, через облачные сервисы или мессенджеры, защищенные одним из криптографических протоколов.
Шифрование для баз данных, файловых систем и хранилищ в цифровом компьютерном виде осуществляется двумя основными способами, называемыми симметричным (например, AES) и асимметричным (самый распространенный - RSA) [4].
При первом способе обменивающиеся данными стороны пользуются для шифровки и дешифровки одним секретным ключом, который неизвестен третьим лицам и не дает доступа им к защищаемой информации.
В асимметричных алгоритмах математической зависимостью связаны открытый и закрытый ключи соответственно для шифрования и дешифровки данных. Система асимметричного шифрования основывается на математическом (правда недоказанном) суждении о недостаточной мощи современных компьютеров для разложения целого числа на простые сомножители за разумное время, то есть предполагается, что для взлома такой системы современному компьютеру не хватит времени, однако такая возможность может появиться в ближайшем будущем у квантовых компьютеров, использующих не только математические алгоритмы, но и законы физики.
Применительно к новым технологиям, по мнению разработчиков шифрования, для лучшей защиты информации в сетях следует использовать одноразовые ключи для дешифровки и безопасной их передачи. Это доступно методу квантовой криптографии, основанному на наблюдении за квантовым состоянием фотонов, задаваемых отправителем и регистрируемых их получателем [5]. Учитывая принцип неопределенности Гейзенберга, невозможность одновременного точного измерения двух квантовых величин и необходимость повышения криптостойкости, было предложено [6. P. 661-663] использовать способность симметричного атома излучать в противоположных направлениях два фотона. Неопределенная поляризация излучаемых симметричных фотонов всегда противоположна, но становится известной при измерении [7. P. 3121-3124], что, в свою очередь, является гарантией безопасности пересылки и хранения ключа вследствие идентичности кодовых последовательностей. При этом попытка перехватить зашифрованную информацию и одноразовый ключ, передаваемый с ней, приводит к ее изменению, невозможности повторного применения ключа и расшифровки [8].
По этим причинам квантовая криптография, основанная на законах квантовой механики и использовании квантовых объектов, считается практически абсолютной защитой зашифрованной информации от взлома. Однако, рынок научного поиска и развития квантовых технологий пока только формируется, поскольку технические воплощения применения квантовой криптографии пока несовершенны и требуют развития. Последним занимаются ученые разных стран – России, Китая, Японии, США и др. [9]
В настоящее время российские ученые добились успехов [10] в развитии квантовой криптографии, повысив эффективность алгоритмов классической постобработки за счет сокращения доли ключа, расходуемой на аутентификацию данных и коррекции ошибок на основе использования полярных кодов.
Следствием улучшения этих алгоритмов стало увеличение скорости генерации ключей и повышение устойчивости устройств для квантового распределения ключей к внешней среде (например, в условиях реальных городских линий связи). способные в перспективе снизить стоимость оборудования.
Российскими учеными также разработан способ повышения уровня защиты систем квантовой криптографии за счет применения особого алгоритма, обнаруживающего атаки на квантовый генератор случайных чисел с помощью протокола, мгновенно оценивающего вклад классических шумов и уровень потенциальной угрозы [11]. Кроме этого, созданный протокол способен преобразовывать случайную битовую последовательность на выходе в «истинно квантовую» без сложных алгоритмов (хэширование) постобработки, обычно применяемых для этих целей [12].
Современные криптографические методы позволяют надежно зашифровывать данные, но с появлением квантовых компьютеров, способных быстро взломать эти шифры, неизбежно возникнет потребность в новых способах шифрования.
Например, уже сейчас исследователи Университетов Саудовской Аравии и Шотландии обеспечили возможность пересылки информации по единовременному каналу связи с помощью созданного ими оптического микрочипа [13]. Последний характеризуется разработчиками как не взламываемая даже квантовыми компьютерами система безопасности, поскольку в ней используются ключи, создаваемые оптическим чипом, не хранящиеся и не передаваемые вместе с сообщением, которые невозможно воссоздать или перехватить. Создатели микрочипа утверждают также, что их способ криптографии в сети занимает меньше места, чем традиционные коммуникации.
Вероятно, применение квантовых компьютеров способно снизить безопасность пользования классическими криптографическими алгоритмами, поскольку алгоритмы с открытым ключом полностью исчерпают свою защитную функцию, а такая функция у симметричных алгоритмов существенно понизится [14]. Такое предположение неоптимистично, но показывает, что в первую очередь требуется исправление алгоритмов, обеспечивающие шифрование с открытым ключом - цифровых подписей, а затем перевести все самые необходимые и важные протоколы на квантово-безопасный уровень – уровень постквантовой криптографии.
Ранее нами исследовались вопросы функционирования беспилотных (летательных, наземных, морских) систем вооружений [15. С. 1-21; 16; 17. P. 671-690; 18. С. 223-234], наиболее опасными из которых признаются беспилотные летательные аппараты (БПЛА), способные выполнять разведывательные и атакующие функции.
Применение таких систем вооружений требует обеспечения повышенной информационной безопасности выполнения ими поставленных им задач с позиции криптографической стойкости [19; 20], поскольку практика их применения уже давно показала их уязвимость [21; 22], обусловленную необходимостью (1) осуществлять постоянный обмен информацией БПЛА с наземными пунктами управления и между собой, (2) использовать внешнюю систему при позиционировании БПЛА в пространстве.
Например, одни специалисты [21] отмечают, что малые БПЛА при приеме информационно-управляющих пакетов не способны уверенно и точно идентифицировать посылающего эти пакеты субъекта и определить отсутствие или наличие зловредных изменений в изначальных пакетах, поэтому криптографическая защита является необходимостью для реализации информационного обмена в управляющем контуре «наземный оператор - оборудование БПЛА. Другие [24; 25; 26. P. 113-122] говорят, что недорогие БПЛА ограничены в ресурсах с точки зрения энергии, памяти, хранилища и вычислительной мощности, что не позволяет специалистам внедрять передовые и сложные решения криптозащиты у них на борту.
В любом случае отсутствие криптозащиты предоставляет сторонним интересантам возможность, подключившись к БПЛА, получить имеющуюся у него информацию и повлиять на ее содержание или на процесс управления аппаратом [26. P. 113-122]. Именно такой возможностью воспользовались, например, иракские повстанцы, в ноутбуках которых американские войска летом 2009 г. обнаружили программное обеспечение (далее - ПО), позволяющее перехватывать видео с беспилотников, передаваемое по незашифрованным каналам связи. По данным американских военных именно использование нешифрованных каналов связи на БПЛА RQ/MQ-1 Predator и MQ-9 Reaper дало такую возможность иракцам, использовавшим с середины 2008 г. для этих целей программный продукт малоизвестной российской фирмы [27; 21].
В настоящее время вид связи БПЛА-БПЛА (Drone-to-Drone, D2D) - не стандартизирован, поэтому фактически для разработки и оптимизации интеллектуальной системы беспроводной связи на базе БПЛА может быть использовано машинное обучение. В большинстве случаев связь D2D может быть смоделирована как одноранговая (Peer-to-Peer (P2P) communication), что сделает ее уязвимой для различных типов P2P-атак, включая помехи (напр., распределенный отказ в обслуживании (Distributed Denial of Service, D-DoS) и атака Сивиллы (Sybil attack) - вид атаки в одноранговой сети, в результате которой жертва подключается только к узлам, контролируемым злоумышленником [23]).
Кроме указанных, очередным уязвимым звеном для атак хакеров (противников), как показала практика, являются наземные компьютерные сети, управляющие беспилотниками. Большинство коммуникаций между БПЛА и землей используют однофакторную аутентификацию, которую можно легко взломать, что делает их уязвимыми для пассивных (подслушивание) и активных (человек посередине) атак и в силу такой доступности являются небезопасными [28. P. 3]. К ним относятся уже известные и стандартизированные промышленные протоколы, которые используются в таких видах беспроводной связи, как Bluetooth и Wi-Fi 802.11, включая 2,4 ГГц и 5 ГГц. Такого рода уязвимости также обсуждаются в отечественной доктрине [29. С. 86-92]. Отмечается, что защита рабочих мест наземных пунктов управления бесплотного авиационного комплекса (БПАК) от несанкционированного доступа к ним в качестве основных методов и средств обеспечения информационной безопасности должна предусматривать использование персоналом: (1) постоянно изменяемых паролей из шести символов; (2) запрограммированных специальных клавиш для уничтожения всей информации из всех видов памяти компьютера; (3) защиты электронного документооборота, осуществляемого при оперативной связи с командованием. Реализация такой защиты распространяется на весь состав комплекса и должна осуществляться с задаваемым уровнем криптостойкости для коротких сообщений с использованием их «быстрого» шифрования и дешифрования.
Организация информационной безопасности таких комплексов обычно достигается использованием надежной охраны мест размещения компьютеров и экранирования их корпусов для предотвращения перехвата и считывания содержащейся на них информации. Это сопровождается скрытным обменом последней по радиоканалам; ее сжатием при передаче с БПЛА на наземный пункт управления, обеспечением используемых радиоканалов устойчивостью к помехам противника и так далее. Как видим, для целей информационной безопасности наземных комплексов БПАК реализуются все существующие средства (физические, аппаратные, программные) и методы (криптография) защиты.
В связи со сказанным безопасным и надежным ранее считался вид связи БПЛА – спутник (Drone-to-Satellite, D2S), который позволяет отправлять координаты в реальном времени через Глобальную систему позиционирования (GPS) и позволяет отозвать любой БПЛА на исходную станцию, если он вышел за линию контроля или за пределы прямой видимости, и хотя спутниковая связь стоит дорого, в том числе в плане технического обслуживания, этот вид связи довольно широко используется вооруженными силами [29. С. 86-92; 30].
Учитывая вышеизложенное, становится очевидным, что квантовая криптография является ближайшей перспективой защиты каналов связи для передачи ценной стратегической информации и разработки специальных технологий для квантового распределения ключей при защите беспилотных видов транспорта от массового взлома.
В этом формате, как отмечают зарубежные специалисты [31], суды неохотно признают патентоспособной обычную реализацию шифрования на существующих компьютерных технологиях, однако разработка нового алгоритма шифрования в целом с большей вероятностью получит патентную защиту. Попробуем разобраться в этом вопросе лучше.
Например, когда кто-то решает использовать возможности патентной системы США для защиты технологий, таких как криптография, необходимо подать заявку на патент в Управление по патентам и товарным знакам США (U.S. Patent and Trademark Office, USPTO).
В практическом смысле большая часть криптографии была и будет развернута с помощью программного обеспечения, являющегося по сути алгоритмичным. Поэтому многие патентные формулы, охватывающие криптографию, будут представлять собой скорее формулы способов, в которых перечисляется ряд этапов, составляющих способ в целом, в котором криптография по своей сути рассматривается как алгоритмичная (основанная на алгоритме) аналогично тому, как является алгоритмичным программное обеспечение (компьютерные программы). То есть на сегодня речь идет о патентовании алгоритма, а не самой компьютерной программы / программного обеспечения, математического метода, лежащих в основе метода сугубо абстрактной концепции и т.п., ведь ни программное обеспечение, ни компьютерные программы прямо не упоминаются в патентном праве США, а математические методы и абстрактные концепции не патентуются. По сути, суды США, даже рассматривая дела, становящиеся затем знаковыми в этом вопросе, такие как: Gottschalk v. Benson, 409 US 63 (1972); Parker v. Flook , 437 US 584 (1978); Diamondv. Diehr, 450 US 175 (1981); State Street Bank and Trust Company v. Signature Financial Group, Inc.,149 F.3d1368 (Fed. Cir. 1998); InreBilski, 545 F.3d 943, 88 USPQ2d 1385 (Fed. Cir. 2008); AliceCorp. v. CLSBankInternational, 573 US 208 (2014) и противоположное им решение по делу DDR Holdings, LLC v. Hotels.com, LP, 773 F.3d 1245 (Fed. Cir. 2014) и др. [32], избегают (по возможности) высказывать мнения о программном обеспечении или компьютерных программах как объектах патентования как таковых, и сводят рассмотрение подобных дел к решениям о патентах на программное обеспечение или компьютерные программы, направленные на реализацию бизнес-методов, которые признаются опять-таки непатентоспособными.
Тем не менее патенты, применяемые к компьютерным программам (патенты на программное обеспечение), были реализованы в компьютерной индустрии (одни без особого желания, другие - с большой охотой) в течение последних тридцати лет. При этом, к числу самых ранних (конец 1960-х - начало 1970-х г.) и важных патентов, выданных Управлением по патентам и товарным знакам США на программное обеспечение, относятся патенты, касающиеся криптографии. Невзирая на то, что компьютерные алгоритмы в тот период времени были признаны непатентоспособными, патент на криптографию можно было получить, если он был заявлен как патент на устройство шифрования, построенное с применением аппаратного обеспечения. Объясняется это тем, что в то время скорость действия компьютеров была не велика и не могла обеспечить надежность существующего шифрования за необходимое (короткое) время. По сути, благодаря машине, реализовавшей способ шифрования, компания IBM смогла получить патенты на алгоритм, ставший в США впоследствии стандартом шифрования данных DES (U.S. Data Encryption Standard). При этом следует отметить, что в США действовала и действует доктрина эквивалентности (doctrine of equivalence), согласно которой новое устройство нарушает первоначальный патент, если, по сути, оно работает и дает тот же результат, что и запатентованное устройство. Эта доктрина воплощает в себе основополагающий принцип патентного права. Вследствие действия этого принципа нарушением запатентованной технологии шифрования будет признана любая программа, использующая эту технологию даже на иных по техническому строению машинах. Однако, повышение быстродействия компьютеров, позволяющее реализовывать базовые логические схемы программного обеспечения, и принятие патентного законодательства относительно электронных устройств, способствуют тому, что с течением времени компьютерные программы смогут стать предметом патентного права [33. P. 118].
В настоящее время к числу других криптографических патентов относятся следующие: US4218582A (Public Key Cryptographic Apparatus and Method) (URL: https://patents.google.com/patent/US4218582A/en?oq=US4%2c218%2c582 (дата обращения: 08.09.2021)), US4200700A (Cryptographic Apparatus and Method) (URL: https://patents.google.com/patent/US4200770A/en (дата обращения: 08.09.2021)), US4405829A (Cryptographic Communications System and Method) (URL: https://patents.google.com/patent/US4405829A/en (дата обращения: 08.09.2021)) и др. [34] При этом патентная формула, содержащая утверждение о криптографическом способе, написанная широким языком без ссылки на программное обеспечение, может быть нарушена, если предположить, что такое утверждение уже действительно в соответствии с патентным законодательством, - например, есть владелец патента, который уже создал какой-либо метод, а третье лицо начинает его «использовать» [35. P. 757 et seq.].
Одновременно разрабатываемые в настоящее время новые технологии применения квантовых методов шифрования, реализуемые на основе использования особенностей физической квантовой механики, априори подлежат правовой защите в качестве объектов патентования [36].
Как же можно запатентовать изобретение в области криптографии в странах БРИКС?
Согласно Закону Бразилии № 9.279 от 14 мая 1996 г. «О промышленной собственности» [37] (в ред. Закона № 10.196 от 2001 г., далее – Закон 1996 г.) не могут быть запатентованы математические методы (п. I ст. 10), сугубо абстрактные концепции (пп. II ст. 10), схемы, планы, принципы и методы - деловые, бухгалтерские, финансовые, образовательные, рекламные, лотереи и надзор (п. III ст. 10), компьютерные программы сами по себе (п. V ст. 10), представление информации (п. VI ст. 10) и правила игры (п. VII ст. 10). В практическом плане к вопросу патентования нужно подходить аккуратно. Так, в соответствии с бразильской патентной практикой «способ» (метод) сам по себе (“Method” per se) может использоваться в описании патента, имеющем то же значение, что и термин «процесс» (“Process”) [38]. При этом, когда в патентной формуле заявлен способ (согласно ст. 10 и 18 Закона 1996 г.), он должен решать техническую проблему и должен быть жизнеспособен в контексте приведенных выше запретов ст. 10 Закона 1996 г.
Итак. Математический анализ, линейная алгебра, дискретная математика и др. необходимы программистам, особенно тем, кто решает заняться криптографией [39], при этом стоит четко иметь в виду, что уравнение не подлежит патентованию, хотя для его решения требуются умственные усилия, а результат представляет собой итого решения исключительно математической задачи, а не технической проблемы.
Абстрактные концепции, например, математические, могут становиться мощным и универсальным средством выявления физических законов [40], но законы природы просто существуют, проверяются учеными в области прикладных исследований, и не могут быть запатентованы, однако, если кто-то использует закон или принцип физики, добавляя технический дифференциал или улучшая работу какого-либо устройства, действующего согласно этому закону, по отношению к имеющемуся уровню техники, это улучшение имеет право на патентование. Также способ реализации абстрактных концепций, если его изложение убеждает эксперта, приобретает патентоспособность.
В контексте п. III ст. 10 Закона 1996 г. отмечается [38], что согласно бразильским критериям патентной экспертизы некоторые примеры способов не являются патентоспособными, это: анализ рынка, аукционы, консорциумы, программы стимулирования, способы, касающиеся работы торговых точек; банковские переводы через банковскую сеть или банкомат, которые включают в себя среди своих функциональных этапов расчеты обменного курса и платы за услуги; банковские методы, обработка налогов, страхование, анализ имущества, финансовый анализ; методы аудита, инвестиционное планирование, пенсионные планы, медицинское страхование, методы онлайн-покупок; онлайн-метод продажи авиабилетов через Интернет и др. Однако, например, если способ реализации чего-либо в финансовой сфере решает техническую проблему, он может быть патентоспособным. Классическим примером является способ шифрования, используемый в разных сферах, в том числе в банковской.
Что касается компьютерных программ самих по себе, то есть исходного кода, то он не является патентоспособным, но защищается регистрацией авторских прав на него. Патентом можно защитить алгоритм - как изобретение, связанное с программным обеспечением (software related invention), если такое изобретение можно определить как техническое решение, которое решает техническую проблему и создает технические эффекты [41].
С принятием Патентным ведомством Бразилии 29 декабря 2020 г. новых Руководящих принципов рассмотрения патентных заявок, касающихся изобретений, реализованных в программном обеспечении» [42; 43] (далее – Руководящие принципы) практика работы Ведомства с тем, что ранее называлось «патентами на программное обеспечение» (“Software Patents”), изменилась.
Сейчас заявки на выдачу таких патентов описываются как «патентные заявки, включающие изобретения, реализованные с помощью компьютерных программ / программного обеспечения» (“Patent Applications Involving Inventions Implemented by Computer Programs”, ‘computer-implemented invention’, ‘Software Implemented Inventions’), что имеет больше смысла.
До принятия Руководящих принципов правило гласило, что «патент на программное обеспечение» будет выдан только в том случае, когда программное обеспечение используется на каком-либо (любом - персональный компьютер, микроконтроллер и др.) оборудовании и соблюдены критерии патентоспособности согласно Закону.
Сейчас внесены и действуют следующие ключевые изменения:
- математические методы могут считаться изобретениями, если они применяются для решения технических задач и обеспечивают технический эффект. Однако простая реализация математического метода с помощью программного обеспечения все еще не имеет права на получение патента. Бизнес-методы также не подходят для этого, даже если они реализованы на компьютере;
- при оценке изобретательского уровня важно определять, является ли технический эффект результатом самого изобретения, а не применения компьютера, с использованием которого реализовано изобретение;
- заявки на патентование процесса и продукта принимаются. Примерами заявок на патентование продукта являются системы и устройства. Заявки на патентование программного обеспечения и программных продуктов самих по себе не принимаются. Последние должны быть оформлены в виде заявок на программное обеспечение и программные продукты на машиночитаемом носителе (как увидим ниже, как и в Китае, например);
- использование способа выражения «средство плюс функция» (“means plus function” / средство для…) приемлемо для формулы продукта в заявке, если невозможно определить продукт в его структурных элементах и/или средства, изложенные в заявке понятны для специалиста в данной области [44]. В этой связи отмечается [45], что описание в заявке в этом случае должно сопровождаться достаточным количеством примеров, когда эта функция практически реализуется, что служит обоснованием использования такой терминологии. Недостаточный объем конкретной информации приводит к осложнению этапа экспертизы и снижению шансов патента сохраниться при возникновении этапа его аннулирования (Bilskivs. Kappos, 2010; AliceCorp. vs. CLSBankInternational, 2014 и др.).
С позиции требования законодательства о том, что во всех областях техники, как уже отмечалось, по-прежнему важно решить на современном уровне техническую проблему и достичь нового технического эффекта, который не связан с тем, как была написана программа, и, хотя Руководящие принципы не уточняют, что именно означает «техническое решение», они содержат несколько примеров приемлемых изобретений [41], это: графический интерфейс, который связывает личные заметки с выдержками электронного документа с помощью тегов XML; способ шифрования данных; способ уплотнения данных; кодирование принятого радиосигнала; способ обработки электрокардиографических сигналов для получения параметров, которые могут помочь врачу диагностировать заболевание; способ сокращения времени доступа к памяти; способ фильтрации сейсмических данных; способ управления двигателем с помощью численного интегрирования; способ, который оптимизирует управление файлами, аппаратные ресурсы, использование памяти и/или время работы; методы и системы, применяемые для управления машиной, устройством или роботом и т.д.
Таким образом закон признает три процесса [38], которые возможно запатентовать, когда в них используются следующие величины:
а) физические для создания продукта или физического эффекта, например, заявка на патент, программное обеспечение которой использует данные датчиков (рассматриваемых физических величин, поскольку они измеряют, например, ускорение, скорость и т.д.) для вывода (действия) на тормоз АБС автомобиля;
б) физические (например, амплитуда электрического сигнала) для создания нематериального продукта (например, для обработки изображений камер с низким разрешением);
c) абстрактные для создания виртуального продукта в результате преобразования одного виртуального продукта в другой виртуальный продукт, хранящийся на устройстве. (например, сжатие данных, шифрование, управление базами данных, протоколы передачи данных).
В России в силу пп. 2), 4-6) п. 5 ст. 1349 Гражданского кодекса [46; 47] не патентуются научные теории и математические методы; правила и методы игр, интеллектуальной или хозяйственной деятельности; программы для ЭВМ; решения, заключающиеся только в представлении информации. Но в качестве изобретений могут признаваться алгоритмы сжатия или шифрования информации для хранения на носителе или для передачи в канале связи [48]. Патент в этом случае защищает саму логику работы программы, ее суть и выдается на технические решения, относящиеся к способу (процессу осуществления действий над материальным объектом, выполняемому с помощью материальных средств - п. 1 ст. 1350 ГК РФ) [49; 50; 51], к которым относятся, например, работы IT-системы, передачи или обработки информации, управления аппаратно-программным комплексом [52; 53]. В этом случае для обеспечения адекватного объема охраны изобретения и достаточности его противодействия аннулированию необходимо так составить описание алгоритма, чтобы оно удовлетворяло требованию наличия описания изобретения в виде, раскрывающем его сущность, и в объеме, необходимом специалисту в данной области для понимания сути реализации изобретения (п. 2(2) ст. 1375 ГК РФ). При этом описание изобретения должно демонстрировать связь технического результата с признаками изобретения, сформулированными в формуле изобретения, в виде четкой логической цепочки изобретения «назначение – признаки – технический результат» [48]. Кроме того, возможно патентование аппаратно-программного комплекса, который используется для этих целей. Стоит иметь в виду, что такой патент не всегда защищает программу отдельно от устройства: когда программа встроена в какое-то устройство, можно запатентовать и устройство, и алгоритм, по которому оно работает, получится патент, который защищает весь аппаратно-программный комплекс [54]. Как показывает анализ выданных патентов, когда в программе заложен уникальный алгоритм, получается патент на изобретение-способ, и, когда программа встроена в устройство, одним патентом патентуется устройство и способ его работы. Также возможна регистрация исходного кода программы сжатия или шифрования информации, которая подтверждает лишь то, что у определенного лица на определенную дату уже был код, но не защищает суть программы, ее идею, функционал или логику работы. Согласно п. 1 ст. 1261 ГК РФ охраняется исходный текст и объектный код компьютерных программ также, как и тексты книг - авторским правом.
В Индии согласно положениям ст. 2(1)(j) Закона «О патентах» 1970 г. [55] (в ред. Закона 2002 г., далее – Закон 1970 г.) «изобретение» означает новый продукт или процесс, предполагающий наличие изобретательского уровня (inventive step, см. решения по делам Biswanath Prasad Radhey Shyam vs Hindustan Metal Industries Ltd [56], Rado v. John Tye & Son Ltd. [57. P. 319–356], F. Hoffmann-La Roche Ltd vs Cipla Ltd. [58]) и возможность промышленного применения (capability of industrial application).
В соответствии со ст. 2(1)(ja) «изобретательский уровень» означает особенность (a feature) изобретения, которая включает техническое продвижение вперед (technical advance) по сравнению с существующими знаниями или экономическое значение (economic significance) или и то, и другое, которые делают изобретение неочевидным для специалиста в данной области техники.
Согласно ст. 2(1)(ac) «возможность промышленного применения» в отношении изобретения означает, что оно может быть изготовлено или использовано в промышленности (being made or used in an industry).
Иными словами, Закон 1970 г. требует от заявителя указать, «что» представляет собой изобретение и «как» его реализовать.
Например, если заявка на патент относится к «устройству/системе» (apparatus/system/device), т.е. изобретениям, основанным на аппаратном обеспечении, каждая особенность изобретения должна быть описана с соответствующими иллюстративными рисунками. Если изобретение относится к «способу» (method), должна быть четко описана необходимая последовательность шагов, чтобы отличить изобретение от предшествующего уровня техники с помощью блок-схем и другой информации, необходимой для реализации изобретения одновременно со способами/средствами такой реализации.
Вместе с тем должны быть описаны рабочие взаимоотношения различных компонентов вместе с возможностью подключения и желаемый изобретателем результат (desired result/output or the outcome of the invention), а также наилучший способ применения и/или использования изобретения, описывающий не только и не столько его функциональные возможности, сколько способ его реализации (применения - implementation of the invention – п. 4.4.1 и 4.4.2 Руководства по экспертизе изобретений, связанных с компьютерами (Computer Related Inventions, CRIs) Патентного ведомства Индии [59] (далее – Руководство 2017 г.)
Согласно ст. 2(1)(l)4, «новое изобретение» - это любое изобретение или технология, которая не была ожидаема (предвидена - has not been anticipated) в публикации ни в одном документе или используема в Индии или где-либо еще в мире до даты подачи заявки на патент с полной спецификацией, т.е. патентная формула не находилась в общественном достоянии (in public domain) или не составляла уровень развития техники на рассматриваемый период времени.
Согласно Руководства 2017 г. основными элементами в применении информационных технологий, являются компьютеры и их периферийные устройства. Изобретения, связанные с компьютерами, включают в себя изобретения, предполагают использование компьютеров, компьютерных сетей или других программируемых устройств, и такие изобретения, одна или несколько функций которых полностью или частично реализованы с помощью компьютерной программы или программ [59. P. 3]. В этом смысле Руководство 2017 г. определяет на основе иных законов Индии (напр., Закона об информационных технологиях 2000 г. № 21 / The Information Technology Act, 2000 (No. 21 of 2000)), Закона об авторском праве 1957 г. / Copyright Act 1957), Оксфордского словаря для продвинутых пользователей (Oxford Advanced Learners Dictionary) и др. такие понятия как «компьютер», «компьютерная сеть», «компьютерная система» и др.
Так, компьютерная программа согласно ст. 2(ffc) Закона об авторском праве означает набор инструкций, выраженных словами, кодами, схемами или в любой другой форме, включая машиночитаемый носитель, способный заставить компьютер выполнить определенную задачу или достичь определенного результата.
Словосочетание «само по себе» (per se), не определенное в законодательных актах Индии, включая Закон 1970 г., понимается в его общем словарном значении как «как таковое», «само по себе», чтобы показать, что имеется в виду что-то само по себе, а не в связи с другими вещами. «Алгоритм» (algorithm) таким же образом понимается как «набор правил, которым необходимо следовать при решении конкретной проблемы», а «программное обеспечение» (software) также понимается как «программы и т.д., используемые для работы с компьютером».
Согласно ст. 3 Закона 1970 г. непатентоспособны: п. (k) математический или бизнес-метод или компьютерная программа как таковая или алгоритмы; п. (m) простая схема, или правило, или метод выполнения умственного действия, или метод игры; п. (n) представление информации; п. (o) топография интегральных схем.
Так, в то время как оценка математических или бизнес-методов сравнительно проще, компьютерные программы как таковые или изобретения, связанные с алгоритмами, требуют тщательного рассмотрения в ходе патентной экспертизы. Компьютерные программы часто заявляются для патентования как способ или система с указанием на функции технологических схем или этапов процесса. Заявки, связанные с алгоритмами, часто заявляются даже шире, чем компьютерные программы, описываемые как единый алгоритм, который может быть реализован с помощью разных программ на разных компьютерных языках. В любом случае, если, по существу, формулы изобретения в любой форме, такие как способ/процесс, устройство/система/устройство, программный продукт для ЭВМ/ машиночитаемый носитель, относятся к указанным запрещенным категориям, они не будут патентоспособны.
Даже если проблема при оценке заявки связана с соотношением аппаратного и программного обеспечения, выражение функциональности как способа следует оценивать по существу, так как внимание должно уделяться содержанию изобретения, а не конкретной форме, в которой оно заявлено, поэтому нельзя маскировать заявку на компьютерные программы как таковые формулировками как будто бы решаемой задачи (п. 4.4.4 Руководства 2017 г.) [59. P. 13-14].
Использование способа выражения «средство плюс функция» (“means plus function” / средство для…) приемлемо для формулы продукта в заявке, если невозможно определить продукт в его структурных элементах и/или средства, изложенные в заявке понятны для специалиста в данной области, поскольку формулы изобретений, связанных с компьютерами, часто касаются способов реализации ряда функций, таких как средства (means) преобразования цифрового сигнала в аналоговый и т.д. Для повышения разборчивости формулы изобретения в таких случаях называемые в формуле изобретения «средства» должны быть четко определены с помощью их физических конструктивных особенностей и цифр. Не допускаются такие формулировки формул изобретения, если конструктивные особенности называемых средств не раскрыты в спецификации. Если спецификация поддерживает выполнение изобретения исключительно с помощью компьютерной программы, то такие формулы изобретения отклоняются, поскольку указанные средства являются не чем иным, как компьютерной программой как таковой. Равным образом, если в спецификации не раскрыты структурные особенности называемых средств, и спецификация поддерживает выполнение изобретения исключительно с помощью программного обеспечения, то в этом случае средства в формуле изобретения опять-таки являются не чем иным, как программным обеспечением (п. 4.4.5 Руководства 2017 г.) [59. P. 14-15].
В качестве примеров непатентоспособных компьютерных программ (программного обеспечения) как таковых Руководство приводит заявки, касающиеся: (i) компьютерных программ/ набора инструкций/ процедур и/или подпрограмм; (ii) «компьютерных программных продуктов» / «носителя информации с инструкциями» / «базы данных» / «компьютерной памяти с инструкциями», хранящейся на считываемом компьютером носителе и др. (п. 4.5.4 Руководства 2017 г.).
Законодательное намерение прикрепить к компьютерной программе определение «как таковая» очевидно из следующего мнения, выраженного Объединенным парламентским комитетом при внесении патентов (поправок) Закон 2002 г.: «В новом предлагаемом пункте (k) были добавлены слова «как таковые». Это изменение было предложено потому, что иногда компьютерная программа может включать в себя некоторые другие вещи, вспомогательные к ней или разработанные на ее основе. Намерение здесь не состоит в том, чтобы отклонить их для выдачи патента, если они являются изобретениями. Однако компьютерные программы как таковые не предназначены для получения патента. Эта поправка была предложена для уточнения цели» [59. P. 17].
Алгоритмы во всех формах, включая, но не ограничиваясь, набором правил или процедур или любой последовательностью шагов или любым методом, выраженным в виде конечного списка определенных инструкций, будь то для решения проблемы или иным образом, и независимо от того, используют ли логический, арифметический или вычислительный метод, рекурсивный или иной, непатентоспособны (п. 4.5.3 Руководства 2017 г.).
Математические методы являются частным примером принципа, согласно которому чисто абстрактные или интеллектуальные методы не подлежат патентованию. Таким образом, математические методы, такие как метод вычисления, формулировка уравнений, нахождение квадратных корней, кубических корней и все другие подобные акты умственного мастерства, не подлежат патентованию. Аналогичным образом, простые манипуляции с абстрактной идеей или решение чисто математической задачи/уравнений без указания практического применения также не подлежат патентованию. Однако простое наличие математической формулы в формуле изобретения для четкого определения объема охраны, испрашиваемой в изобретении, не обязательно делает его формулой «математического метода». Кроме того, данный запрет может не применяться к изобретениям, которые включают математические формулы, в результате которых создаются системы кодирования, снижения шума в системах связи/ электрических/электронных системах или шифрования/ дешифрования электронных сообщений (п. 4.5.1 Руководства 2017 г.)
Понятие «бизнес-метод» включает в себя весь спектр видов деятельности на коммерческом или промышленном предприятии, связанных с торговлей товарами или услугами. Заявки, сформулированные не напрямую как «методы ведения бизнеса», но, с большой вероятностью, с использованием некоторых таких средств, непатентоспособны. Однако, если в заявленной патентной формуле указывается устройство и/или технический процесс для реализации изобретения (даже частично), формула изобретения должна быть рассмотрена в целом. Когда заявка по существу является «бизнес-методом», она не должна рассматриваться как патентоспособный объект. Однако простое присутствие в формуле изобретения таких слов, как «предприятие», «бизнес», «бизнес-правила», «цепочка поставок», «заказ», «продажи», «транзакции», «коммерция», «оплата» и т.д., не может привести к выводу, что изобретение является просто «бизнес-методом». Однако, если заявка по существу касается осуществления коммерческой/ торговой/ финансовой деятельности/ транзакции и/или способа покупки/продажи товаров через Интернет (например, предоставления функциональности веб-сервиса), то же самое следует рассматривать как бизнес-метод, которые не может быть запатентован.
В Китае согласно принятому в 2019 г. Закону «О шифровании» [60; 61; 83] (в силе с 1 января 2020 г., далее – Закон 2019 г.) государство поощряет и поддерживает научно-технические исследования в сфере шифрования и защищает интеллектуальную собственность на криптографические способы [62] и технологии, поскольку само шифрование Закон 2019 г. понимает как технологии, продукты или услуги, применяющие определенные преобразования к информации для обеспечения защиты или аутентификации безопасности (ст. 2). Отметим, что в России также можно получить патент на технологию (как совокупность процессов обработки или переработки материалов в определенной отрасли производства, технологическую схему (линию)) [52]. Важно иметь ввиду, что согласно ст. 25 более раннего Закона - «О патентах» КНР 1984 г. [63] (далее – Закон 1984 г.) - запрещается патентование правил и способов интеллектуальной деятельности (rules and methods for intellectual activities), - на этом основании из сферы патентования исключаются математические правила и алгоритмы (mathematical rules and algorithms themselves), поскольку они, обычно, не решают никаких технических проблем и, следовательно, не являются техническими решениями [64]. При этом обновленные Руководящие принципы патентной экспертизы (Guidelines for Patent Examination) [65] в редакции от 1 апреля 2017 г. (далее – Руководящие принципы) и соответствующая практика патентной экспертизы согласно растущим требованиям к защите изобретений, связанных с программным обеспечением (computer-related inventions), создали по мнению исследователей [66], беспрецедентно благоприятную среду для такого рода патентных заявок. Согласно Части II, Главе 1, разделу 4.2 Руководящих принципов «компьютерная программа как таковая» (‘a computer program per se’) подпадает под категорию правил и способов интеллектуальной деятельности, которые исключаются из патентной защиты, как это предусмотрено в ст. 25 Закона 1984 г. Поэтому в течение длительного времени до 1 апреля 2017 г. заявки, касающиеся компьютерных программ или машиночитаемых носителей, характеризующихся только хранящимися на них компьютерными программами, отклонялись как направленные на защиту правил и способов интеллектуальной деятельности. В то время формула изобретения, направленная на защиту изобретения, связанного с программным обеспечением, могла быть запатентована только в том случае, если она была составлена как способ, содержащий этапы, или устройство, содержащее модули, для выполнения этапов в строгом соответствии с формулой способа или технологическим процессом, изложенным в описании. При этом заявка, касающаяся способа, могла сталкиваться с трудностями при реализации прав из патента, а заявка на патентование «устройства, содержащего модули» (‘apparatus comprising modules’) - приводить к ограниченному применению, поскольку некоторые судьи, применяющие патентный закон, считали неясным, к каким аппаратным компонентам на самом деле относятся «модули». Ни одно из вышеуказанных требований к способу и устройству не было бы нарушено, если бы компьютерные программы распространялись в виде машиночитаемых носителей. Именно опасения такого рода относительно претензий к патентным заявкам породили в индустрии программного обеспечения спрос на ослабление формальных требований к изобретениям, связанным с программным обеспечением, с тем чтобы новаторам было легче обеспечивать соблюдение своих патентных прав. Поэтому кроме того, что приемлемое изобретение, относящееся к компьютерным программам, должно решить техническую проблему (should solve technical problem), содержать в себе предлагаемые технические меры (adopt a technical measure) и достигать посредством них технического эффекта (achieve a technical effect), и три этих технических фактора должны быть отражены в заявленном техническом решении, которое управляет, направляет или обрабатывает объект, внешний по отношению к компьютеру, или его внутренний объект (controls, guides, or processes an object external to a computer or an internal object thereof), и представляется на экспертизу [67], с 1 апреля 2017 г. положения Части II, Главы 9, Раздела 2 Руководящих принципов были пересмотрены и предусматривают такие формулировки: «Если формула изобретения просто относится к алгоритму или правилам математических вычислений, или компьютерным программам как таковым, либо компьютерным программам как таковым, записанным на носителях (таких как ленты, диски, оптические диски, магнитно-оптические диски, ПЗУ, PROM, VCD, DVD или другие машиночитаемые носители), или правилам или методам игр и т.д., она подпадает под действие правил и методов интеллектуальной деятельности и не является объектом, для которого может быть запрошена патентная защита.» [68. С. 12-15] При этом суть новеллы в добавлении слов «как таковая» (per se) выглядит именно как требуемая редакция. Государственное ведомство интеллектуальной собственности Китая (State Intellectual Property Office of China, SIPO) пояснило, что данная правка предназначена для того, чтобы отличать последовательность машиночитаемого кода, которая должна быть защищена авторским правом, от технического решения, полностью или частично основанного на технологическом процессе компьютерных программ. Таким образом, пересмотренные Руководящие принципы разъяснили, что то, что не может быть защищено, - это машиночитаемый носитель с программным кодом «как таковым», но машиночитаемый носитель, содержащий инструкции по выполнению технического метода, больше не исключается из патентной защиты. Другими словами, с 1 апреля 2017 г. машиночитаемый носитель, описанный в инструкциях, записанных на нем, больше не отклоняется экспертами патентного ведомства просто из-за названия в формуле изобретения.
Также стоит отметить, что, хотя в пересмотренных Руководящих принципах словосочетание «как таковая» также используется после словосочетания «компьютерные программы», когда машиночитаемый носитель не упоминается, в нынешней практике патентной экспертизы разрешен только машиночитаемый носитель, а одна компьютерная программа без материального носителя по-прежнему исключается из патентной защиты в соответствии с нынешней практикой патентной экспертизы.
Кроме того, пересмотренные Руководящие принципы затронули положения Части II, Главы 9, Раздела 5.2 и звучат теперь следующим образом: «Если заявка составлена для получения патента на аппаратное средство (as an apparatus claim), в формуле изобретения должны быть указаны различные составные части этого средства и соединения между ними, причем составные части могут включать не только аппаратное обеспечение, но и программы» (…the component parts may comprise not only hardware but also programs). SIPO пояснило, что эта новелла призвана разъяснить, что способ разработки устройства, включающего функции программного обеспечения, не будет ограничен «устройством, содержащим модули», как описано выше, но формула изобретения может быть составлена как устройство, содержащее память, в которой хранятся компьютерные программы, и процессор, сконфигурированный для выполнения нескольких шагов при выполнении компьютерных программ. Такой способ составления заявки позволит перечислять в ней фактические компоненты, такие как память, процессоры и другое аппаратное обеспечение, которые содержатся в устройстве, вместо «модулей» с расплывчатыми значениями.
В соответствии с пересмотренными Руководящими принципами теперь могут существовать следующие способы составления заявки на получение охраны изобретения, связанного с программным обеспечением:
• способ, включающий этапы...;
• устройство, содержащее модули для...;
• устройство, содержащее память, в которой хранятся компьютерные программы, и процессор, сконфигурированный для выполнения при выполнении компьютерных программ шагов...
• считываемый компьютером носитель информации, на котором хранятся компьютерные программы, причем компьютерные программы сконфигурированы для выполнения /при выполнении на процессоре шагов...
Поскольку пересмотренные Руководящие принципы патентной экспертизы вступили в силу совсем недавно, еще не было много судебных дел, чтобы точно решить, что наиболее полезно для правоприменения. Во всяком случае, чтобы избежать трудности с пониманием и интерпретацией того, как на самом деле работает программное обеспечение, со стороны судей, целесообразно добавлять некоторое общее описание аппаратной и программной среды, в которой может быть реализовано изобретение [66; 69].
Согласно п. (2) ст. 25 Закона ЮАР «О патентах» № 57 от 1978 г. (в ред. 2011 г.) [70; 71] непатентоспособны в русле рассмотренных выше подходов научные теории; математические методы; схемы, правила или методы выполнения умственного действия, игры или ведения бизнеса; компьютерные программы или представления информации [72]. При этом любые из этих объектов непатентоспособны лишь как таковые (as such / per se) [1]. Критериями патентоспособности выступают: новизна, изобретательский шаг (inventive step) и пригодность к использованию/применению в торговле, промышленности или сельском хозяйстве. На 2008 г. [1. P. 6, 7, 10-11] отмечалось, с одной стороны, отсутствие в ЮАР судебной практики и прецедентного права по вопросу патентования компьютерных программ, с другой, склонность следовать британскому законодательству, которое, в свою очередь, начало следовать соответствующему (более либеральному) европейскому законодательству. В русле такого подхода на основе представлений Европейского патентного ведомства (далее – ЕПВ) изобретения, реализованные с помощью компьютера (Computer Implemented Inventions, CIIs) – это, «Изобретения, реализация которых включает использование компьютера, компьютерной сети или другого программируемого устройства, имеющие одну или несколько функций, которые реализуются полностью или частично с помощью компьютерной программы» [73]. Примеры таких изобретений: способ энергосбережения, компьютерно-реализованный метод оценки эффективности лидерства, компьютеризированный метод обработки счетов-фактур, способ шифрования, схема отказоустойчивости (например, в телефонной связи) и др. Общий подход состоит в защите исходного кода компьютерной программы (software) авторским правом (by сopyright ©). Для патентования CIIs, вероятно, как и в Европе, необходимо наличие технического эффекта (“technical effect”). Методы ведения бизнеса защищаются положениями о коммерческой тайне, ноу-хау и конфиденциальной информации, вместе с тем такие методы, реализованные с помощью компьютерной программы, могут быть патентоспособны. Заявки могут подаваться (как и в Европе) на патентование устройства, способа, носителя данных и/или формы программного продукта для ЭВМ [1. P. 17].
Чтобы понять этот подход приведем несколько решений ЕПВ [1. P. 18-19]:
– (1988) «Вклад в уровень мастерства (art) и полученные эффекты относятся только к области исключенной деятельности... (area of excluded activity)» - не подлежит патентованию;
– (1998) «Продукт компьютерной программы не исключается из патентоспособности... если при его запуске на компьютере он создает дополнительный технический эффект, который выходит за рамки «обычных» (“normal”) физических взаимодействий между программой (программным обеспечением) и компьютером (аппаратным обеспечением)» - патентоспособно [74. С. 360-369];
– (2000) «…устройство, представляющее собой физический объект или конкретное изделие, пригодное для осуществления или поддержки экономической деятельности, является изобретением...»;
– (2002) «Изобретение, состоящее из смеси технических и нетехнических характеристик и имеющее технический характер в целом, должно оцениваться с учетом требований изобретательского уровня, принимая во внимание все те характеристики, которые способствуют указанному техническому характеру, в то время как характеристики, не вносящие такого вклада, не могут поддерживать наличие изобретательского уровня».
В этой связи важно понять отличие технических и нетехнических характеристик (табл. 1).
Табл. 1. Примеры технических и нетехнических характеристик
изобретения (из практики ЕПВ)
|
Технические характеристики
|
Нетехнические характеристики
|
|
Управление тормозом в автомобиле
|
Расчет пенсии
|
|
Более быстрая связь между мобильными телефонами
|
Новые правила проведения аукциона
|
|
Безопасная передача данных (шифрование данных)
|
Продажа и бронирование пакетов парусных круизов
|
|
Распределение ресурсов в операционной системе
|
Эстетические эффекты музыки или видео
|
Источник: [1. P. 21]
Суммируя, технический характер находит выражение в:
• обработке физических данных (напр., параметров или контрольных значений производственного процесса);
• обработка, которая влияет на то, как работает компьютер (это, напр., экономия памяти, увеличение скорости работы компьютера, безопасность процесса, скорость передачи данных и др.);
• подразумевается физическими особенностями (напр., памятью, портами и т.д.) [1. P. 20].
Что касается позиции собственно ЮАР [1. P. 33], то Патентное ведомство признает, что разработчики тратят слишком много усилий, чтобы сразу отказаться от патентов на программное обеспечение. При этом система отсроченной экспертизы теоретически позволяет получить патент на компьютерную программу, и недорого.
Если мы соотнесем полезность патентования изобретений в сфере шифрования с действием положений о коммерческой тайне, то нужно отметить, что представители бизнеса, далекого от техники, ошибочно считают, что дополнительная безопасность их зашифрованных данных может быть обеспечена за счет засекречивания алгоритмов шифрования.
По этой же причине компании, запатентовавшие и использующие новые способы шифрования, отказываются их опубликовывать, опасаясь, что за публикацией последует ослабление безопасности, которой доверяют потребители их продукции. Однако на сегодняшний день специалисты по безопасности считают, что такое обоснование засекречивания алгоритмов шифрования неверно, поскольку оно не приводит к существенному повышению обеспечиваемой этим алгоритмом безопасности, а наоборот способно фактически снизить общую безопасность шифрования [33. P. 120-121]. Кроме того, секретность сама по себе тормозит прогресс науки, что, как правило, не соответствует интересам государства в части развития интеллектуальной собственности в его пределах [75. P. 32-39].
Стоит вспомнить, что согласно «пакету Яровой» [76] - двум законам, направленным на борьбу с терроризмом: №374-ФЗ "О внесении изменений в Федеральный закон "О противодействии терроризму" и отдельные законодательные акты Российской Федерации в части установления дополнительных мер противодействия терроризму и обеспечения общественной безопасности" и № 375-ФЗ "О внесении изменений в Уголовный кодекс Российской Федерации и Уголовно-процессуальный кодекс Российской Федерации в части установления дополнительных мер противодействия терроризму и обеспечения общественной безопасности" «организаторы распространения информации» (cогласно п.1 ст. 101 «Обязанности организатора распространения информации в сети "Интернет" Федерального закона от 27.07.2006 № 149-ФЗ "Об информации, информационных технологиях и о защите информации" [101] организатором распространения информации в сети "Интернет" является лицо, осуществляющее деятельность по обеспечению функционирования информационных систем и (или) программ для электронных вычислительных машин, которые предназначены и (или) используются для приема, передачи, доставки и (или) обработки электронных сообщений пользователей сети "Интернет"[77]) должны в случаях передачи ими сообщений, закрытых криптографическими алгоритмами, передавать в ФСБ РФ ключи для их декодирования под угрозой наложения штрафа за неисполнение этого в размере до миллиона рублей [78]. Вызвано это тем, что каждое соединение, использующее протокол HTTPS (например, интернет-продажи, интернет-банки, социальные сети и др.), шифруется уникальным ключом. Согласно опубликованному Приказу № 432 от 19 июля 2016 г. «Об утверждении порядка предоставления организаторами распространения информации в информационно-коммуникационной сети «Интернет» в Федеральную службу безопасности Российской Федерации информации, необходимой для декодирования принимаемых, передаваемых, доставляемых и (или) обрабатываемых электронных сообщений пользователей информационно-коммуникационной сети «Интернет» (URL: http://publication.pravo.gov.ru/Document/View/0001201608120037?index=2&rangeSize=1 (дата обращения: 09.09.2021)), схема проста: ФСБ России отправляет «организатору передачи информации» заказное письмо с запросом на предоставление «информации для декодирования» (ключей шифрования). Организатор эти ключи обязан предоставить на магнитном носителе по почте (либо по электронной почте). Техническая и/или организационная сложность исполнения в том, что во многих случаях для защищенных интернет-соединений по протоколу HTTPS, например, ключ шифрования меняется каждый раз, когда вы подключаетесь к защищенному сайту (банки, соцсети и т.п.), чтобы выполнить данное требование нужна перенастройка серверов и др., чем компании, не имеющие представительств в России, например, могут формально не заниматься [79].
При этом наблюдается растущая тенденция к академическому дискурсу на тему криптографических алгоритмов.
На практике опубликованные алгоритмы находятся под постоянным контролем, анализирующим их эффективность. Итогом этого анализа стало, например, выявление недостатков у ряда алгоритмов и более широкое применение для защиты данных другими алгоритмами, соответствующими всем критериям анализа. Опыт показывает, что итогом разных стратегий компаний - по сохранению своих алгоритмов в тайне во избежание проверок на надежность и рыночных рисков или по использованию лицензий на ранее секретные алгоритмы с целью получения доли рынка и контроля на нем – становится практическая невозможность сохранения в секрете деталей успешных алгоритмов шифрования. Такие алгоритмы начинают широко использовать, а при таком распространении их можно спокойно проанализировать и успешно реконструировать.
Так было, например, в следующих случаях:
● в 1980-х годах изобретатель Рональд Ривест (ЮАР) разработал альтернативу формату DES - алгоритмы шифрования данных RC2 и RC4, имеющие существенное преимущество в виде переменной длины ключа, обеспечивающей невозможность расшифровки. Для реализации своей криптографической разработки он основал компанию (RSA Data Security), которая продала лицензии многим компаниям США (Microsoft, Apple, Lotus и др.). Однако уже в 1994 г. исходный код алгоритма RC4 был анонимно опубликован в интернете, по-видимому, вследствие «утечки» со стороны одной из многих фирм Силиконовой долины, лицензировавших этот продукт;
● алгоритм RC2 на два года дольше был недоступен широкому кругу потребителей, но и он в 1996 г. был анонимно опубликован в Интернете после анализа копии, предположительно предоставленной Lotus Notes;
● в 1990-х годах киноиндустрия разработала систему шифрования под названием «Система шифрования содержимого» (Contents Scrambling System, CSS) для защиты кинофильмов, которые распространялись на DVD. Эту систему считали безопасной до октября 1999 г., когда в интернете была анонимно размещена «C program», способная расшифровывать DVD-диски. Криптографический анализ показал наличие существенных недостатков у CSS, позволяющих с легкостью расшифровывать DVD-диски; множество других программ, способных расшифровывать DVD-диски, также уже опубликованы в электронном или печатном виде [33. P. 121].
Возможность подобных атак на успешные алгоритмы очевидна, и сохранение секретности любого алгоритма недолговечно. Однако, все равно неопубликованные алгоритмы разработчики пытаются на некоторое время защититься положениями о коммерческой тайне.
Безусловно, национальные законы и политика оказывают важное влияние на надежность и доступность шифрования во всем мире (рис. 1).
Рис. 1. Карта мира с отображением стран, имеющих законы и политики в области
использования шифрования (по степени представленных в них ограничений)
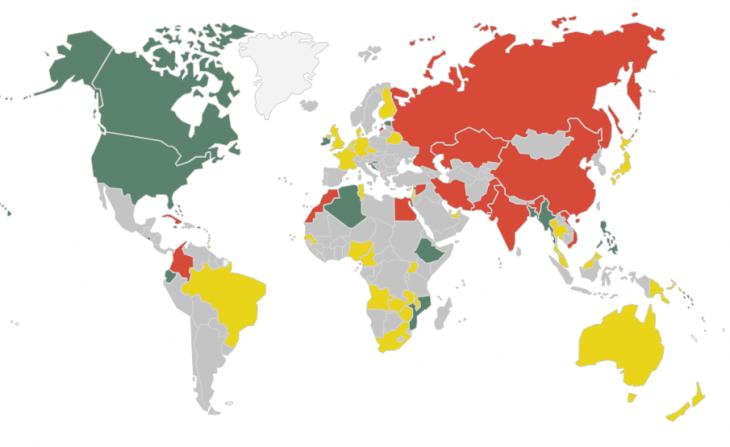

Источник: [80]
С этих позиций интересны положения некоторых рассматриваемых законодательств. Так, высказывается идея [81. P. 4] о том, что национальные законодательства и/или политики должны исходить из следующих 6 принципов:
(1) общее право на шифрование (general right to encryption), согласно которому национальное законодательство или политика должны устанавливать общее право физических лиц на использование продуктов и услуг шифрования, как в России или в Китае (например; Бахрейн, Иран, Пакистан, Саудовская Аравия и др.), на 2017 г. официально запрещали различные формы шифрования на стороне клиента [82]. Так, согласно Закону 2019 г. КНР шифрование делится на «базовое» (core encryption), «обычное» (ordinary encryption) и «коммерческое» (commercial encryption – ст. 6 Закона 2019 г.). Закон 2019 г. не определяет «базовое» или «обычное» шифрование, но указывает, что эти два вида шифрования используются для защиты информации, составляющей «государственную тайну», которая сама по себе классифицируется в КНР на три уровня: совершенно секретно (top secret), секретно (secret), конфиденциально (confidential). Разница между «базовым» и «обычным» шифрованием заключается в том, что «базовое» шифрование может использоваться для защиты всех трех уровней государственных секретов, а «обычное» - только для защиты государственных секретов уровня «секретно» и «конфиденциально» [83]. Коммерческое шифрование используется для защиты информации, которая не считается государственной тайной. Этот вид шифрования таким образом, ключевой для защиты личных данных граждан, юридических лиц и организаций, которые могут использовать эти алгоритмы в соответствии с законом (ст. 8 Закона 2019 г.). Кроме того, базовое шифрование и обычное шифрование, но не коммерческое шифрование, сами по себе признаются государственной тайной и будут подлежать строгому регулированию со стороны Государственного управления криптографии (State Cryptography Administration, SCA – ст. 7 Закона 2019 г.
В Бразилии право на криптографию развивается судебными решениями, например, делами в отношении компании WhatsApp [84. P. 4-5], использующей сквозное шифрование (end-to-end encryption), из-за использования которого суды Бразилии трижды (в 2015 и 2016 гг.) блокировали работу компании. Компания оспаривала судебные решения, ссылаясь на нарушение тем самым норм, регламентирующих защиту данных, конфиденциальности (включая конфиденциальность коммуникаций), свободы слова и бизнес-моделей интернет-компаний, в связи с чем Федеральный верховный суд вынужден был рассматривать законность блокировки. Последний провел открытые слушания с привлечением экспертов для оценки доводов «за» и «против». Во время слушания специалисты по шифрованию, такие как Диего Аранья (Diego Aranha), утверждали, что нынешняя система шифрования основана на контроле, а не на безопасности, и что надежное шифрование является краеугольным камнем безопасности современной информационной экономики и защищает людей от угроз. Напротив, правительство проявило интерес к законному взлому, бэкдорам (от англ. backdoor – изъян, нарочно оставленный программистом в алгоритме, чтобы облегчить себе или кому-то ещё нелегальный доступ к тому, что этот алгоритм, по идее, должен защищать (например, в романе Р. Желязны «Князь Света», 1967 г. (Roger Zelazny. «Lord of Light», 1967. URL: http://lib.ru/ZELQZNY/lord.txt (дата обращения: 11.09.2021)) в огненосный жезл Агни его конструктор Яма встроил специальный механизм, позволяющий самому Яме дистанционно взорвать оружие в руках хозяина. А в «громовую колесницу» Шивы не встроил, о чём потом сильно жалел), такая же дискуссия набирает обороты в Индии [82]) и другим решениям с точки зрения эффективного проведения уголовных расследований и судебного преследования. Представители Федеральной полиции и Прокуратуры вместо этого утверждали, что службы шифрования должны реагировать на требования суда, когда это необходимо, и что при необходимости должны быть предусмотрены исключительные меры доступа для сбора данных. Представители телекоммуникационных компаний встали на сторону сил безопасности, добавив, что телекоммуникационные услуги требуются по закону для предоставления таких услуг, которые являются дорогостоящими, и что провайдеры интернет-услуг должны столкнуться с аналогичным бременем. Другие участники дискуссии (напр., Рональдо Лемос / Ronaldo Lemos) сосредоточились на влиянии блокировки приложений на сетевую инфраструктуру и на важности поощрения конфиденциальности и свободы выражения мнений на уровне контента сети. Специалисты за пределами правительства и представители гражданского общества не поддержали это изменение протокола. Они утверждали, что это будет неэффективно, потенциально может поставить под угрозу безопасность приложения, может вызвать проблемы с управлением из-за его глобального масштаба и потенциально может нарушить личные права пользователей. Невозможность прийти к единому мнению вызвала необходимость еще одних слушаний в 2016 г., к которым снова призвал Федеральный Верховный суд, в результате чего в Бразилии начались одни из главных дебатов о шифровании. Суд выбрал примерно двадцать участников из пожелавших участвовать 200 заинтересованных сторон, подавших заявки на участие в дебатах. Среди отобранных участников слушаний были: (1) компании частного сектора (включая WhatsApp, Facebook и других интернет-провайдеров); (2) государственные учреждения, такие как Федеральная полиция Бразилии, Государственная прокуратура, Министерство науки, технологий, инноваций и коммуникаций, Руководящий комитет по Интернету (Internet Steering Committee) и Исследовательская группа по информации и координации Понто БР (NIC.br) (Information and Coordination Study Group of Ponto BR (NIC.br)); (3) ученые (профессора в области вычислительной техники, инженерии и/или информационной безопасности); (4) некоммерческие организации (исследовательские учреждения, специализирующиеся на правовых вопросах, такие как ITS RIO, InternetLab и Lapin-UnB) и (5) представители гражданского общества (ассоциации судей и юристов). Дискуссия только начата. Что достигнуто? Два законодательных акта действительно касаются модернизации систем здравоохранения и устанавливают требование о том, чтобы электронные медицинские записи были защищены шифрованием [85]. Другой аналогичный закон касается способов оплаты и цифровых подписей в электронной торговле, использующих шифрование для обеспечения безопасности транзакций [86]. Наконец, еще один законопроект предусматривает использование шифрования при подаче электронных судебных петиций [87; 88];
(2) обязательная минимальная или максимальная надежность шифрования, в рамках которой национальное законодательство или политика не должны предписывать максимальные стандарты для продуктов и услуг шифрования. Минимальные стандарты могут быть допустимы, если они преследуют законную цель и являются необходимыми и соразмерными (согласно Руководящим принципам Департамента телекоммуникаций Индии (Department of Telecommunications Guidelines) и Общей информации о выдаче лицензии на использование интернет-услуг (General Information for Grant of Licence for Operating Internet Services) поставщики интернет-услуг не могут развертывать «массовое шифрование» (“bulk encryption”) в своих сетях и запрещают пользователям использовать шифрование с длиной ключа более 40 бит без предварительного разрешения. Любой, кто использует более надежное шифрование, обязан предоставить правительству копию ключей шифрования [81. P. 6]. Этот и другие подходы порождают непримиримые дебаты на тему шифрования в Индии [82].
Согласно ст. 24 Закона 2019 г. КНР организации, занимающиеся коммерческим шифрованием, должны соблюдать обязательные национальные стандарты в этой области и свои собственные опубликованные технические стандарты, в дополнение к соблюдению законов и нормативных актов. Этот подход к дерегулированию коммерческого шифрования значительно отличается от подхода, применявшегося в предыдущих правилах шифрования 1999 г. и 2007 г. [88] В соответствии с предыдущими правилами импорт, экспорт, продажа, использование и научные исследования продуктов и технологий шифрования в Китае строго регулировались с помощью ряда разрешений на производство, продажу и использование. В частности, от юридических и физических лиц ранее требовалось использовать только одобренные продукты шифрования, произведенные в Китае, и ни одной организации или физическому лицу не разрешалось распространять или использовать коммерческие продукты шифрования иностранного производства. Исключение было предложено иностранным организациям (в том числе организациям с иностранными инвестициями) и физическим лицам: такие организации и физические лица могли обращаться в SCA для импорта коммерческих продуктов шифрования иностранного производства для собственного использования);
(3) национальное законодательство или политика вправе требовать, чтобы поставщики продуктов или услуг шифрования были лицензированы или зарегистрированы только в том случае, если такие требования преследуют законную цель и являются необходимыми и соразмерными. Пользователей никогда не следует ставить перед требованием наличия лицензии, регистрации или получения разрешения каким-либо другим способом для использования продуктов или услуг шифрования (согласно ст. 30 Закона ЮАР «Об электронных коммуникациях и транзакциях» 2002 г. (Electronic Communications and Transactions Act of 2002) [82. P. 8] требуется, чтобы все поставщики криптографии регистрировали свою контактную информацию и описание своих криптографических продуктов или услуг в правительстве. Это требование распространяется только на компании, которые разрабатывают продукты или услуги шифрования, и в нем конкретно говорится, что они не обязаны раскрывать какую-либо конфиденциальную информацию или коммерческую тайну;
(4) контроль за импортом/экспортом, в рамках которого национальное законодательство или политика должны устанавливать ограничения или условия на импорт или экспорт продуктов или услуг шифрования только в том случае, если они преследуют законную цель и являются необходимыми и соразмерными (согласно Постановлению Государственного совета КНР № 273 «Регулирование коммерческих кодов шифрования» (State Council Order No. 273 “Regulation of Commercial Encryption Codes”) предусматривается, что для импорта и экспорта любого продукта шифрования требуется лицензия Национальной комиссии по регулированию кодов шифрования (National Commission on Encryption Code Regulations), а согласно Закону 2019 г. государство поощряет исследования, академический обмен, воплощение в жизнь научных разработок в сфере коммерческой криптографии, однако научные исследования, коммерческие продажи, оказание услуг и их экспорт не должны наносить ущерба национальной безопасности и общественным интересам, нарушать права и ущемлять интересы других людей. При этом согласно ст. 28 Закона 2019 г. устанавливается система лицензирования импорта и экспортного контроля, которая регулирует (i) импорт коммерческого шифрования, которое «может повлиять на национальную безопасность или общественные интересы» и «обеспечивает функцию защиты шифрования», и (ii) экспорт коммерческого шифрования, который «может повлиять на национальную безопасность или общественные интересы» или требуется международными обязательствами Китая. Список объектов коммерческого шифрования в рамках этого предписания будет опубликован Министерством торговли совместно с SCA и Главным таможенным управлением в неуказанный более поздний срок;
(5) обязательства поставщиков услуг по оказанию помощи органам власти, в рамках которых национальное законодательство или политика не должны требовать, чтобы частные организации помогали государственным органам получать доступ к содержимому зашифрованных сообщений. Если законодательство включает такие требования, они должны быть разрешены только тогда, когда это преследует законную цель, является необходимым и соразмерным (согласно ст. 18 Закона Китая «О борьбе с терроризмом» (Anti-Terrorism Law 2015 as amended 2018 (URL: https://www.appinchina.co/government-documents/anti-terrorism-law-of-the-peoples-republic-of-china/ (дата обращения: 09.09.2021))), предусматривает, что операторы связи и провайдеры интернет-услуг «должны предоставлять технические интерфейсы, дешифровку и другую техническую поддержку органам общественной и государственной безопасности, осуществляющим предотвращение и расследование террористической деятельности в соответствии с законом». Никаких ограничений, гарантий и надзора не существует, за исключением того, что эти положения применяются только в отношении «предотвращения и расследования террористической деятельности». Согласно Закону 2019 г. КНР госучреждениям (и чиновникам) стало запрещено требовать у коммерческих разработчиков раскрытия эксклюзивной информации об их алгоритмах, а также предписывается хранить доверенную им коммерческую тайну [61]. В Индии ст. 69 Закона «Об информационных технологиях» 2000 г. (Information Technology Act of 2000, далее – Закон об ИТ) наделяет центральное правительство и правительства штатов полномочиями предписывать любому правительственному учреждению (any government agency) перехватывать, отслеживать или расшифровывать или вызывать перехват, мониторинг или расшифровку любой информации, передаваемой, получаемой или хранящейся с помощью любых компьютерных ресурсов. Правительство должно следить за тем, чтобы «это по необходимости или из целесообразности происходило в интересах суверенитета или целостности Индии, обороны Индии, безопасности государства, дружественных отношений с иностранными государствами или поддержания общественного порядка, либо для предотвращения подстрекательства к совершению любого преступления, связанного с вышеуказанным, при совершении которого офицер полиции вправе произвести арест без ордера согласно Приложению Первому (First Schedule) к Уголовно-процессуальному кодексу Индии 1973 г. (Code of Criminal Procedure 1973 [89], далее – УПК Индии) или любому иному действующему закону страны (cognizable offence), или для расследования любого преступления. В результате любое правительственное учреждение может потребовать от любого «подписчика или посредника или любого лица, отвечающего за компьютерный ресурс», «предоставить все средства и техническую помощь», необходимые для перехвата, мониторинга или расшифровки информации. Невыполнение этого требования является уголовным преступлением, наказуемым лишением свободы на срок до семи лет, штрафом или и тем, и другим. Ограничения и гарантии здесь минимальны и связаны исключительно с тем, что правительство убеждено в том, что такие меры «необходимы или целесообразны» в отношении указанного перечня целей [82. P. 12].
Что можно сказать в плане практического использования этих положений? С 2008 г. правительство Индии оказывало давление на производителя Blackberry Research in Motion (RIM), чтобы он расшифровывал сообщения по требованию или передавал их ключ. RIM столкнулась с аналогичными мерами в Саудовской Аравии и Объединенных Арабских Эмиратах. Кампания против RIM была больше направлена на обеспечение соблюдения индийской юрисдикции в отношении иностранной компании, чем на риски национальной безопасности, связанные с шифрованием. Существует два вида услуг Blackberry. Для компаний RIM устанавливает локальный сервер Blackberry Enterprise Server (BES), и электронные письма сотрудников направляются через BES с помощью надежного шифрования. В большинстве случаев RIM не имеет ключа и не может расшифровать сообщения BES. В любом случае отмечается [82], что террористы не являются сотрудниками, они не пользуются услугами BES. Для частных лиц у RIM есть незашифрованная сеть Blackberry Internet Service (BIS). Скорее всего, именно так могли общаться все, кто потенциально представляет угрозу безопасности и использует Blackberrys. Электронные письма BIS могут быть перехвачены в виде открытого текста при условии, что местный оператор связи удалит любое добавленное им шифрование транспортного уровня. Мгновенные сообщения через приложение Blackberry Messenger (BBM) передаются на основе уникальных номеров, специфичных для устройства (PIN-код). Обмен сообщениями на основе уникальных номеров, специфичных для устройства (PIN to PIN messaging) - еще один вариант общения для элементов, создающих угрозу, - сквозно не шифруется, а шифруется с помощью одного глобального ключа [90; 91]. Такие сообщения легко перехватить и перенаправить на третий Blackberry. По сути, если правительство хотело перехватить чьи-либо сообщения BIS, оно могло делать это в соответствии с индийским законодательством. Достаточно иметь судебный приказ о перехвате (an interception order) в соответствии со ст. 69 Закона об ИТ, читаемого в соответствии с правилом 3 Правил об информационных технологиях (Процедура и гарантии перехвата, мониторинга и расшифровки информации) 2009 г. (Information Technology (Procedure and Safeguards for Interception, Monitoring, and Decryption of Information) Rules, 2009), или со ст. 5(2) Закона «Об индийском телеграфе» 1885 г. (Indian Telegraph Act, 1885), читаемого в соответствии с правилом 419A Правил «Об индийском телеграф» 1951 г. (Indian Telegraph Rules, 1951). С другой стороны, если бы, гипотетически, сервер BIS находился в Индии, то доступ к данным на нем государству можно было бы обеспечить в соответствии со ст. 91 УПК Индии (как это сделало в 2014 г. Центральное бюро расследований (Central Bureau of Investigation)). Почему же при этих альтернативных возможностях правительство занялось RIM? Возможно, это стремление продемонстрировать жесткую линию в области безопасности, а Blackberry - культовый бренд. Именно так главный исполнительный директор RIM расценил эти действия в 2011 г. [92] Скорее всего, правительство хотело, чтобы RIM установила зеркальные серверы в Индии, чтобы удовлетворить свои претензии по поводу локализации данных. В ответ RIM одновременно подчеркнула, что «решение», которое она предоставила индийскому правительству, не связано с ее платформой BES, а касается только ее незашифрованной сети BIS. Есть ли в Индии прокси-сервер BIS? Вероятно, нет, поскольку последствия для RIM перевешивают любые выгоды пребывания на индийском рынке. Перенаправляет ли RIM весь индийский трафик со своего иностранного сервера BIS в Индию? Возможно. Гарантировала ли RIM, что положительно ответит на каждый правительственный запрос о целевых данных BIS? Наиболее вероятно, что да, но, как показано выше, правительство и так имело к нему технологический доступ [82], так стоила ли игра свеч?
Согласно ст. 21 Закона ЮАР «О перехвате сообщений и предоставлении информации, связанной с коммуникациями» 2002 г. [93] (далее – Закон о перехвате сообщений) сотрудник правоохранительных органов, пожелавший получить ключ дешифрования южноафриканской организации, зарегистрированной в Министерстве связи, вправе это сделать. По сути, в этой статье рассматриваются различные требования, которые необходимо соблюдать, чтобы подать заявку на доступ к ключу расшифровки или, в качестве альтернативы, к руководству к дешифрованию (alternatively a decryption direction). Так, южноафриканский Закон о перехвате сообщений, по-видимому, ищет рамки, с помощью которых отдельные данные могут быть перехвачены и дешифрованы в случае, когда это оправдано. Например, руководство к дешифрованию может быть выдано только: (a) если соответствующий назначенный судья (a designated judge concerned) удовлетворен фактами, изложенными в соответствующем заявлении и подтверждающими факт наличия разумных оснований полагать, что (i) любое косвенное сообщение (indirect communication), к которому применяется соответствующее руководство к перехвату, или любая часть такого косвенного сообщения состоит из зашифрованной информации; (ii) владелец ключа дешифрования, указанный в заявке, владеет зашифрованной информацией и ключом дешифрования к ней; (III) цели, для достижения которых соответствующее руководство к перехвату было выдано были бы не достигнуты полностью или частично, если бы руководство к дешифрованию не было бы выдано; (IV) вступить во владение (to obtain possession) зашифрованной информацией в доступной форме без выдачи руководства к дешифрованию уполномоченным лицом, которое выполняет или помогает с исполнением указанного руководства к дешифрованию, разумно не практикуется (not reasonably practicable); (b) после того, как соответствующий назначенный судья рассмотрел и учел (I) степень и характер любой другой зашифрованной информации, дополнительной по отношению к зашифрованной информации, в отношении которой выдается руководство к дешифрованию, к которой требуемый ключ также служит ключом (де)шифрования; (II) неблагоприятные последствия, которые может оказать на бизнес держателя ключа шифрования, в отношении которого выдано руководство к дешифрованию. В этой связи этика закона о раскрытии ключей оспаривается на основании прав человека [94];
(6) обязательства физических лиц по оказанию помощи органам власти, согласно которым национальное законодательство или политика не должны предоставлять государственным органам возможность требовать от физических лиц расшифровывать (или помогать в расшифровке) зашифрованные сообщения. Опять же, если законодательство действительно включает такие требования, они должны быть разрешены только тогда, когда это преследует законную цель и является необходимым и соразмерным [82].
Вместе с тем, отмечается [95], что также важны решения, принимаемые на международных форумах, от органов ООН (Генеральной Ассамблеи ООН, Совета ООН по правам человека и Специальных процедур ООН) до Группы семи (G7) и Группы 20 (G20), которые также могут играть важную роль в формировании норм, касающихся шифрования.
Если посмотреть на этот вопрос в международно-правовой ретроспективе, увидим следующее. Международные соглашения о контроле за криптографическим программным обеспечением восходят ко временам Координационного комитета по многостороннему экспортному контролю (Coordinating Committee for Multilateral Export Controls, COCOM) - международной организации, нацеленной на контроль за распространением (включая экспорт) технических данных и продукции военного и двойного назначения. Членами COCOM являлись 17 стран - Австралия, Бельгия, Германия, Греция, Дания, Италия, Испания, Канада, Люксембург, Нидерланды, Норвегия, Португалия, Соединенное Королевство, Соединенные Штаты, Турция, Франция и Япония. В качестве сотрудничающих членов в COCOM вошли Австрия, Венгрия, Ирландия, Новая Зеландия, Польша, Сингапур, Словакия, Тайвань, Финляндия, Швеция, Швейцария и Южная Корея. В 1991 г. когда на полках магазинов США, Европы и Азии все чаще предлагались к продаже программы, позволяющие реализовать различные криптографические алгоритмы, COCOM признала невозможность успешно контролировать экспорт криптографического программного обеспечения. В результате организацией был разрешен экспорт программного обеспечения для криптографии массового спроса (mass-market cryptography software) и программного обеспечения, представляющего собой общественное достояние (public domain software). Несмотря на то, что решения COCOM имели рекомендательный характер, большинство стран-членов COCOM (кроме США) следовали им, однако в марте 1994 г. COCOM прекратила свою деятельность.
Начатые в 1995 г. обсуждения нового режима контроля за экспортом обычных вооружений и товаров и технологий двойного назначения [96] завершились подписанием летом 1996 г. Вассенаарскиих договоренностей (далее – ВД) 31 страной. В их числе: Австралия, Австрия, Англия, Аргентина, Бельгия, Венгрия, Германия, Греция, Дания, Ирландия, Испания, Италия, Канада, Корея, Чехия, Люксембург, Нидерланды, Новая Зеландия, Норвегия, Польша, Португалия, Россия, Румыния, Словакия, США, Турция, Финляндия, Франция, Швейцария, Швеция и Япония. Сейчас в ВД участвует 41 страна [96]. Из числа стран БРИКС это РФ и ЮАР. Участники ВД обязались на национальном уровне контролировать экспорт согласно всей номенклатуре по спискам вооружений, товаров и технологий двойного применения. При этом прерогативой каждого из участников является принятие решений о передаче или об отказе в этом любого товара. Все меры, предпринимаемые участниками согласно ВД, отвечают национальной политике и законодательству. Однако списки содержат также не отвечающие профилю ВД некоторые положения (по химии, биологии и др.) из списка COCOM. Последний отражал исключения COCOM для программного обеспечения для криптографии массового рынка и программного обеспечения, являющегося общественным достоянием. В декабре 1998 г. эти ограничения были расширены.
Параллельно на региональном уровне 11 сентября 1995 г. Советом Европы в рамках решения уровне общеполитических вопросов в ЕС на межправительственном была принята Рекомендация R (95) 13 о решении проблем уголовно-процессуального законодательства применительно к информационными технологиям [97] с использованием мер, минимизирующих негативные последствия применения криптографии при расследовании уголовных преступлений, но не затрагивающих законное применение криптографии в большей степени, чем это необходимо.
Европейский союз практически прекратил регулирование перевозок криптографических объектов по странам ЕС в 2000 г. после того, как Регламентом Совета (ЕС) № 1334/2000 был установлен единый режим сообщества по контролю за экспортом предметов и технологий двойного назначения [98], при этом некоторые объекты - устройства криптоанализ - продолжали регулироваться. Экспорт в ряд стран (Австралия, Венгрия, Канада, Новая Зеландия, Норвегия, Польша, США, Швейцария, Чехия, Япония) - требует Общего разрешения Сообщества на экспорт (Community General Export Authorization, CGEA); а экспорт в другие страны требует Общую национальную лицензию на экспорт в конкретную страну (General National License for export to a specific country).
В настоящее время Регламент Совета (ЕС) № 428/2009 от 05.05.2009 является основным правовым актом ЕС, регламентирующим порядок экспорта товаров двойного назначения и устанавливающим единый режим контроля за экспортом, передачей, транзитом товаров двойного назначения и брокерской деятельностью в отношении товаров двойного назначения [99; 100. С. 44–56].
На уровне Евразийского экономического союза (далее – ЕАЭС) ввоз и вывоз с территории ЕАЭС оборудования, предназначенного для шифровально-криптографических функций, является ограниченным. Основной документ, регулирующий трансграничное перемещение шифровальных средств, это - Решение Коллегии ЕЭК от 21 апреля 2015 г. № 30 (URL: https://www.garant.ru/products/ipo/prime/doc/70884966/ (дата обращения: 10.09.2021)), точнее п. 2.19 Приложения № 2 к этому Решению и Приложение № 9 к этому Решению «Положение о ввозе на таможенную территорию Евразийского экономического союза и вывозе с таможенной территории Евразийского экономического союза шифровальных (криптографических) средств».
Для прохождения таможенной процедуры для шифровально-криптографических средств необходимо оформить: (1) лицензию или нотификацию при импорте или экспорте; (2) при ввозе продукции для собственных нужд (то есть без целей распространения, переработки, оказания услуг шифрования, временного ввоза/вывоза, использования свободной таможенной зоны и свободного склада, реэкспорта или реимпорта) –разрешительный документ (заключение) или нотификацию.
Подходов иных интеграционных объединений с участием стран БРИКС в этом вопросе автору обнаружить не удалось.
Изложенное позволяет заключить следующее.
1. Применяемые на практике в настоящее время способы шифрования, по сути, основаны на методах, использующих специальные математические алгоритмы, встроенные в компьютерное программное обеспечение. При этом надежность (уязвимость) методов шифрования зависит от характера и ценности защищаемой информации. На примере уязвимостей применения беспилотных летательных аппаратов продемонстрирована необходимость использования криптографических методов защиты информации стратегического военного характера, получаемой не только этими аппаратами, но наземными пунктами управления ими.
2. Математическая природа алгоритмов современных методов шифрования является существенным, но преодолимым препятствием для получения не только защиты авторским правом, но и патентной.
Это препятствие, ранее имевшее место во всех правопорядках стран БРИКС и США (основателя компьютерной индустрии), преодолевалось установлением акцента в формуле изобретения не на исходный код (защищаемый авторским правом) или алгоритм шифрования, а на «устройство» («продукт», «средство, предназначенное для …») или «способ» («метод», «процесс») шифрования, которые представляют собой новые технические решения или достигают новых технических эффектов.
3. Развитие информационной (компьютерной, цифровой) индустрии породило эволюцию национальных правопорядков в части обеспечения информационной безопасности путем поощрения развития национального криптографического и программного обеспечения и его обеспечения защитой в настоящее время патентным правом при определенных условиях. В странах БРИКС эти изменения в правопорядках выражены в следующем:
- В Бразилии разрешено патентование трех процессов, использующих или физические величины для создания (1) физического эффекта или материального продукта и (2) нематериального продукта, или абстрактные величины для создания (3) одного виртуального продукта путем преобразования другого виртуального продукта, хранящегося на устройстве. что подразумевает шифрование, сжатие данных, управление базами данных, протоколы передачи данных.
- В России алгоритмы сжатия или шифрования информации признаются изобретением, если они решают проблемы соответственно хранения на носителе и передачи в канале связи. Патент в РФ защищает логику работы компьютерной программы в цепочке «назначение – признаки – технический результат» и выдается на технические решения, относящиеся к способу (процессу) действий материальных средств над материальным объектом (например, работы IT-системы, передачи или обработки информации, управления аппаратно-программным комплексом).
- В Индии «изобретение» означает новый продукт или процесс, предполагающий наличие изобретательского уровня (технического продвижения вперед) и возможность промышленного применения. Не подлежат патентованию компьютерная программа «как таковая» или математические методы и алгоритмы независимо от заявляемых в формуле изобретения форм (способ/процесс, устройство/система/устройство, программный продукт для ЭВМ/ машиночитаемый носитель). Однако, изобретения, включающие математические формулы, в результате которых создаются системы кодирования, снижения шума в системах связи/ электрических/электронных системах или шифрования/ дешифрования электронных сообщений являются исключением из этого запрета и патентоспособны.
- В настоящее время в КНР Закон «О шифровании» (2019 г.) обеспечил правовую защиту интеллектуальной собственности на криптографические способы и технологии, а Руководящие принципы патентной экспертизы (2017 г.) сформулировали условия патентования математических правил и алгоритмов не «как таковых», а используемых для шифрования или для программного обеспечения на машиночитаемом носителе, содержащем инструкции по выполнению технического метода.
- В ЮАР не подлежат патентованию «как таковые» научные теории; математические методы; схемы, правила или методы выполнения умственного действия; компьютерные программы или представления информации, но при соответствии критериям патентоспособности (новизна - изобретательский шаг - пригодность к практическому использованию или применению) заявки могут подаваться на патентование устройства, способа, носителя данных и/или формы программного продукта для ЭВМ.
4. Соотнесение эффективности обеспечения информационной безопасности с помощью только запатентованного шифрования или с применением дополнительно к последнему защиты на основании положений о коммерческой тайне продемонстрировало полную нецелесообразность такой защиты, поскольку практика показала, что все успешные способы шифрования (их исходный код) все равно за короткий период времени становятся публичным достоянием посредством Интернета.
5. В целях обеспечения надежности и доступности шифрования во всем мире могут быть сформулированы шесть принципов, которые следует учитывать в национальных законодательствах всех стран:
- общее право на использование продуктов и услуг шифрования для защиты информации, которая не считается государственной тайной, - личных данных граждан, юридических лиц и организаций. Например, в Бразилии законами установлены требования защиты шифрованием электронных медицинских записей, способов оплаты и цифровых подписей в электронной торговле, а в КНР закон разрешает коммерческое шифрование;
- установление обязательной минимальной и максимальной надежности шифрования, за пределами которой не должны предписываться иные стандарты для продуктов и услуг шифрования. Например, в Индии пользователям интернет-услуг запрещено производить шифрование с длиной ключа более 40 бит без предварительного разрешения и предоставления правительству копии ключей шифрования, а в Китае коммерческое шифрование (дополнительно к соблюдению правовых актов) должно отвечать и обязательным национальным, и своим собственным опубликованным техническим стандартам;
- поставщики продуктов или услуг шифрования должны быть лицензированы или зарегистрированы. Например, в ЮАР все поставщики криптографии регистрируют свою контактную информацию и описание своих криптографических продуктов или услуг (без раскрытия конфиденциальной информации или коммерческой тайны) в правительстве;
- контроль за импортом/экспортом продуктов или услуг шифрования в целях предотвращения ущерба национальной безопасности и общественным интересам, и нарушения прав и ущемления интересов других людей должен (согласно закону КНР) осуществляться также с помощью системы лицензирования;
- в целях предотвращения и расследования террористической деятельности частные организации, применяющие криптографические способы защиты информации, обязаны помогать государственным органам получать доступ к содержимому зашифрованных сообщений (Китай) или правительство наделяется полномочиями предписывать любому правительственному учреждению перехватывать, отслеживать и расшифровывать любую информацию (Индия). Например, в ЮАР ключ дешифрования южноафриканской организации, зарегистрированной в Министерстве связи, вправе получить сотрудник правоохранительных органов при соблюдении определенных процедур;
- государственные органы не должны требовать от физических лиц расшифровывать (или помогать в расшифровке) зашифрованные сообщения без законной необходимой и соразмерной цели.
6. Контроль за криптографическим программным обеспечением осуществлялся и осуществляется в рамках международных соглашений за распространением технических данных и продукции военного и двойного назначения, участники которых обязались контролировать экспорт на национальном уровне с сохранением за собой прерогативы принятия решений о передаче или об отказе в этом для любого товара из списка вооружений, товаров и технологий двойного применения.
При этом такие интеграционные объединения стран, как ЕС и Евразийский экономический союз (ЕАЭС) установили единый режим по контролю за ввозом и вывозом со своей территории криптографического оборудования с помощью различных разрешительных систем: в ЕС это Общая национальная лицензия или Общее разрешение Сообщества соответственно в зависимости от предмета экспорта или страны, принимающей его; в ЕАЭС – это либо нотификация или лицензия (при экспорте-импорте), либо нотификация или разрешительный документ (заключение) при ввозе продукции для собственных нужд.
References
1. Érik van der Vyver. Protection of Software and Computer Implemented Inventions. March 2008. – 34 p. URL: http://www.rci.uct.ac.za/usr/rcips/ip/compinv.pdf (data obrashcheniya: 11.09.2021)
2. Alferov A.P., Zubov A.Yu., Kuz'min A.S., Cheremushkin A.V. Osnovy Kriptografii.-M.: Gelios, 2005. – S. 5-53.
3. Zhel'nikov V. Kriptografiya ot papirusa do komp'yutera.-M.: ABF, 1996. URL: https://textarchive.ru/c-1905418-pall.html (data obrashcheniya: 21.08.2021)
4. What Are the Different Types of Encryption? / HP Online Store. December 04, 2020. URL: https://www.hp.com/in-en/shop/tech-takes/post/what-are-the-different-types-of-encryption (data obrashcheniya: 08.09.2021)
5. Charles H. Bennett, Francois Bessette, Gilles Brassard, Louis Salvail, and John Smolin. Experimental Quantum Cryptography. August 2015. Journal of Cryptology 5(1). DOI: 10.1007/3-540-46877-3_23 URL: https://www.researchgate.net/publication/2630685_Experimental_Quantum_Cryptography (data obrashcheniya: 21.08.2021)
6. Artur K. Ekert. Quantum Cryptography Based on Bell's Theorem. // Phys. Rev. Lett. 1991. Vol. 67. Num. 6. P. 661-663. URL: https://cqi.inf.usi.ch/qic/91_Ekert.pdf (data obrashcheniya: 21.08.2021)
7. Bennett, C.H., “Quantum cryptography using any two non-orthogonal states”, Phys. Rev. Letts. 68, pp. 3121-3124, 1992.
8. Zapechnikov S.V. Kriptograficheskie metody zashchity informatsii: ucheb. posobie dlya akademicheskogo bakalavriata / S.V. Zapechnikov, O.V. Kazarin, A.A. Tarasov.-M.: Izdatel'stvo Yurait, 2018. — 309 s.-(Seriya: Bakalavr. Akademicheskii kurs). URL: https://mx3.urait.ru/uploads/pdf_review/C95081E2-D817-463F-B5DB-49FE1912DF90.pdf (data obrashcheniya: 10.09.2021)
9. Quantum computers will disrupt existing systems. URL: https://www.huawei.com/za/trust-center/post-quantum-cryptography (data obrashcheniya: 11.09.2021)
10. Uchenye iz Rossii obnovili mirovoi rekord v oblasti kvantovoi kriptografii. 17.02.2021. URL: https://ria.ru/20210217/rekord-1597773434.html (data obrashcheniya: 22.08.2021)
11. Uchenye nashli sposob povysit' bezopasnost' kvantovoi kriptografii. 06 aprelya 2020. URL: https://www.cnews.ru/news/line/2020-04-06_uchenye_nashli_sposob_povysit (data obrashcheniya: 22.08.2021)
12. Rossiiskie uchenye znachitel'no povysili bezopasnost' kvantovogo shifrovaniya. 14 apr 2020. URL: https://vk.com/wall-117903599_3826 (data obrashcheniya: 22.08.2021)
13. Kvantovaya kriptografiya / shifrovanie. 2021/02/17. URL: https://www.tadviser.ru/index.php/Stat'ya:Kvantovaya_kriptografiya_(shifrovanie) (data obrashcheniya: 22.08.2021)
14. Lyubashevskii V. Kvantovo-bezopasnaya kriptografiya. // «Kommersant'' Nauka».-№6 ot 24.03.2020.-S. 33. URL: https://www.kommersant.ru/doc/4292008 (data obrashcheniya: 22.08.2021)
15. Belikova K.M. Razvitie iskusstvennogo intellekta v Brazilii: aktsent na voennuyu sferu i voprosy intellektual'noi sobstvennosti // Pravo i politika. – 2021. – № 10. – S. 1-21. DOI: 10.7256/2454-0706.2021.10.36096 URL: https:// nbpublish.com/library_read_article.php?id=36096 (data obrashcheniya: 16.07.2021)
16. Belikova K.M. Napravleniya i perspektivy razvitiya i primeneniya iskusstvennogo intellekta v voennoi sfere v YuAR // Pravo i politika. – 2021. – № 9. DOI: 10.7256/2454-0706.2021.9.36076 URL: https://nbpublish.com/library_read_article.php?id=36076 (data obrashcheniya: 10.07.2021)
17. Belikova, K. M. (2021). Marco legal para o uso da inteligência artificial na esfera militar da Índia no contexto da proteção dos direitos de patente (Legal framework for the use of artificial intelligence in India’s military sphere in the context of patent rights protection). Laplage Em Revista, 7(2), p.671-690. https://doi.org/10.24115/S2446-62202021721051p.671-690 URL: https://laplageemrevista.editorialaar.com/index.php/lpg1/article/view/1051 (data obrashcheniya: 06.07.2021)
18. Belikova K.M. Osnova pravovogo regulirovaniya razvitiya i primeneniya iskusstvennogo intellekta v voennoi sfere Kitaya v kontekste gosudarstvennoi strategii i okhrany avtorskikh i patentnykh prav. // Probely v rossiiskom zakonodatel'stve. 2020. T. XIII. №5. S. 223-234.
19. Shurkhovetskii G.N. Kriptostoikost' algoritmov shifrovaniya [Elektronnyi resurs] / G.N. Shurkhovetskii // Molodaya nauka Sibiri: elektron. nauch. zhurn. – 2018. – №2. – Rezhim dostupa: http://mnv.irgups.ru/toma/22-2018, svobodnyi. – Zagl. s ekrana. – Yaz. rus., angl. (data obrashcheniya: 06.08.2021)
20. Bruce Schneier. Why Cryptography Is Harder Than It Looks. // Information Security Bulletin. 1997. URL: https://www.schneier.com/essays/archives/1997/01/why_cryptography_is.html (data obrashcheniya: 06.08.2021)
21. Aktual'nye voprosy obespecheniya kiberbezopasnosti bespilotnykh letatel'nykh apparatov. // Voennoe obozrenie. 10.01.2016. URL: http://militaryreview.ru/aktualnye-voprosy-obespecheniya-kiberbezopasnosti-bespilotnyx-letatelnyx-apparatov.html (data obrashcheniya: 13.08.2021)
22. Glavnoe o bezopasnosti dronov. URL: https://www.kaspersky.ru/resource-center/threats/can-drones-be-hacked (data obrashcheniya: 13.08.2021)
23. Testova A. Chto ugrozhaet blokchein-setyam: rassmatrivaem ataki i sposoby zashchity. 15 yanvarya 2018. URL: https://habr.com/ru/company/bitfury/blog/346656/ (data obrashcheniya: 11.08.2021)
24. Allouch, A.; Cheikhrouhou, O.; Koub, A.; Toumi, K.; Khalgui, M.; Nguyen Gia, T. UTM-Chain: Blockchain-Based Secure Unmanned Traffic Management for Internet of Drones. Sensors 2021, 21, 3049. https://doi.org/10.3390/s21093049 URL: https://www.mdpi.com/1424-8220/21/9/3049 (data obrashcheniya: 13.08.2021)
25. Jerbi, W.; Guermazi, A.; Cheikhrouhou, O.; Trabelsi, H. CoopECC: A Collaborative Cryptographic Mechanism for the Internet of Things. J. Sensors 2021, 2021, 8878513
26. Md Samsul Haque, Morshed U. Chowdhury. A New Cyber Security Framework Towards Secure Data Communica-tion for Unmanned Aerial Vehicle (UAV). // Security and Privacy in Communication Networks. Serie “Lecture Notes of the Institute for Computer Sciences”. October 2018. P. 113-122. DOI: 10.1007/978-3-319-78816-6_9. URL: https://www.researchgate.net/publication/324722005_A_New_Cyber_Security_Framework_Towards_Secure_Data_Communication_for_Unmanned_Aerial_Vehicle_UAV (data obrashcheniya: 13.08.2021)
27. Popov N.I., Efimov S.V. K voprosu obespecheniya informatsionnoi bezopasnosti bespilotnykh aviatsionnykh sistem s letatel'nymi apparatami malogo i legkogo klassa v spetsializirovannykh ASU. // T-Comm-Telekommunikatsii i Transport. – 2013. URL: https://masters.donntu.org/2017/etf/nizhenets/library/article3.htm (data obrashcheniya: 05.08.2021)
28. Jean-Paul Yaacoub, Hassan Noura, Ola Salman, Ali Chehab. Security analysis of drones systems: Attacks, limitations, and recommendations. // Internet of Things. Volume 11, September 2020, 100218. P. 3 (1-40). URL: https://www.ncbi.nlm.nih.gov/pmc/articles/PMC7206421/pdf/main.pdf (data obrashcheniya: 11.08.2021).
29. Tutubalin P.I., Kirpichnikov A.P. Obespechenie informatsionnoi bezopasnosti funktsionirovaniya kompleksov bespilotnoi razvedki. // Vestnik tekhnologicheskogo universiteta.-2017.-T.20.-№ 21. – S. 86-92.
30. Sputnikovyi shpionazh. // Khaker. 07.03.2008. URL: https://xakep.ru/2008/03/07/42680/ (data obrashcheniya: 13.08.2021)
31. Patrick T. Muffo. The Patentability of Encryption Inventions. Oct 27, 2015. URL: https://www.seyfarth.com/news-insights/the-patentability-of-encryption-inventions.html (data obrashcheniya: 08.09.2021)
32. Martin Campbell-Kelly, Not All Bad: An Historical Perspective on Software Patents, 11 Mich. Telecomm. & Tech. L. Rev. 191 (2005). Available at: http://repository.law.umich.edu/mttlr/vol11/iss2/2 (data obrashcheniya: 11.09.2021)
33. Simson Garfinkel. 4.4. Legal Restrictions on Cryptography. // Web Security, Privacy & Commerce. O'Reilly Media, Inc. 2nd Ed. 2001. – P. 118 (877 p.) https://www.oreilly.com/library/view/web-security-privacy/0596000456/ch04s04.html (data obrashcheniya: 06.09.2021)
34. Yevgeniy Sverdlik. IBM scientists patent homomorphic encryption method. December 20, 2013. URL: https://www.datacenterdynamics.com/en/news/ibm-scientists-patent-homomorphic-encryption-method/ (data obrashcheniya: 08.09.2021)
35. Greg Vetter, Patenting Cryptographic Technology, 84 Chi.-Kent L. Rev. 757 (2010). Available at: https://scholarship.kentlaw.iit.edu/cklawreview/vol84/iss3/5 (data obrashcheniya: 08.09.2021)
36. Quantum cryptography key distribution system and method (US20030169880A1). URL: https://patents.google.com/patent/US20030169880 (data obrashcheniya: 06.09.2021) i dr.
37. Lei 9.279/1996 (Lei Ordinária) 14.05.1996, regula direitos e obrigações relativos a propriedade industrial. // D.O. de 15/05/1996. P. 8353. URL: http://www.planalto.gov.br/ccivil_03/leis/l9279.htm (data obrashcheniya: 10.05.2019)
38. José Roberto Cunha. Articles 10 and 18 of Brazilian IP Law. 11 de May de 2020. URL: https://vlgbrazil.com/news/why-to-register-a-trademark-in-brazil/ (data obrashcheniya: 10.09.2021)
39. Matematika dlya programmista: sovety, razdely, literatura. 19 yanvarya 2018. URL: https://proglib.io/p/how-to-learn-maths (data obrashcheniya: 11.09.2021)
40. Levin A. Kak abstraktnaya matematika pomogaet konkretnoi fizike. 19 dekabrya 2017. URL: https://yandex.ru/turbo/popmech.ru/s/science/13451-bolshie-kalibry-fiziki/ (data obrashcheniya: 10.09.2021)
41. Gustavo Sartori Guimarães. Can you patent a software in Brazil? June 29 2021. URL: https://www.lexology.com/library/detail.aspx?g=a7162f21-2430-4f55-a8c0-e5999f60b8b1 (data obrashcheniya: 10.09.2021)
42. Guidelines for the Examination of Patent Applications Covering Software Implemented Inventions / Ed. by Brazilian PTO (BRPTO). December 29, 2020. Tsit. po: Inventions / VIPmarketing. January 12, 2021. URL: https://www.venturini-ip.com/news/new-brazilian-guidelines-for-the-examination-of-patent-applications-covering-software-implemented-inventions/ (data obrashcheniya: 11.09.2021)
43. Portaria / INPI/ PR № 404 de 28 de Dezembro de 2020. URL: https://www.gov.br/inpi/pt-br/servicos/patentes/legislacao/legislacao/PPHIIPortiaria404de21.12.20RPI2608de29.12.20.pdf (data obrashcheniya: 11.09.2021)
44. Inventions / VIPmarketing. January 12, 2021. URL: https://www.venturini-ip.com/news/new-brazilian-guidelines-for-the-examination-of-patent-applications-covering-software-implemented-inventions/ (data obrashcheniya: 11.09.2021)
45. P. Andrew Riley, Jonathan R.K. Stroud, and Jeffrey Totten. The Surprising Breadth of Post-Grant Review for Covered-Business-Method Patents: A New Way to Challenge Patent. – The Columbia Science & Technology Law Review, Vol. XV, Spring 2014, pages 235–292. Tsit. po: Fedorov S.V. Patentovanie algoritmov komp'yuternykh programm. 2 iyulya 2018 (Mat-ly doklada, sdelannogo avtorom na patentnoi konferentsii «Peterburgskie kollegial'nye chteniya – 2018» 27 iyunya 2018 g.). URL: https://habr.com/ru/post/415789/ (data obrashcheniya: 07.09.2021)
46. Grazhdanskii kodeks Rossiiskoi Federatsii. Chast' chetvertaya Grazhdanskogo kodeksa Rossiiskoi Federatsii ot 18 dekabrya 2006 g. № 230-FZ. Prinyata Gosudarstvennoi Dumoi 24 noyabrya 2006 g. // SZ RF. 2006. № 52 (1 ch.). St. 5496.
47. Prikaz Rospatenta ot 31.12.2009 N 199 Ob utverzhdenii Rekomendatsii po voprosam ekspertizy zayavok na izobreteniya>Prilozhenie. Rekomendatsii po voprosam ekspertizy zayavok na izobreteniya>3. Proverka printsipial'noi patentosposobnosti zayavlennogo v kachestve izobreteniya ob''ekta>Matematicheskie metody. URL: https://sudact.ru/law/prikaz-rospatenta-ot-31122009-n-199-ob/prilozhenie/3/matematicheskie-metody/ (data obrashcheniya: 06.09.2021)
48. Fedorov S.V. Patentovanie algoritmov komp'yuternykh programm. 2 iyulya 2018 (Mat-ly doklada, sdelannogo avtorom na patentnoi konferentsii «Peterburgskie kollegial'nye chteniya – 2018» 27 iyunya 2018 g.). URL: https://habr.com/ru/post/415789/ (data obrashcheniya: 07.09.2021)
49. Sposob shifrovaniya informatsii, predstavlennoi dvoichnym kodom (RU2581772C2). URL: https://yandex.ru/patents/doc/RU2581772C2_20160420 (data obrashcheniya: 06.09.2021)
50. Sposob shifrovaniya dvoichnoi informatsii (RU2701128C1). URL: https://patenton.ru/patent/RU2701128C1 (data obrashcheniya: 06.09.2021)
51. Cposob potochnogo shifrovaniya dannykh (RU2291578C1). URL: https://yandex.ru/patents/doc/RU2291578C1_20070110 (data obrashcheniya: 06.09.2021) i t.d.
52. Patent na sposob / «Gardium». URL: https://legal-support.ru/services/patent/patent-na-sposob/ (data obrashcheniya: 07.09.2021)
53. Bashuk A., Tokarev R. IT-patenty dlya rossiiskikh razrabotchikov softa: pol'za, problemy, podvodnye kamni. 11 noyabrya 2020. URL: https://habr.com/ru/post/527484/ (data obrashcheniya: 08.09.2021)
54. Bashuk A. Kak zashchitit' komp'yuternuyu programmu ot plagiata. Pyat' zakonnykh sposobov. 18.03.20. URL: https://journal.tinkoff.ru/programm-files/ (data obrashcheniya: 08.09.2021)
55. Patents Act, 1970 (The e-Version incorporates all the amendments in the Patents Act, 1970 and the Patent Rules, 2003 and is updated till 11-03-2015). http://www.ipindia.nic.in/writereaddata/Portal/IPOAct/1_31_1_patent-act-1970-11march2015.pdf (data obrashcheniya: 16.02.2020)
56. AIR 1982 SC 1444. Tsit. po: Guidelines for Examination of Computer Related Inventions (CRIs) / Office of the Controller General of Patents, Designs and Trademarks of India. 2017. – P. 9 (18 p.) URL: https://ipindia.gov.in/writereaddata/Portal/IPOGuidelinesManuals/1_86_1_Revised__Guidelines_for_Examination_of_Computer-related_Inventions_CRI__.pdf (data obrashcheniya: 12.09.2021)
57. Reports of Patent, Design and Trade Mark Cases, Volume 83, Issue 14, 7 July 1966, Pages 319–356, https://doi.org/10.1093/rpc/83.14.319 URL: https://academic.oup.com/rpc/article/83/14/319/1600681 (data obrashcheniya: 13.09.2021)
58. Mumbai Central, ... on 7 September, 2012. Tsit. po: Guidelines for Examination of Computer Related Inventions (CRIs) / Office of the Controller General of Patents, Designs and Trademarks of India. 2017. – P. 10 (18 p.). URL: https://ipindia.gov.in/writereaddata/Portal/IPOGuidelinesManuals/1_86_1_Revised__Guidelines_for_Examination_of_Computer-related_Inventions_CRI__.pdf (data obrashcheniya: 12.09.2021)
59. Guidelines for Examination of Computer Related Inventions (CRIs) / Office of the Controller General of Patents, Designs and Trademarks of India. 2017. 18 p. URL: https://ipindia.gov.in/writereaddata/Portal/IPOGuidelinesManuals/1_86_1_Revised__Guidelines_for_Examination_of_Computer-related_Inventions_CRI__.pdf (data obrashcheniya: 12.09.2021)
60. 中华人民共和国密码法 (2019年10月26日第十三届全国人民代表大会常务委员会第十四次会议通过 ). URL: http://www.npc.gov.cn/npc/c30834/201910/6f7be7dd5ae5459a8de8baf36296bc74.shtml (data obrashcheniya: 10.09.2021)
61. V Kitae prinyat zakon o kriptografii / Redaktsiya. 28.10.2019. URL: https://d-russia.ru/v-kitae-prinyat-zakon-o-kriptografii.html (data obrashcheniya: 10.09.2021)
62. Methods and apparatus for cryptography (CN106663389A). URL: https://patents.google.com/patent/CN106663389A/en (data obrashcheniya: 06.09.2021)
63. Patent Law of the People’s Republic of China (as amended up to the Decision of December 27, 2008, regarding the Revision of the Patent Law of the People’s Republic of China). URL: https://wipolex.wipo.int/ru/text/178664 (data obrashcheniya: 06.09.2021)
64. Lin Li, Yujie Jin and Yali Shao. Protecting AI-related innovations in China. June 26 2020. URL: https://www.managingip.com/article/b1m92lbg3th9w0/protecting-ai-related-innovations-in-china (data obrashcheniya: 06.09.2021)
65. Revised Patent Examination Guidelines (I): China Loosening Rules on Patent Invalidation. // Newsletters. March 2017. / Lung Tin IP Attorneys. URL: http://www.lungtin.com/UpLoadFile/Files/2019/5/21/15152074733ac4b32-c.pdf (data obrashcheniya: 09.09.2021)
66. Xiaowei Wei. China: Obtaining Patents for Software-Related Inventions in China. 30 August 2017. URL: https://www.mondaq.com/china/patent/624420/obtaining-patents-for-software-related-inventions-in-china (data obrazshcheniya: 08.09.2021)
67. Li Hui. Patent eligibility for software in China. // China Business Law Journal. 19 June 2019. URL: https://law.asia/china-patent-eligibility-software/ (data obrashcheniya: 08.09.2021)
68. Dragileva I.P. Patentovanie komp'yuternykh programm i metodov predprinimatel'stva v stranakh Azii. // Patentnoe delo. – 2011.-№ 5. – S. 12-15.
69. Amy Bray. April 1, 2017 Revision of Chinese Patent Examination Guidelines May be Good News for Patentees. // The National Law Review. May 8, 2017. Volume VII, Number 128. URL: https://www.natlawreview.com/article/april-1-2017-revision-chinese-patent-examination-guidelines-may-be-good-news (data obrashcheniya: 09.09.2021)
70. Patents Act, 1978 [Act No; 57, 1978]. // Government Gazette. Cape Town, 17 May 1978. Vol. 155. No. 6012. URL: https://www.gov.za/sites/default/files/gcis_document/201504/act-57-1978.pdf (data obrashcheniya: 06.05.2019)
71. Inventions which cannot be Patented in South Africa / Smit & Van Wyk. URL: https://www.svw.co.za/patents/patent-exclusions/ (data obrashcheniya: 06.09.2021)
72. Guidelines for Examination in the European Patent Office. March 2021 edition. // OJ EPO 2021, A6. URL: https://www.epo.org/law-practice/legal-texts/guidelines.html i http://documents.epo.org/projects/babylon/eponet.nsf/0/C4B20952A0A7EF6BC125868B002A5C61/$File/epo_guidelines_for_examination_2021_hyperlinked_en.pdf (data obrashcheniya: 11.07.2021)
73. Peregudova Yu.B. Okhranosposobnost' reshenii, otnosyashchikhsya k metodam khozyaistvennoi ili intellektual'noi deyatel'nosti. Diss. kand. yurid. nauk. M., 2006. – 185 s.
74. Tazetdinova L.D. O patentovanii programmnogo obespecheniya (sravnitel'nyi analiz RF i zapadnykh stran). // Voprosy rossiiskogo i mezhdunarodnogo prava. – 2018.-№ 9A. – S. 360-369.
75. Robert B. Bigelow, Legal Aspects of Proprietary Software, DATAMATION, Oct. 1968, at 32-39.
76. Kak rabotaet "paket Yarovoi". 1 iyul 2018, obnovleno 26 sen 2018. URL: https://tass.ru/ekonomika/5335719 (data obrashcheniya: 09.09.2021)
77. Pochti lyuboi sait mozhet popast' v reestr Roskomnadzora. 08.02.18. URL: https://journal.tinkoff.ru/news/ori/ (data obrashcheniya: 10.09.2021)
78. "Chernyi den' dlya Rossii": Putin podpisal antiterroristicheskii "paket Yarovoi". // Nastoyashchee vremya. 7 iyulya 2016 g. URL: https://www.currenttime.tv/a/27817452.html (data obrashcheniya: 09.09.2021)
79. Shchet'ko N. FSB opredelilas' s trebovaniyami po rasshifrovke dannykh. Pyat' voprosov o tom, chem eto grozit internetu i messendzheram v Rossii. // Nastoyashchee vremya. 16 avgusta 2016 g. URL: https://www.currenttime.tv/a/russia-messengers-fate/27845129.html (data obrashcheniya: 09.09.2021)
80. World map of encryption laws and policies. URL: https://www.gp-digital.org/world-map-of-encryption/# (data obrashcheniya: 08.09.2021)
81. Encryption laws and policies: human rights assessment tool / Ed. Global Partners Digital. December 2020. P. 4. URL: https://www.gp-digital.org/wp-content/uploads/2020/12/encryption-human-rights-assessment-tool.pdf (data obrashcheniya: 09.09.2021)
82. Bhairav Acharya. Breaking ranks with Asia: The case for encrypting India. Feb 21 2017. URL: https://www.orfonline.org/expert-speak/breaking-ranks-with-asia-the-case-for-encrypting-india/ (data obrashcheniya: 12.09.2021)
83. China Enacts Encryption Law. October 31, 2019. URL: https://www.cov.com/-/media/files/corporate/publications/2019/10/china_enacts_encryption_law.pdf (data obrashcheniya: 10.09.2021)
84. Gabriel Aleixo, Andrea Guimaraes Gobbato, Natalia Langennegger, Ronaldo Lemos, Isabela Garcia de Souza, and Fabro Steibel. The Encryption Debate in Brazil. May 2019.-Carnegie Endowment for International Peace. – P. 4-5 (15 p.). URL: https://carnegieendowment.org/2019/05/30/encryption-debate-in-brazil-pub-79219 (data obrashcheniya: 10.09.2021)
85. PL 471/2008 i PL 474/2008. Tsit. po: Gabriel Aleixo, Andrea Guimaraes Gobbato, Natalia Langennegger, Ronaldo Lemos, Isabela Garcia de Souza, and Fabro Steibel. Op. cit. P. 7.
86. PL 4906-A/2001. Gabriel Aleixo, Andrea Guimaraes Gobbato, Natalia Langennegger, Ronaldo Lemos, Isabela Garcia de Souza, and Fabro Steibel. Op. cit. P. 7.
87. PL 3279/2012. Gabriel Aleixo, Andrea Guimaraes Gobbato, Natalia Langennegger, Ronaldo Lemos, Isabela Garcia de Souza, and Fabro Steibel. Op. cit. P. 7.
88. Priscilla Silva, Ana Lara Mangeth, and Christian Perrone. The Encryption Debate in Brazil: 2021 Update. March 2021.-Carnegie Endowment for International Peace. – 11 p. URL: https://carnegieendowment.org/2021/03/31/encryption-debate-in-brazil-2021-update-pub-84238 (data obrashcheniya: 11.09.2021) 88. Regulations on Administration of Commercial Encryption (1999); Administrative Rules on the Use of Commercial Encryption Products (2007). Tsit. po: China Enacts Encryption Law. October 31, 2019. URL: https://www.cov.com/-/media/files/corporate/publications/2019/10/china_enacts_encryption_law.pdf (data obrashcheniya: 10.09.2021)
89. CrPC Schedule 1 – The First Schedule. Updated with Criminal Law (Amendment) Act, 2018. URL: http://devgan.in/crpc/chapter_38.php (data obrashcheniya: 09.09.2021)
90. R. Halevy, “FAQ: Blackberry Messenger and PIN Messages are Not Encrypted,” Berry Review, August 6, 2010, http://www.berryreview.com/2010/08/06/faq-blackberry-messenger-pin-messages-are-not-encrypted/ Tsit. po: Bhairav Acharya. Op. cit.
91. C. Parsons, “Decrypting Blackberry Security, Decentralizing the Future,” Citizen Lab, November 29, 2010, https://citizenlab.org/2010/11/decrypting-blackberry-security-decentralizing-the-future/ Tsit. po: Tsit. po: Bhairav Acharya. Op. cit.
92. RIM CEO calls a halt to BBC Click interview. // BBC, April 13, 2011. URL: http://news.bbc.co.uk/2/hi/programmes/click_online/9456798.stm (data obrashcheniya: 13.09.2021)
93. Interception of Communications and Provision of Communication-related Information Act of 2002 (“RICA”). Tsit. po: Ryszard Lisinski. End-To-End Encryption – A South African Perspective. 14 Nov 2016. URL: https://www.golegal.co.za/end-end-encryption-south-african-perspective/ (data obrashcheniya: 11.09.2021)
94. Cory Farmer, Judson L. Jeffries. Telecommunications Surveillance and Cryptography Regulatory Policy in Africa. May 16, 2013. URL: https://apj.hkspublications.org/telecommunications-surveillance-and-cryptography-regulatory-policy-in-africa/ (data obrashcheniya: 12.09.2021)
95. International Forum Pages. URL: https://www.gp-digital.org/series/encryption-policy-hub/international-forums/ (data obrashcheniya: 09.09.2021)
96. Vassenaarskie dogovorennosti (spravka). 6.07.17. URL: https://www.mid.ru/eksportnyj-kontrol/-/asset_publisher/UhKoSvqyDFGv/content/id/80354 (data obrashcheniya: 10.09.2021)
97. Recommendation R (95) 13 Concerning Problems of Criminal Procedure Law Connected with Information Technology (Adopted by the Committee of Ministers on 11 September 1995 at the 543 meeting of the Ministers' Deputies). URL: https://www.aip-bg.org/lichnidanni/pdf/r_95_13.pdf (data obrashcheniya: 10.09.2021)
98. Council Regulation (EC) No 1334/2000 of 22 June 2000 setting up a Community regime for the control of exports of dual-use items and technology. // OJ L 159, 30.6.2000, p. 1–215. URL: https://eur-lex.europa.eu/legal-content/EN/TXT/?uri=CELEX%3A32000R1334 (data obrashcheniya: 10.09.2021) (utratil silu).
99. Council Regulation (EC) No 428/2009 of 5 May 2009 setting up a Community regime for the control of exports, transfer, brokering and transit of dual-use items // OJ L 134. 29.05.2009. P. 1-269. URL: https://eur-lex.europa.eu/legal-content/EN/TXT/?uri=celex%3A32009R0428 (data obrashcheniya: 10.09.2021)
100. Slepak V. Yu. Pravovye osnovy eksporta tovarov dvoinogo naznacheniya iz Evropeiskogo Soyuza // Lex russica.-2021.-T. 74.-№ 1.-S. 44–56. DOI: 10.17803/1729-5920.2021.170.1.044-056
101. Federal'nyi zakon ot 27.07.2006 № 149-FZ "Ob informatsii, informatsionnykh tekhnologiyakh i o zashchite informatsii". // SZ RF ot 31 iyulya 2006 g. № 31 (chast' I) st. 3448)
Link to this article
You can simply select and copy link from below text field.
|
|





