|
MAIN PAGE
> Back to contents
Cybernetics and programming
Reference:
Bashmakov D.A., Prokhozhev N.N., Mikhailichenko O.V., Sivachev A.V.
Application of neighborhood matrices of pixels to improve the accuracy of steganoanalysis of fixed digital images with a homogeneous background
// Cybernetics and programming.
2018. № 1.
P. 64-72.
DOI: 10.25136/2644-5522.2018.1.24919 URL: https://en.nbpublish.com/library_read_article.php?id=24919
Application of neighborhood matrices of pixels to improve the accuracy of steganoanalysis of fixed digital images with a homogeneous background
Bashmakov Daniil Andreevich
graduate student, Department of Design and Security of Computer Systems, St. Petersburg National Research University of Information Technologies, Mechanics and Optics
197101, Russia, Saint Petersburg, ul. Kronverskii, 49, of. 474

|
basme@list.ru
|
|
 |
Other publications by this author
|
|
Prokhozhev Nikolai Nikolaevich
PhD in Technical Science
Associate Professor, St. Petersburg National Research University of Information Technologies, Mechanics and Optics
197101, Russia, g. Saint Petersburg, ul. Kronverskii, 49, of. 474

|
19791109@list.ru
|
|
 |
Other publications by this author
|
|
Mikhailichenko Ol'ga Viktorovna
Senior Lecturer, Department of Design and Security of Computer Systems, St. Petersburg National Research University of Information Technologies, Mechanics and Optics
197101, Russia, Sankt-Peterburg, Kronverkskii prospekt, d.49

|
19791109@list.ru
|
|
 |
Other publications by this author
|
|
|
Sivachev Aleksei Vyacheslavovich
graduate student, Department of Design and Security of Computer Systems, St. Petersburg National Research University of Information Technologies, Mechanics and Optics
197101, Russia, Saint Petersburg, Kronverskii prospekt, 49, of. 474

|
sivachev239@mail.ru
|
|
 |
Other publications by this author
|
|
|
DOI: 10.25136/2644-5522.2018.1.24919
Received:
06-12-2017
Published:
27-02-2018
Abstract:
The article consideres the accuracy of the steganoanalysis using the Weighted Stego algorithm in passive data transmission channel countermeasures using the method of embedding the spatial region of fixed digital images with the RGB color model into the smallest significant bit. The dependence of the accuracy of steganoanalysis by the Weighted Stego method on the fraction of a homogeneous background in the analyzed image was studied. The drop in the accuracy of pixel prediction in the background areas of the image is investigated using the prediction model proposed by the authors of the original Weighted Stego algorithm. The Weighted Stego steganoanalysis algorithm is investigated. The basis for the steganoanalysis algorithm is a model for predicting the pixel values of the analyzed image from adjacent pixels. To assess the effectiveness of the analysis, the BOWS2 collection was used. Embedding information is realized by changing the least significant bits of the image in the spatial domain with a payload of 3-5 %%. The effectiveness of the methods is determined taking into account the obtained truly positive, truly negative, false positive and false negative values of the classification of images. The fall in the accuracy of steganoanalysis by the Weighted Stego method is shown with an increase in the fraction of a homogeneous background in the analyzed image. The method of improvement of the pixel prediction model in the basis of Weighted Stego is proposed, which allows to level out the drop in accuracy with increasing the fraction of a homogeneous background in the analyzed image. The results of the work are useful to a specialist in the field of information protection in the tasks of detecting and countering a hidden data channel. The obtained results can be used in the development of steganoanalysis systems based on the Weighted Stego algorithm.
Keywords:
steganography, steganalysis, binary classification, least significant bit, passive countermeasure, statistical steganalysis, image spatial domain, steganalysis method accuracy, steganographic embedding, steganalysis algorithm
This article written in Russian. You can find original text of the article here
.
Введение
В современном информационном пространстве стеганография используется для организации скрытых каналов передачи информации. Широкая область применения скрытых каналов передачи информации обуславливает факт использования стеганографии террористическими организациями и другими криминальными структурами [1, 2]. В целях пассивного противодействия стеганографическим каналам передачи информации разрабатываются методы стеганоанализа, позволяющие определить факт сокрытия информации в контейнере, и, как следствие, факт наличия скрытого канала передачи информации.
Неподвижные цифровые изображения различных форматов являются одним из наиболее распространённых типов стеганографических контейнеров [3]. Существует ряд методов встраивания информации в неподвижное цифровое изображение, равно как и ряд различных методов стеганоанализа для этого типа контейнера. Сокрытие информации в младшие значащие биты пространственного домена изображения является распространённым и простым методом стеганографического встраивания. Несмотря на большое число методов стеганоанализа, ориентированных на этот метод встраивания, универсальных методов, позволяющих эффективно определять факт встраивания вне зависимости от характеристик изображения, не разработано. Например, статистические методы стеганоанализа показывают хорошие результаты при значительных объёмах встраивания, но при малых объёмах оказываются неэффективны [4, 5].
Методы статистического стеганоанализа неподвижных цифровых изображений различаются по используемым характеристикам анализируемого контейнера. Метод Weighted Stego Image (далее – WS) является одним из наиболее эффективных и перспективных с точки зрения модификаций методов этой группы [6, 7].
Эффективность метода стеганоанализа, оцениваемая через параметры точности бинарной классификации, является главным критерием при выборе метода при решении практической задачи пассивного противодействия стеганографическому каналу. В задачах стеганоанализа в пространственной области имеет значение точность при различных характеристиках анализируемого изображения как такового.
Опубликовано множество работ, исследующих зависимость точности стеганоанализа в пространственной области от параметров анализируемого изображения, в том числе, для алгоритма WS. Однако, отсутствуют работы, в которых исследуется зависимость точности стеганоанализа от доли однородного фона в анализируемом изображении. В то же время, однородность пространственного домена может оказывать значительное влияние на точность стеганоанализа.
Цель работы
В работе проводится оценка зависимости точности статистического стеганоанализа алгоритмом WS от доли однородного фона в анализируемом изображении и приводится метод модификации алгоритма WS для улучшения точности стеганоанализа в изображениях со значительной долей однородного фона.
Методика проведения экспериментов
Имеющееся множество тестовых цифровых изображений используется для формирования двух подмножеств: оригинальных изображений и стегоизображений. Множество стегоизображений формируется путём имитирования стеганографического встраивания в пространственную область путём изменения наименьшего значащего бита на противоположный в фиксированном проценте пикселей изображения. После этого для изображений из обоих множеств производится расчёт доли однородного фона. Каждая из выборок, в свою очередь, разделяется на две подвыборки: HB и LB. Выборка HB содержит изображения, в которых доля однородного фона составляет более 40%. Выборка LB содержит изображения, в которых доля однородного фона не превышает 5%. Изображения, не попадающие ни в одну из подвыборок, удаляются из эксперимента. Подвыборки анализируются алгоритмом WS, полученные результаты сохраняются для последующей обработки и сравнения точности анализа в различных подвыборках.
Те же подвыборки используются при анализе модифицированным алгоритмом, предложенным в работе. Результаты сохраняются для последующего сравнения с результатами оригинального алгоритма.
Условия проведения экспериментов
В качестве исходного алгоритма стеганоанализа взята версия алгоритма WS, предложенная авторами алгоритма в [6].
Для проведения экспериментов были выбраны следующие коллекции изображений:
· Коллекция 1 – 50000 изображений, разрешение от 1200х800 до 2100х1800.
· Коллекция 2 – 1000 изображений, разрешение 2400х2400.
· Коллекция 3 – 1200 изображений, разрешение 3750х2940.
Коллекции выбраны из открытого источника изображений BOWS2, широко используемого в работах по стеганографии и стеганоанализу в качестве тестового материала [8, 9].
Моделирование стеганографического встраивания производилось путём изменения значений младших значащих бит пикселей пространственного домена изображения в каждой цветовой плоскости модели RGB по-отдельности.
Способ оценки эффективности методов стеганоанализа
Поскольку система стеганоанализа представляет собой бинарный классификатор, эффективность лежащего в основе системы алгоритма стеганоанализа определяется точностью классификации изображений как оригинальных и стеганограмм. В пределе каждое изображение, не подвергавшееся обработке, классифицируется как оригинальное, а каждое изображение со встроенной информацией – как стеганограмма. Реальный анализатор имеет погрешность, при этом некорректные классификации подразделяются на классы: истинно положительное и истинно отрицательное (далее – TP и TN) – корректные классификации, ложноположительные и ложноотрицательные (FP и FN) – некорректные классификации. Количественно оценить точность стеганоанализа можно как процент некорректной классификации при заданном проценте корректной классификации. Наглядно результат может быть представлен с помощью графика доверительных интервалов.
Способ улучшения точности стеганоанализа
Оригинальный алгоритм WS основывается на предсказании пикселей анализируемого изображения по окружающим пикселям. От точности предсказания пикселей напрямую зависит конечная точность стеганоанализа алгоритмом WS. Метод предсказания, предложенный авторами алгоритма, обладает абсолютной точностью при анализе полностью однородного изображения (все значения пикселей которого одинаковы). В естественной фотографии пиксели, представляющие однородный фон (такой, как облачное небо, поверхность воды и студийный фон) незначительно отличаются друг от друга. При анализе фоновых областей изображения, где значения пикселей изменяются относительно соседних незначительно, ошибка, даваемая предсказанием по соседним пикселям, может рассматриваться алгоритмом как присутствие стеганографического встраивания в анализируемый пиксель. Это может снижать точность стеганоанализа с помощью WS при наличии большой доли фона в изображении.
Для усовершенствования метода предсказания соседних пикселей в фоновых областях учтено, что фоновые области естественных изображений зачастую обладают характерными особенностями: структурой и градиентом. Даже фон, не имеющий явно выраженной структуры (например, рисунка, как на обоях или студийном фоне) имеет повторяющиеся шаблоны, возникающие за счёт особенностей матриц фотоаппаратов и алгоритмов обработки и сжатия изображений. Для учёта подобных особенностей решено применить матрицы соседства пикселей, основанные на цепях Маркова. Этот инструмент хорошо работает в задачах определения структуры и высокоуровневых закономерностей изменения данных, например, успешно использован в алгоритме стеганоанализа SPAM.
Пусть 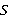 – анализируемое изображение, элемент пространственного домена которого определён как – анализируемое изображение, элемент пространственного домена которого определён как 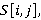 где где 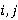 – координаты пикселя. n-цепь для пикселя пикселя – координаты пикселя. n-цепь для пикселя пикселя 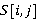 – кортеж – кортеж 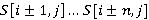 . Таким образом, n-цепь для пикселя представляет собой упорядоченное множество n соседних пикселей в определённом направлении. В зависимости от направления, такие цепи обозначаются nL, nR, nT и nB (соответственно, для направлений влево, вправо, вверх и вниз). . Таким образом, n-цепь для пикселя представляет собой упорядоченное множество n соседних пикселей в определённом направлении. В зависимости от направления, такие цепи обозначаются nL, nR, nT и nB (соответственно, для направлений влево, вправо, вверх и вниз).
Построив все 4 цепи для каждого пикселя изображения, для каждой уникальной цепи определяется количество пикселей, для которого она была построена. Самый часто встречающийся пиксель для данной цепи – предсказанный пиксель для данной цепи. Набор пар «цепь – предсказанный пиксель» – матрица соседства пикселей. Матрица строится на выборке изображений, результаты по отдельным изображениям суммируются.
При предсказании значения пикселя анализируемого изображения для него сроится n-цепь. Если такая n-цепь присутствует в матрице соседства пикселей, значение пикселя берётся из матрицы для данной цепи. Если цепь отсутствует, значение предсказывается по четырём соседним пикселям, как в оригинальном алгоритме WS.
Также вводятся пороги доверия матрице соседства пикселей. При построении матрицы на изображении без явно выраженных структурных паттернов матрица может давать неадекватные результаты, которые могут отрицательно влиять на точность анализа. Для выборки размером 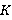 изображений для каждой цепи вводятся пороги доверия, изображений для каждой цепи вводятся пороги доверия, 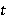 – относительный, и – относительный, и 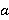 – абсолютный: – абсолютный:
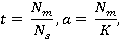
 где где 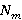 – количество появления предсказанного пикселя для данной цепи, – количество появления предсказанного пикселя для данной цепи, 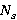 – количество появления данной цепи для всей выборки, – количество появления данной цепи для всей выборки, 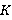 – количество изображений в выборке. – количество изображений в выборке.
Изменяя пороги доверия можно варьировать область применения матрицы соседства пикселей и анализа по соседним пикселям.
Как правило, матрицы соседства пикселей строятся на обучающей выборке, после чего применяются при анализе тестовой выборки (в частности, такой подход применяется в SPAM). В общем случае мы не располагаем обучающей выборкой, лишь изображением, предназначенным для анализа. Для применения метода в таком случае можно использовать само анализируемое изображение как обучающее. Это возможно при условии применения метода для малых величин полезной нагрузки. Учитывая, что в рассматриваемом случае максимально изменено 5% пикселей анализируемого изображения, этого недостаточно, чтобы внести значительную погрешность в закономерности расположения пикселей в фоновых областях.
Матрицу логично обучать и применять только на фоновых областях изображения. Для этого необходимо различать фоновые и нефоновые области. Выделение фона изображения можно провести на основе гистограммы изображения. Гистограмма строится для каждой цветовой плоскости отдельно. Далее среди гистограмм для каждой плоскости выбирается пик – значение пикселя, наиболее часто встречающееся в изображении. Определяется интервал фона B – максимальная разница между значением пикселя и значением пика, при котором пиксель считается принадлежащим фону. Фоновой областью считается та, для которой, по меньшей мере для двух из трёх цветовых плоскостей, разница между значением пикселя и пиком для данной цветовой плоскости не превышает B.
Таким образом, итоговый набор параметров усовершенствованного алгоритма включает в себя пороги доверия a, t и интервал фона B.
Усовершенствованная модель предсказания пикселя задаётся следующим уравнением:
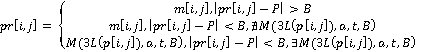
где,
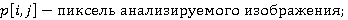
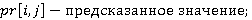
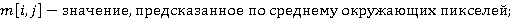
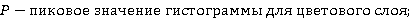
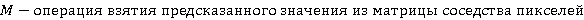 ; ;
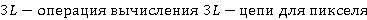 . .
Прочие детали реализации WS не меняются.
Результаты исследования
Для подтверждения предположения о зависимости точности стеганоанализа методом WS от доли фона в изображении проведён эксперимент. Немодифицированный алгоритм WS использован для классификации стеганографического встраивания в выборки HB и LB. Полезная нагрузка варьировалась от 1 до 10%. На рисунке 1 показан график зависимости вероятности верного обнаружения от вероятности положительного ложного срабатывания алгоритма для полезной нагрузки 4%. Кривые для других значений полезной нагрузки демонстрируют ту же тенденцию.
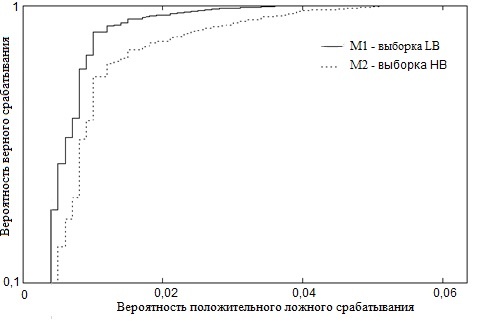
Рисунок 1. График зависимости вероятности верного обнаружения от вероятности положительного ложного срабатывания алгоритма WS для полезной нагрузки 4%
Из графика на рисунке 1 видно, что при анализе изображения с большой долей фона наблюдается завышение доли положительных ложных срабатываний, что соответствует предположению о непреднамеренной «имитации» стеганографического встраивания за счёт несовершенного метода предсказания пикселей изображения. Таким образом, метод нуждается в усовершенствовании. Кривые для других значений полезной нагрузки демонстрируют ту же тенденцию.
Для подтверждения влияния усовершенствования алгоритма на точность стеганоанализа введена средняя ошибка предсказания, определяемая как среднее значение разности предсказанного и реального значения для каждого пикселя анализируемого изображения.
Для подвыборок HB и LB имитировано встраивание с полезной нагрузкой 5%. Затем пиксели изображения предсказаны по соседним пикселям (метод оригинального алгоритма WS), и с использованием матриц соседства пикселей (усовершенствованный метод). В эксперименте использована 3L-цепь, пороги выставлены t=0.9, a=200. На рис. 2.1, 2.2 показаны графики распределения вероятностей средней ошибки предсказания пикселей изображения для выборок LB и HB соответственно. На графиках кривая PLAIN соответствует предсказанию по соседним пикселям. Кривая CHAIN соответствует предсказанию по матрице соседства пикселей.
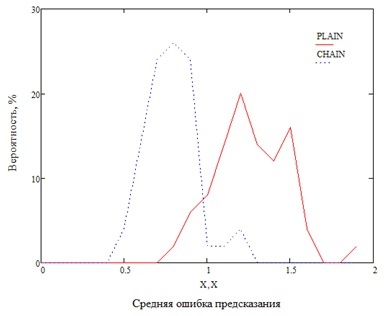
Рисунок 2.1. Распределение вероятности средней ошибки предсказания, коллекция LB
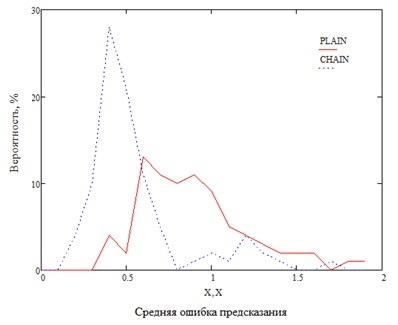
Рисунок 2.2. Распределение вероятности средней ошибки предсказания, коллекция HB
Из графиков на рис. 2.1, 2.2 видно, что средняя ошибка предсказания падает при анализе с использованием матриц соседства пикселей. Следует учитывать, что алгоритм WS округляет результат предсказания до целого по обычным правилам округления.
В таблице 1 приведены численные оценки средней ошибки для выборок LB и HB.
Таблица 1 – Средняя ошибка предсказания пикселей для выборок HB и LB
|
Метод / Коллекция
|
HB
|
LB
|
|
По среднему (PLAIN)
|
1.22
|
1.74
|
|
3L-цепь (CHAIN)
|
0.74
|
0.96
|
Таблицы 2, 3 содержат значение 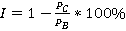 , где , где 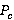 – точность стеганоанализа улучшенного алгоритма, – точность стеганоанализа улучшенного алгоритма, 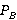 – точность стеганоанализа алгоритма, предложенного авторами (соответственно, для выборок HB и LB). – точность стеганоанализа алгоритма, предложенного авторами (соответственно, для выборок HB и LB).
Таблица 2 – Увеличение точности стеганоанализа на выборке HB
|
Полезная нагрузка / Разрешение
|
800x800
|
1500x1500
|
2400x2400
|
|
3%
|
10,1%
|
9,9%
|
9,5%
|
|
4%
|
14,0%
|
13,3%
|
9,8%
|
|
5%
|
17,5%
|
15,6%
|
11,0%
|
Таблица 3. Увеличение точности стеганоанализа на выборке LB
|
Полезная нагрузка / Разрешение
|
800x800
|
1500x1500
|
2400x2400
|
|
3%
|
1,1%
|
1,0%
|
1,0%
|
|
4%
|
3,3%
|
1,9%
|
1,7%
|
|
5%
|
4,8%
|
3,4%
|
2,9%
|
Обсуждение результатов
Оригинальный алгоритм WS, предложенный авторами, позволяет эффективно определять факт встраивания в LSB пространственного домена цифровых изображений. Средняя ошибка предсказания остаётся достаточно малой, в том числе при малых значениях полезной нагрузки. Тем не менее, при анализе изображений с большой долей однородного фона алгоритм теряет в точности за счёт особенностей модели предсказания пикселей анализируемого изображения.
Результаты, полученные для изображений с большой долей однородного фона, показывают практическую невозможность эффективного детектирования факта встраивания в подобные изображения из-за слишком высокой вероятности положительного ложного срабатывания: алгоритм ошибочно принимает чистые фоновые области за области, подвергшиеся стеганографическому встраиванию.
Игнорирование фоновых областей при анализе изображений делает алгоритм уязвимым, позволяя встраивать стеганопосылку именно в область однородного фона, оставаясь незамеченным для стеганоанализатора.
Предложенное в настоящей работе усовершенствование алгоритма изменяет модель предсказания значений пикселей, делая её более эффективной на фоновых областях изображений, что уменьшает вероятность ложного положительного срабатывания при анализе изображений с большой долей однородного фона.
Заключение
В работе проведено исследование эффективности стеганоанализа методом Weighted Stego неподвижных цифровых изображений со встраиванием в пространственный домен в зависимости от доли однородного фона в анализируемом изображении. Результаты исследования показали снижение точности анализа с повышением доли однородного фона. Это затрудняет эффективность противодействия скрытым каналам передачи информации на основе стагенографии методами, основанными на использовании алгоритма WS. В работе приведён метод усовершенствования модели предсказания пикселей при анализе, позволяющий нивелировать снижение точности при анализе областей однородного фона изображений. Метод не снижает точность анализа изображений с малой долей однородного фона. Увеличение точности стеганоанализа в процентном отношении для изображений с большой долей однородного фона составляет 10-15%.
Необходимо дальнейшее совершенствование модели предсказания пикселей алгоритма WS в различных областях анализируемого изображения. Также возможно совершенствование методов распознавания различных областей изображения для адаптивного применения различных моделей предсказания, эффективных в областях со специфичными характеристиками.
References
1. Gribunin V.G., Okov I.N., Turintsev I.V. Tsifrovaya steganografiya. M.:Solon-Press. 2016. 262 s.
2. Steganography: A Powerful Tool for Terrorists and Corporate Spies // Stratfor [Elektronnyi resurs]. Rezhim dostupa: https://www.stratfor.com/analysis/steganography-powerful-tool-terrorists-and-corporate-spies, svobodnyi. Yaz. angl. (data obrashcheniya 22.08.2017).
3. Gayathri C., Kalpana V. Study on image steganography techniques // International Journal of Engineering and Technology (IJET). 2013. V. 5. P. 572–577.
4. Prokhozhev N., Mikhailichenko O., Sivachev A., Bashmakov D., Korobeynikov A.G. Passive Steganalysis Evaluation: Reliabilities of Modern Quantitative Steganalysis Algorithms // Advances in Intelligent Systems and Computing. 2016. V. 451. R. 89–94. doi:10.1007/978-3-319-33816-3_9
5. Prokhozhev N.N., Mikhailichenko O.V., Bashmakov D.A., Sivachev A.V., Korobeinikov A.G. Issledovanie effektivnosti primeneniya statisticheskikh algoritmov kolichestvennogo steganoanaliza v zadache detektirovaniya skrytykh kanalov peredachi informatsii // Programmnye sistemy i vychislitel'nye metody. 2015. № 3. S. 281–292. doi: 10.7256/2305-6061.2015.3.17233
6. Ker, Andrew. (2007). A Weighted Stego Image Detector for Sequential LSB Replacement. Proceedings-IAS 2007 3rd Internationl Symposium on Information Assurance and Security. 453-456. 10.1109/IAS.2007.71.
7. Ker, Andrew & B ohme, Rainer. (2008). Revisiting Weighted Stego-Image Steganalysis. Electronic Imaging 2008, International Society for Optics and Photonics. 6819. . 10.1117/12.766820.
8. BOWS2 the 10 000 original images [Elektronnyi resurs]. Rezhim dostupa: http://bows2.ec-lille.fr/, svobodnyi. Yaz. angl. (data obrashcheniya 12.04.2017).
9. Pevny T., Bas P., Fredrich J. Steganalysis by subtractive pixel adjacency matrix // Transactions on Information Forensics and Security. 2010. V. 5 N 2. P. 215–224.
Link to this article
You can simply select and copy link from below text field.
|
|





