|
DOI: 10.7256/2306-4196.2015.2.14349
Received:
30-01-2015
Published:
17-04-2015
Abstract:
The purpose of the study is in increasing the protection of nodes when accessing resources of an outside network. The objects of the study are the schemes of secure access from corporate network nodes to the information in the external network via "Direct connection" and "Connecting node". The study of these schemes is carried in terms of improving the security of the terminal node of corporate network, convenience and quality of organizing access of this node to the external network resources, as well as the complexity of the implementation of these schemes. In addition, the paper considers the possibility of protecting corporate network nodes from DDoS-attacks. The basis of the research is in the method of comparative analysis, which allows to reveal the advantages and disadvantages of each of the schemes. Based on the results it can be concluded that the scheme of "Direct connection" should be used in the following cases. Firstly, when it is impossible to make significant changes to the existing network architecture. Secondly, when the organization has limited financial resources. And thirdly, if it is necessary to work with external network resources in real time. Scheme "Connecting node", in contrast, requires (radical) rebuilding of network architecture and significant financial costs, but allows a much greater extent than the scheme of "direct connection", protecting an organization from the threats from the external network.
Keywords:
encryption, network organization, firewalls, unauthorized access, information security, information technology, information protection, protected storage, monitoring of network traffic, access control
This article written in Russian. You can find original text of the article here
.
Введение В современных сложных вычислительных системах, подключенных как к корпоративным сетям, так и к сетям общего пользования, остро стоит проблема защищенности информации. Несанкционированный доступ, отказ узла в обслуживании, потеря информации, а также нарушение режима секретности на узле может привести к значительным экономическим и иным потерям.
Угроза атаки на вычислительные устройства может исходить как извне – посредством удаленных сетевых атак, так и изнутри подзащитной сети – за счет различных закладочных программных или аппаратных средств. Для устранения проблем защиты информации могут быть применены меры и использованы средства обеспечения информационной безопасности, расположенные на различных уровнях сети.
Принципы организации защищенного подключения корпоративной сети к сетям общего пользования, являются одними из важнейших элементов обеспечения информационной защищенности, существенно влияющими на безопасность и надежность работы в сети. Эффективные методы обеспечения безопасности, как правило, требуют значительных материальных затрат на них. Подходы, позволяющие осуществить безопасное подключение узла корпоративной сети к ресурсам внешней сети обычно:
- разрабатываются для конкретной корпоративной сети и, таким образом, не являются универсальными;
- требуют создания совершенно новой архитектуры сети или полной реорганизации прежней;
- обеспечивают лишь точечную (сегментную), а не комплексную защиту сети;
- могут быть неприменимы в сетях государственных учреждений и корпоративных сетях, в которых ведется обработка информации ограниченного доступа.
В данной работе предложено два подхода к обеспечению безопасного доступа узлов сети к слабо защищенным участкам внутри корпоративной сети или в саму корпоративную сеть, в том числе в сетях общего пользования. При этом учитываются все требования, изложенные руководящих документов по безопасности. Постановка задачи исследования Каждый из предлагаемых подходов ориентирован на повышение степени защищенности устройств сети и безопасности доступа к слабо защищенным и/или неподконтрольным участкам сети. Оба подхода направлены на: снижение риска
DDoS-атак, защиту устройств от вредоносного программного обеспечения, устранение возможности несанкционированного доступа к узлу сети и на устранение угрозы прослушивания канала передачи данных.
Рассматриваемые подходы базируются на стандартной сетевой схеме доступа узла к внешней сети: узел «Внутренней (локальной) сети» ‑ маршрутизатор ‑ устройства «Внешней сети (Интернет)». Это позволяет минимизировать степень возможной реорганизации уже имеющейся корпоративной сети. Данная общая схема доступа изображена на Рисунке 1.
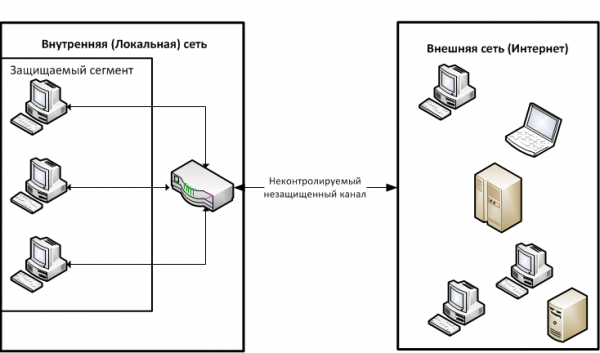
Рисунок 1. Общая схема доступа узла во внешнюю сеть
В стандартной схеме доступа оконечного узла корпоративной сети к узлам внешней сети защита этого узла основана на встроенных в него средствах. Это средство антивирусной защиты и стандартный межсетевой экран, который присутствует в системе. Также в стандартной схеме имеется средство фильтрации поступающих из внешней сети пакетов, находящееся на маршрутизаторе.
Для критически важных систем указанных средств защиты недостаточно. В связи с этим предлагаются две новые схемы безопасного подключения:
- схема «Прямое соединение», позволяющая быстро, с минимальными финансовыми затратами и практически неизменной архитектурой сети организовать безопасный доступ оконечного узла во внешнюю сеть;
- схема «Связующий узел», использующая дополнительное промежуточное вычислительное устройство для соединения внутренней и внешней сетей, что позволяет повысить уровень безопасного доступа к ресурсам внешней сети.
Схема «Прямое соединение» позволяет быстро и недорого организовать безопасный доступ оконечного узла к узлам внешней сети, в то время как схема «Связующий узел» обеспечивает повышенный уровень безопасности при доступе к ресурсам внешней сети. Схема «Прямое соединение» Использование схемы «Прямого соединения» предполагает минимальные изменения в архитектуре корпоративной сети, а также минимальные дополнительные финансовые затраты на ее создание. Структура схемы «Прямое соединение» представлена на Рисунке 2.
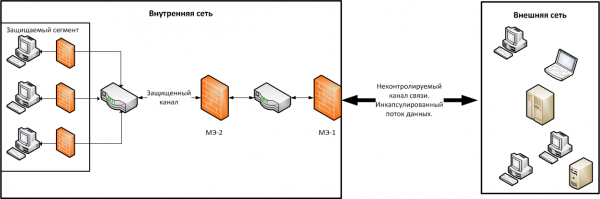
Рисунок 2. Схема «Прямое соединение»
В предлагаемой схеме на входе во внутреннюю сеть (перед маршрутизатором) устанавливается межсетевой экран (МЭ) с фильтрацией пакетов (МЭ-1) для фильтрации поступающих на вход данных от нежелательных сообщений (спама) [4] и снижения риска DDoS-атак. Чаще всего указанный выше маршрутизатор, может нести на себе функционал МЭ с фильтрацией пакетов, однако эффективнее использовать раздельно маршрутизатор и МЭ.
После маршрутизатора требуется установить МЭ с адаптивной проверкой пакетов (МЭ-2) для более глубокого анализа содержимого пакета [1]. С учетом того, что на вход МЭ-2 будет поступать меньше данных, чем на вход МЭ-1, нагрузка на данный МЭ будет меньше и, следовательно, производительность самой сети выше.
После прохождения МЭ-2 потенциально «чистые» данные должны поступить на адресуемый оконечный узел. На данном узле должно быть установлено антивирусное средство (АВС) со встроенным в него МЭ [1]. Это позволит исключить (в пределах возможностей антивирусной базы) угрозу того, что в полученных данных имелась какая-либо зловредная программа или же исполняемый код, а также угрозу того, что приложения на данном узле будут вести несанкционированную деятельность в сети.
На оконечном узле должна быть установлена система защиты от несанкционированного доступа (НСД). Это позволит защитить узел от получения нарушителем несанкционированного управления над узлом (в том числе, если он является инсайдером). [3]
Для безопасного хранения на узле данных ограниченного доступа требуется также организовать защищенное хранилище данных. Его реализация может быть выполнена либо при помощи криптографических средств, либо с использованием средств виртуальной рабочей среды. Выбор того или иного варианта напрямую зависит от того, какого рода данные хранятся на указанном узле и, как следствие, какого уровня защита для них требуется.
Наконец, требуется обеспечить защищенный канал передачи данных, чтобы злоумышленник не мог повлиять на состояние данных курсирующих в канале. Для этого следует применить процедуру шифрования трафика. Криптостойкость инкапсулированных данных будет зависеть от выбранного в процессе проектирования сети криптоалгоритма и алгоритма электронной цифровой подписи (ЭЦП). По умолчанию ими должны стать алгоритмы ГОСТ-28147-89 и ГОСТ Р 34.10-2012 для того, чтобы схема могла отвечать заявленным требованиям, указанным в руководящих документах (РД).
Для общей защиты сети от DDoS-атак, потери и уничтожения данных и других аналогичных угроз критически важные узлы (как в плане сетевой архитектуры, так и в плане хранящихся на них данных) должны быть резервированы, а для данных хранящихся на них, созданы резервные копии. При хорошем уровне распределения нагрузки в сети между узлами процедура резервирования может вовсе не понадобиться. Схема «Связующий узел» Данная схема представляет собой расширенную элементом «связующий узел» схему «Прямое соединение». Наличие «связующего узла» позволяет существенно повысить защиту от угроз в сети.
Схема «Связующий узел» содержит почти все описанные в схеме «Прямое соединение» элементы, которые играют в ней ту же самую роль. Однако в данной схеме вместо МЭ с адаптивной проверкой пакетов присутствует элемент «связующий узел». В состав этого узла входят две составляющие – МЭ и дополнительный вычислительный узел. Структура сети с использованием схемы «Связующий узел» представлена на Рисунке 3.
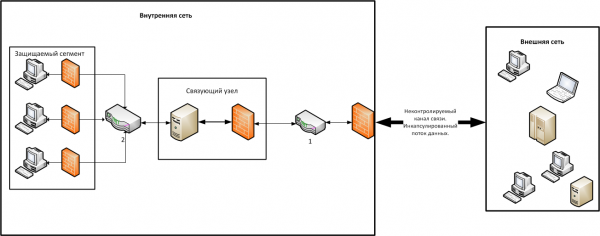
Рисунок 3. Схема «Связующий узел»
МЭ в составе «связующего узла» является МЭ с адаптивной проверкой пакетов. Он устанавливается на входе в «связующий узел» и тщательно анализирует поступающих в сеть пакеты и подтверждения, что данный пакет предназначен строго для данного «связующего узла» (при условии, что их более одного).
Вычислительный узел предназначен для сохранения и предобработки поступающей из внешней сети информации. Так же как и оконечные узлы внутренней сети, данный узел должен содержать: АВС со встроенным в него МЭ; систему защиты от НСД и защищенное хранилище. После того как данные, попавшие на узел, будут проверены на отсутствие в них каких-либо угроз для оконечных вычислительных устройств, они становятся доступными для узлов внутренней сети.
В системе имеется потенциальная угроза того, что злоумышленник может перехватить или повлиять на состояние данных, курсирующих в канале в связи с чем требуется обеспечить защищенный канал передачи данных между узлами внешней и внутренней сетей. В идеальном случае шифрование трафика должно быть на всем пути от оконечных узлов до внешней сети. Однако при должном уровне физической, технической и организационной безопасности на предприятии можно ограничиться лишь созданием защищенного канала передачи информации от «связующего узла» и до узлов внешней сети.
После применения вышеописанных мер соединение всех оконечных узлов корпоративной сети с внешней сетью производится строго через «связующий узел» (или их набор). В результате чего, оконечные узлы внутренней сети имеют возможность безопасного получения информации из внешней сети, только обратившись с запросом на «связующий узел», а не напрямую, делая запросы к вычислительным устройствам внешней сети. Благодаря этому снижается угроза безопасности сети.
Взаимодействие между разными сегментами внутренней сети (имеющими различную степень защищенности или находящимися на удалении друг от друга) происходит через подключенные к ним разных «связующих узлов». Тем самым передача информации между этими сегментами производится так же, как и передача информации между оконечным узлом внутренней сети и внешней сетью. Сравнительный анализ предлагаемых схем Необходимо сравнить эффективность внедрения и использования описанных выше схем. При внедрении «Прямого соединения» не потребуется кардинального изменения архитектуры уже существующей корпоративной сети, а также наличия каких-либо специфических аппаратных и программных средств. Напротив, при внедрении второй из описываемых схем нужен пересмотр политики взаимодействия узлов корпоративной сети между собой, создание более сложной процедуры доступа оконечного узла во внешнюю сеть и использование в сети дополнительных вычислительных узлов [7-8]. Тем самым, внедрение схемы «Прямое соединение» приводит к меньшим материальным и временным затратам при обеспечении безопасности оконечных узлов сети.
В то же время схема «Связующий узел» обеспечивает большую безопасность для корпоративной сети, чем схема «Прямое соединение», поскольку при ее применении:
- снижается нагрузка на оконечные узлы внутренней сети в связи с тем, что основная обработка и проверка поступающих из внешней сети данных производится на «связующих узлах»;
- всю информацию «извне» оконечные узлы получают не из внешней сети, а со «связующих узлов», после того как она проверена на наличие в ней каких-либо угроз безопасности. Следовательно, снижается риск заражения, повреждения или несанкционированного доступа к оконечному узлу.
Однако из-за наличия дополнительного узла (или нескольких узлов) и затрачиваемого времени «связующим узлом» на проверку поступающих данных возникает существенная задержка в получении этих данных оконечным узлом. Как результат, скорость обмена данными между оконечным узлом и внешней сетью при реализации схемы «Связующий узел» становится ниже, чем при использовании схемы «Прямое соединение». Данную проблему можно устранить путем кэширования данных на «связующих узлах». Однако это решение не поможет в случае необходимости получения данных из внешней сети в режиме реального времени.
Сравнивая эти две схемы по возможностям снижения риска DDoS-атак, можно сказать, что оконечные узлы в схеме «Прямое соединение» более подвержены DDoS-атакам, чем в схеме «Связующий узел». Так как, между оконечным узлом и злоумышленником, в схеме «Прямое соединение», находятся лишь два аппаратных МЭ (адаптивный и с фильтрацией пакетов) и МЭ встроенный в АВС. Иными словами, снижение возможной нагрузки на оконечный узел возможно лишь путем резервирования аппаратных МЭ [1,10-11] или путем выделения запредельно больших вычислительных мощностей оконечному узлу (что в принципе является невозможным и нецелесообразным). Реализация первого варианта (резервирование МЭ) не является нерешаемой задачей, хотя и предполагает довольно большие материальные затраты, а также некоторое усложнение сетевой инфраструктуры.
Схема «Связующий узел», напротив, позволяет существенно снизить угрозу DDoS-атак благодаря наличию дополнительных узлов, предобрабатывающих поступающую на них информацию. Некоторые из этих узлов (в зависимости от сегмента сети, к которому они подсоединены) можно по желанию дублировать. Однако резервирование приводит к повышению стоимости данного решения и созданию более сложной сетевой инфраструктуры.
Как указывалось ранее, при рассмотрении вопроса о безопасном доступе к внешним ресурсам схема «Связующий узел» позволяет снизить нагрузку на оконечные узлы внутренней сети. Как следствие, от этих узлов не будет требоваться огромных вычислительных мощностей для обработки данных, поступающих к ним на вход. Это очень важно в тех случаях, когда на данных оконечных узлах не предусмотрена какая-либо работа, требующая большого объема вычислительных ресурсов. В то же время следует иметь в виду, что «связующие узлы» становятся критически важными элементами в сетевой инфраструктуре, а организация их надежной и безотказной работы – первоочередной задачей [5-6].
Обе вышеописанные схемы организации доступа оконечного узла корпоративной сети к ресурсам внешней сети позволяют обеспечить выполнение всех обязательных требований, указанных в РД, в зависимости от проведенной классификации автоматизированных систем (АС) в сети. Однако применение схемы «Связующий узел» потребуется использование на «связующих узлах» программных и аппаратных средств обеспечивающих защиту при наивысшем уровне секретности информации, курсирующей в данном сегменте сети и, как следствие, обрабатывающейся на данном узле. Заключение В статье предложены и проанализированы две схемы организации безопасного доступа узлами корпоративной сети, к информации расположенной во внешней сети. Каждая из схем имеет ряд определенных достоинств и недостатков.
Показано, что схема «Прямое соединение" предпочтительно использовать: когда нет возможности существенного изменения существующей архитектуры корпоративной сети; нужно организовать такой доступ с наименьшими финансовыми затратами; требуется работа с ресурсами внешней сети в реальном времени.
Схема «Связующий узел" требует значительного усложнения имеющейся архитектуры сети, больших финансовых затрат и усложняет процесс работы с ресурсами из внешней сети в реальном времени, но в результате значительно повышает безопасность доступа к внешней сети и защищенность от угроз DDoS-атак.
Таким образом, каждая из показанных схем построения корпоративной сети позволяет достигнуть требуемого уровня безопасности в рамках финансовых и архитектурных возможностей организации. Для более качественного и обоснованного выбора применимости той или иной схемы на практике требуется решение задач выработки критериев моделирования и оптимизации. [9-12]
References
1. Ingham Kenneth, Forrest Stephanie. A History and Survey of Network Firewalls // University of New Mexico. – 2002.
2. Gatchin Yu.A. Matematicheskie modeli otsenki infrastruktury sistemy zashchity informatsii na predpriyatii / Gatchin Yu.A., Zharinov I.O., Korobeinikov A.G // Nauchno-tekhnicheskii vestnik informatsionnykh tekhnologii, mekhaniki i optiki. 2012. № 2 (78). S. 92-95
3. Korobeinikov A.G. Matematicheskaya model' rascheta veroyatnosti nesanktsionirovannogo fizicheskogo proniknoveniya na ob''ekt informatizatsii / Korobeinikov A.G., Pirozhnikova O.I. // Programmnye sistemy i vychislitel'nye metody. 2014. № 2. S. 160-165.
4. Korobeinikov A.G. Algoritm klassifikatsii informatsii dlya resheniya zadachi fil'tratsii nezhelatel'nykh soobshchenii / Korobeinikov A.G., Sidorkina I.G., Blinov S.Yu., Leiman A.V. // Programmnye sistemy i vychislitel'nye metody. – 2012. № 1. S. 89-95.
5. Bogatyrev V.A. K raspredeleniyu funktsional'nykh resursov v otkazoustoichivykh mnogomashinnykh vychislitel'nykh sistemakh // Pribory i sistemy. Upravlenie, kontrol', diagnostika. – 2001. № 12. S. 1-5
6. Bibikov S.V. Otsenka funktsional'noi bezopasnosti dublirovannykh vychislitel'nykh sistem / Bibikov S.V., Bogatyrev V.A. // Nauchno-tekhnicheskii vestnik informatsionnykh tekhnologii, mekhaniki i optiki – 2012. – № 2 (78). – S. 146-147
7. Bogatyrev V.A. Nadezhnost' klasternykh vychislitel'nykh sistem s dublirovannymi svyazyami serverov i ustroistv khraneniya / Bogatyrev V.A., Bogatyrev S.V., Bogatyrev A.V. // Informatsionnye tekhnologii. – 2013. № 2. S. 27-32.
8. Bogatyrev V.A. Optimizatsiya intervalov proverki informatsionnoi bezopasnosti sistem / Bogatyrev V.A., Bogatyrev A.V., Bogatyrev S.V. // Nauchno-tekhnicheskii vestnik informatsionnykh tekhnologii, mekhaniki i optiki. 2014. № 5 (93). S. 119-125.
9. Bogatyrev V.A., i dr. Optimizatsiya raspredeleniya zaprosov mezhdu klasterami otkazoustoichivoi vychislitel'noi sistemy // Nauchno-tekhnicheskii vestnik informatsionnykh tekhnologii, mekhaniki i optiki. – 2013. № 3. S. 77-82
10. Bogatyrev V.A. i dr Optimizatsiya vychislitel'nykh sistem s ob''edineniem mezhsetevykh ekranov v otkazoustoichivye klastery // Nauchno-tekhnicheskii vestnik informatsionnykh tekhnologii, mekhaniki i optiki. – 2011. № 6 (76). S. 140-142.
11. Bogatyrev V.A. Otsenka i vybor otkazoustoichivykh konfiguratsii mezhsetevykh ekranov / Bogatyrev V.A., Fokin S.B., Popova M.V. // Nauchno-tekhnicheskii vestnik informatsionnykh tekhnologii, mekhaniki i optiki. 2011. № 3 (73). S. 139-140.
12. Bogatyrev V.A. Kriterii optimal'nosti mnogourovnevykh otkazoustoichivykh komp'yuternykh sistem / Bogatyrev V.A. Bogatyrev S.V. // Nauchno-tekhnicheskii vestnik ITMO. 2009. № 5 (63). C. 92-97.
13. Zaguzov G.V. Administrativno-pravovye sredstva obespecheniya informatsionnoi bezopasnosti i zashchity informatsii v Rossiiskoi Federatsii // Administrativnoe i munitsipal'noe pravo. - 2010. - 5. - C. 44 - 47.
Link to this article
You can simply select and copy link from below text field.
|





